Design and Analysis of Algorithms 演算法設計與分析. Lecture 9 November 19, 2014 洪國寶
|
|
|
- Raymond Lee
- 5 years ago
- Views:
Transcription
1 Design and Analysis of Algorithms 演算法設計與分析 Lecture 9 November 19, 2014 洪國寶 1
2 Outline Advanced data structures Binary heaps(review) Binomial heaps Fibonacci heaps Data structures for disjoint sets 2
3 Mergeable Heaps Support the following operations. MAKE-HEAP() creates and returns a new heap containing no elements. INSERT(H, x) inserts node x, whose key field has already been filled in, into heap H. MINIMUM(H) returns a pointer to the node in heap H whose key is minimum. EXTRACT-MIN(H) deletes the node from heap H whose key is minimum, returning a pointer to the node. UNION(Hl, H2) creates and returns a new heap that contains all the nodes of heaps H1 and H2. Heaps H1 and H2 are "destroyed" by this operation. DECREASE-KEY(H, x, k) assigns to node x within heap H the new key value k, which is assumed to be no greater than its current key value. DELETE(H, x) deletes node x from heap H. 3
4 Review: Binary Heap Binary heap. Almost complete binary tree. filled on all levels, except last, where filled from left to right Min-heap ordered. every child greater than (or equal to) parent
5 Properties. Review: Binary Heap Min element is in root. Heap with N elements has height = log 2 N N = 14 Height =
6 Review: Binary Heaps Implementing binary heaps. Use an array: no need for explicit parent or child pointers. Parent(i) = i/2 Left(i) = 2i Right(i) = 2i
7 Review: Inserting into a binary heap There are two constraints that must be met an almost complete tree the heap-order property We increase the size of the heap to make a hole in the next spot It the item can be legally inserted in the hole, then do so, otherwise move the parent value down and try again 7
8 Review: Binary Heap Decrease Key Decrease key of element x to k. Bubble up until it's heap ordered. O(log N) operations
9 Review: Binary Heap Extract-Min Delete minimum element from heap. Exchange root with rightmost leaf. Bubble root down until it's heap ordered. (heapify) power struggle principle: better subordinate is promoted
10 Union. Binary Heap: Union Combine two binary heaps H 1 and H 2 into a single heap. No easy solution. (N) operations apparently required H 1 H
11 Priority Queues Operation make-heap insert minimum extract-min union decrease-key delete Linked List 1 1 N N 1 1 N Mergeable Heaps Binary 1 Binomial 1 Fibonacci * 1 log N 1 log N N log N log N log N log N log N log N log N log N 1 1 log N 1 1 log N Coming up next 11
12 Outline Advanced data structures Binary heaps(review) Binomial heaps Fibonacci heaps Data structures for disjoint sets 12
13 Binomial Trees Binomial tree. Recursive definition: B 0 B k B k-1 B k-1 B 0 B 1 B 2 B 3 B 4 13
14 Binomial Trees Useful properties of order k binomial tree B k. Number of nodes = 2 k. Height = k. Degree of root = k. Deleting root yields binomial trees B k-1,, B 0. Proof. By induction on k. B k B k+1 B 1 B 2 B 0 B 0 B 1 B 2 B 3 B 4 14
15 Binomial Trees A property useful for naming the data structure. k B k has i nodes at depth i. depth 0 depth depth 2 depth 3 depth 4 B 4 15
16 Binomial Heap Binomial heap. Vuillemin, Sequence of binomial trees that satisfy binomial heap property. each tree is min-heap ordered 0 or 1 binomial tree of order k B 4 B 1 B 0 16
17 17
18 Binomial Heap: Properties Properties of N-node binomial heap. Min key contained in root of B 0, B 1,..., B k. (root list) Contains binomial tree B i iff b i = 1 where b n b 2 b 1 b 0 is binary representation of N. At most log 2 N + 1 binomial trees. Height log 2 N N = 19 # trees = 3 height = 4 binary = B 4 B 1 B 0 18
19 Binomial Heap Operation 1 Create a binomial heap make-binomial-heap( ) H allocate-node( ) head[h] nil return H Running time = O(1) 19
20 Minimum Binomial Heap Operation 2 Running time = O(log n) 20
21 Binomial Heap Operation 3: Union Create heap H that is union of heaps H' and H''. "Mergeable heaps." Easy if H' and H'' are each order k binomial trees. connect roots of H' and H'' choose smaller key to be root of H (Binomial-link) H' H'' 21
22 Binomial Heap: Union 22
23 Binomial Heap: Union =
24 Binomial Heap: Union
25 12 Binomial Heap: Union
26
27
28
29
30 30
31 31
32 Binomial Heap Operation 3: Union Create heap H that is union of heaps H' and H''. Analogous to binary addition. Running time = O(log N) Proportional to number of trees in root lists 2( log 2 N + 1) =
33 Binomial Heap Operation 3: Union Running time = O(log N) Binomial-heap-merge: merge two sorted linked lists Proportional to number of trees in root lists 2( log 2 N + 1). while loop (line 9- line 21) Each iteration executes one binomial-link O(1) Proportional to number of trees in root lists 2( log 2 N + 1) =
34 Binomial Heap: Extract-min Delete node with minimum key in binomial heap H. Find root x with min key in root list of H, and delete H' broken binomial trees H Union(H', H) Running time. O(log N) H H' 34
35 35
36 36
37 Binomial Heap: Extract-min Running time. O(log N) 1. Find the root with minimum key from root list: O(# of trees) = O(log n) 2. Make-binomial-heap: O(1) 3. Reverse the order of the linked list of x s children: O(degree(x)) = O(log n) 4. Binomial-heap-union: O(log n) H H' 37
38 Binomial Heap Operation 5: Insert Insert a new node x into binomial heap H. H' MakeHeap(x) H Union(H', H) Running time. O(log N) x H H'
39 Binomial Heap Operation 5: Insert 39
40 Binomial Heap: Sequence of Inserts Insert a new node x into binomial heap H. If N =...0, then only 1 steps. If N =...01, then only 2 steps. If N =...011, then only 3 steps. If N = , then only 4 steps x 37 Inserting 1 item can take (log N) time. If N = , then log 2 N steps But, inserting sequence of N items takes O(N) time! (N/2)(1) + (N/4)(2) + (N/8)(3) N Amortized analysis. Basis for getting most operations down to constant time. N n 1 n n N 2 N 2 1 N 1 40
41 Binomial Heap Operation 6: Decrease Key Decrease key of node x in binomial heap H. Suppose x is in binomial tree B k. Bubble node x up the tree if x is too small. Running time. O(log N) Proportional to depth of node x log 2 N depth = H x
42 42
43 43
44 Binomial Heap Operation 7: Delete Delete node x in binomial heap H. Decrease key of x to -. Delete min. Running time. O(log N) 44
45 Binomial Heap Operation 7: Delete 45
46 Priority Queues Operation make-heap insert minimum extract-min union decrease-key delete Linked List 1 1 N N 1 1 N Mergeable Heaps Binary 1 Binomial 1 Fibonacci * 1 log N 1 log N N log N log N log N log N log N log N log N log N 1 1 log N 1 1 log N Coming up next 46
47 Outline Advanced data structures Binary heaps(review) Binomial heaps Fibonacci heaps Data structures for disjoint sets 47
48 Fibonacci Heaps Fibonacci heap history. Fredman and Tarjan (1986) Ingenious data structure and analysis. Original motivation: O(E + V log V) shortest path algorithm. also led to faster algorithms for MST (Lecture 11), weighted bipartite matching 48
49 Fibonacci Heaps Fibonacci heap intuition. Similar to binomial heaps, but less structured. Decrease-key and union run in O(1) time. "Lazy" unions and inserts We do not attempt to consolidate trees in a Fibonacci heap when we unite two heaps or insert a new node. 49
50 Fibonacci Heaps: Structure Fibonacci heap. Set of min-heap ordered trees. min marked H
51 Fibonacci Heaps: Implementation Implementation. Represent trees using left-child, right sibling pointers and circular, doubly linked list. can quickly splice off subtrees Roots of trees connected with circular doubly linked list. fast union min[h]: Pointer to root of tree with minimum element. fast find-min min H
52 Root list Child list 52
53 Fibonacci Heaps: Potential Function Key quantities. degree[x] = degree of node x. mark[x] = mark of node x (black or gray). t(h) = # trees. m(h)= # marked nodes. (H)= t(h) + 2m(H) = potential function. t(h) = 5, m(h) = 3 (H) = 11 degree = 3 min H
54 Fibonacci Heap Operation 1: Create Create a Fibonacci heap make-fib-heap( ) H allocate-node( ) n[h] 0 min[h] nil return H Running time Amortized cost = actual cost = O(1) 54
55 Fibonacci Heap Operation 2: Minimum Minimum Fib-heap-minimum(H ) return min[h] Running time Amortized cost = actual cost = O(1) 55
56 Fibonacci Heap Operation 3: Insert Insert. Create a new singleton tree. Add to left of min pointer. Update min pointer. Update n[h] Insert min H
57 Fibonacci Heap Operation 3: Insert Insert. Create a new singleton tree. Add to left of min pointer. Update min pointer. Update n[h] Insert 21 min H
58 Fibonacci Heap Operation 3: Insert Running time. O(1) amortized Actual cost = O(1). Change in potential = +1. Amortized cost = O(1). Insert 21 min H
59 Insert. Create a new singleton tree. Add to left of min pointer. Update min pointer. Update n[h] 59
60 60
61 Fibonacci Heap Operation 4: Union Union. Concatenate two Fibonacci heaps. Root lists are circular, doubly linked lists. min min H' H''
62 Fibonacci Heap Operation 4: Union Running time. O(1) amortized Actual cost = O(1). Change in potential = 0. Amortized cost = O(1). min H' H''
63 63
64 Fibonacci Heap Operation 5: Extract Extract min. Min Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree. min
65 Fibonacci Heap Operation 5: Extract Extract min. Min Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree. min current
66 Fibonacci Heap Operation 5: Extract Extract min. Min Delete min and concatenate its children into root list. Consolidate trees so that 0 no 1 two 2 3 roots have same degree. min current
67 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree. current min
68 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current
69 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current Merge 17 and 23 trees. 69
70 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current Merge 7 and 17 trees. 70
71 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current Merge 7 and 24 trees. 71
72 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current
73 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current
74 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current
75 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current Merge 41 and 18 trees. 75
76 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current
77 Fibonacci Heap Operation 5: Extract Min Extract min. Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree min current
78 Fibonacci Heap Operation 5: Extract Extract min. Min Delete min and concatenate its children into root list. Consolidate trees so that no two roots have same degree. min Stop. 78
79 Delete min and concatenate its children into root list. 79
80 80
81 Running time = O(1) 81
82 82
83 Running time = O( D(n) + T(consolidate) ) where D(n): max degree of any node in n-node Fibonacci heap Note the number of nodes in root list after step 6 is O(D(n) + t(h)). 83
84 T(consolidate) simple analysis: O(D(n) + (t(h)+d(n)) D(n) + D(n)) = O( D(n) 2 + t(h)d(n) ) O(D(n)) O( t(h)+d(n) ) O( D(n) ) O(D(n)) 84
85 T(consolidate) tight analysis: the running time from step 3 to step 13 is O(# Fib-Heap-Link exec.) = O(# nodes in the root list) = O( D(n) + t(h) ) 85
86 Fibonacci Heap Extract Min Analysis Notation. D(n) = max degree of any node in Fibonacci heap with n nodes. t(h) = # trees in heap H. (H)= t(h) + 2m(H). Actual cost. O(D(n) + t(h)) O(D(n)) work adding min's children into root list and updating min. at most D(n) children of min node O(D(n) + t(h)) work consolidating trees. work is proportional to size of root list since number of roots decreases by one after each merging D(n) + t(h) - 1 root nodes at beginning of consolidation 86
87 Fibonacci Heap Extract Min Analysis Notation. D(n) = max degree of any node in Fibonacci heap with n nodes. t(h) = # trees in heap H. (H)= t(h) + 2m(H). Actual cost. O(D(n) + t(h)) Amortized cost. O(D(n)) t(h') D(n) + 1 since no two trees have same degree. (H) D(n) t(h). 87
88 Fibonacci Heap Extract Min Analysis Is amortized cost of O(D(n)) good? Yes, if only Insert, Extract-min, and Union operations supported. in this case, Fibonacci heap contains only binomial trees since we only merge trees of equal root degree this implies D(n) log 2 N Yes, if we support Decrease-key in clever way. we'll show that D(n) log N, where is golden ratio 2 = 1 + = (1 + 5) / 2 =
89 Fibonacci Heap Operation 6: Decrease Key Decrease key of element x to k. Case 0: min-heap property not violated. decrease key of x to k change heap min pointer if necessary min Decrease 46 to
90 Fibonacci Heap Operation 6 : Decrease Key Decrease key of element x to k. Case 1: parent of x is unmarked. decrease key of x to k cut off link between x and its parent mark parent add tree rooted at x to root list, updating min heap min pointer Decrease 45 to
91 Fibonacci Heap Operation 6 : Decrease Key Decrease key of element x to k. Case 1: parent of x is unmarked. decrease key of x to k cut off link between x and its parent mark parent add tree rooted at x to root list, updating min heap min pointer Decrease 45 to
92 Fibonacci Heap Operation 6 : Decrease Key Decrease key of element x to k. Case 1: parent of x is unmarked. decrease key of x to k cut off link between x and its parent mark parent 15 add tree rooted at x to root list, updating min heap min pointer Decrease 45 to
93 Fibonacci Heap Operation 6 : Decrease Key Decrease key of element x to k. Case 2: parent of x is marked. decrease key of x to k cut off link between x and its parent p[x], and add x to root list cut off link between p[x] and p[p[x]], add p[x] to root list If p[p[x]] unmarked, then mark it. 15 If p[p[x]] marked, cut off p[p[x]], unmark, and repeat. 7 min Decrease 35 to 5. 93
94 Fibonacci Heap Operation 6 : Decrease Key Decrease key of element x to k. Case 2: parent of x is marked. decrease key of x to k cut off link between x and its parent p[x], and add x to root list cut off link between p[x] and p[p[x]], add p[x] to root list If p[p[x]] unmarked, then mark it. 15 If p[p[x]] marked, cut off p[p[x]], unmark, and repeat. 5 7 min parent marked Decrease 35 to 5. 94
95 Fibonacci Heap Operation 6 : Decrease Key Decrease key of element x to k. Case 2: parent of x is marked. decrease key of x to k cut off link between x and its parent p[x], and add x to root list cut off link between p[x] and p[p[x]], add p[x] to root list If p[p[x]] unmarked, then mark it. 15 If p[p[x]] marked, cut off p[p[x]], unmark, and repeat min parent marked Decrease 35 to 5. 95
96 Fibonacci Heap Operation 6 : Decrease Key Decrease key of element x to k. Case 2: parent of x is marked. decrease key of x to k cut off link between x and its parent p[x], and add x to root list cut off link between p[x] and p[p[x]], add p[x] to root list If p[p[x]] unmarked, then mark it. If p[p[x]] marked, cut off p[p[x]], unmark, and repeat min Decrease 35 to 5. 96
97 97
98 Running time = O(1) 98
99 O(1) 99
100 C-c C-c 100
101 Fibonacci Heap Operation 6: Decrease Key Analysis Notation. t(h) = # trees in heap H. m(h) = # marked nodes in heap H. (H) = t(h) + 2m(H). Actual cost. O(c) O(1) time for decrease key. O(1) time for each of c cascading cuts, plus reinserting in root list. 101
102 Fibonacci Heap Operation 6: Decrease Key Analysis Notation. t(h) = # trees in heap H. m(h) = # marked nodes in heap H. (H) = t(h) + 2m(H). Actual cost. O(c) Amortized cost. O(1) t(h') = t(h) + c m(h') m(h) - c + 2 each cascading cut (except the last one) unmarks a node last cascading cut could potentially mark a node c + 2(-c + 2) = 4 - c. 102
103 Fibonacci Heap Operation 7: Delete 103
104 Fibonacci Heap Operation 7: Delete Delete node x. Decrease key of x to -. Extract min element in heap. Amortized cost. O(D(n)) O(1) for decrease-key. O(D(n)) for extract-min. D(n) = max degree of any node in Fibonacci heap. 104
105 Fibonacci Heaps: Bounding Max Degree Definition. D(N) = max degree in Fibonacci heap with N nodes. Key lemma. D(N) log N, where = (1 + 5) / 2. Corollary. Delete and Extract-min take O(log N) amortized time. 105
106 Fibonacci Heaps: Bounding Max Degree Lemma. Let x be a node with degree k, and let y 1,..., y k denote the children of x in the order in which they were linked to x. Then: degree ( y i ) 0 i 2 if if i 1 i 1 106
107 Fibonacci Heaps: Bounding Max Degree Lemma. Let x be a node with degree k, and let y 1,..., y k denote the children of x in the order in which they were linked to x. Then: degree ( y i Proof. When y i is linked to x, y 1,..., y i-1 already linked to x, degree(x) = i - 1 degree(y i ) = i - 1 since we only link nodes of equal degree Since then, y i has lost at most one child otherwise it would have been cut from x Thus, degree(y i ) = i - 1 or i - 2 ) 0 i 2 if if i 1 i 1 107
108 Fibonacci Heaps: Bounding Max Degree Key lemma. In a Fibonacci heap with N nodes, the maximum degree of any node is at most log N, where = (1 + 5) / 2. Proof of key lemma. For any node x, we show that size(x) degree(x). size(x) = # node in subtree rooted at x taking base logs, degree(x) log (size(x)) log N. Let s k be min size of tree rooted at any degree k node. trivial to see that s 0 = 1, s 1 = 2 s k monotonically increases with k Let x* be a degree k node of size s k, and let y 1,..., y k be children in order that they were linked to x*. Assume k 2 s k size ( x*) k size( y i 2 k i 2 k s i 2 k 2 s i 0 s deg[ y i 2 i 108 i i ] )
109 Fibonacci Facts Definition. The Fibonacci sequence is: 0,1,1, 2, 3, 5, 8, 13, 21,... recursive definition: F k 0 1 F k-1 F k-2 if if if k 0 k 1 k 2 Fact F1. F k+2 k, where = (1 + 5) / 2 = Fact F2. For k 0, 2 1 Consequence. s k F k+2 k. This implies that size(x) degree(x) for all nodes x. F k F i k i 0 s k size ( x*) k size( y i 2 k i 2 k s i 2 k 2 s i 0 s deg[ y i 2 i i i ] ) 109
110 Complexity of Mergeable Heaps Make-Heap(): creates and returns a new heap containing no elements. Minimum(H): returns a pointer to the node with the minimum key. Extract-Min(H): deletes the node with the minimum key. Decrease-Key(H, x, k): assigns to node x the new key value k, which is its current key value. Delete(H, x): deletes node x from heap H. 110
111 Heap summary Binary Binomial Fibonacci Type of trees Complete binary trees Binomial trees Any (no restriction) # of trees 1 O(log n) O(n) Important characteristics Tree height Tree height Max degree Number of trees Max degree Implementation (data structure) Array Linked lists Circular doubly linked list 111
112 Heap summary (Continued) Binary Binomial Fibonacci Heap size heap-size[h] Can be computed n[h] Minimum H[1] Computed from root list min[h] Complexity Worst case Worst case amortized Operation union O(n) O(log n) O(1) decrease-key O(log n) O(log n) O(1) 112
113 Questions? 113
Design and Analysis of Algorithms. Lecture 9 November 20, 2013 洪國寶
 Design and Analysis of Algorithms 演算法設計與分析 Lecture 9 November 20, 2013 洪國寶 1 Outline Advanced data structures Binary heaps (review) Binomial heaps Fibonacci heaps Dt Data structures t for disjoint dijitsets
Design and Analysis of Algorithms 演算法設計與分析 Lecture 9 November 20, 2013 洪國寶 1 Outline Advanced data structures Binary heaps (review) Binomial heaps Fibonacci heaps Dt Data structures t for disjoint dijitsets
Design and Analysis of Algorithms 演算法設計與分析. Lecture 8 November 16, 2016 洪國寶
 Design and Analysis of Algorithms 演算法設計與分析 Lecture 8 November 6, 206 洪國寶 Outline Review Amortized analysis Advanced data structures Binary heaps Binomial heaps Fibonacci heaps Data structures for disjoint
Design and Analysis of Algorithms 演算法設計與分析 Lecture 8 November 6, 206 洪國寶 Outline Review Amortized analysis Advanced data structures Binary heaps Binomial heaps Fibonacci heaps Data structures for disjoint
Fibonacci Heaps CLRS: Chapter 20 Last Revision: 21/09/04
 Fibonacci Heaps CLRS: Chapter 20 Last Revision: 21/09/04 1 Binary heap Binomial heap Fibonacci heap Procedure (worst-case) (worst-case) (amortized) Make-Heap Θ(1) Θ(1) Θ(1) Insert Θ(lg n) O(lg n) Θ(1)
Fibonacci Heaps CLRS: Chapter 20 Last Revision: 21/09/04 1 Binary heap Binomial heap Fibonacci heap Procedure (worst-case) (worst-case) (amortized) Make-Heap Θ(1) Θ(1) Θ(1) Insert Θ(lg n) O(lg n) Θ(1)
Binary and Binomial Heaps. Disclaimer: these slides were adapted from the ones by Kevin Wayne
 Binary and Binomial Heaps Disclaimer: these slides were adapted from the ones by Kevin Wayne Priority Queues Supports the following operations. Insert element x. Return min element. Return and delete minimum
Binary and Binomial Heaps Disclaimer: these slides were adapted from the ones by Kevin Wayne Priority Queues Supports the following operations. Insert element x. Return min element. Return and delete minimum
PRIORITY QUEUES. binary heaps d-ary heaps binomial heaps Fibonacci heaps. Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley
 PRIORITY QUEUES binary heaps d-ary heaps binomial heaps Fibonacci heaps Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos Last updated
PRIORITY QUEUES binary heaps d-ary heaps binomial heaps Fibonacci heaps Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos Last updated
Algorithms PRIORITY QUEUES. binary heaps d-ary heaps binomial heaps Fibonacci heaps. binary heaps d-ary heaps binomial heaps Fibonacci heaps
 Priority queue data type Lecture slides by Kevin Wayne Copyright 05 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos PRIORITY QUEUES binary heaps d-ary heaps binomial heaps Fibonacci
Priority queue data type Lecture slides by Kevin Wayne Copyright 05 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos PRIORITY QUEUES binary heaps d-ary heaps binomial heaps Fibonacci
3/7/13. Binomial Tree. Binomial Tree. Binomial Tree. Binomial Tree. Number of nodes with respect to k? N(B o ) = 1 N(B k ) = 2 N(B k-1 ) = 2 k
 //1 Adapted from: Kevin Wayne B k B k B k : a binomial tree with the addition of a left child with another binomial tree Number of nodes with respect to k? N(B o ) = 1 N(B k ) = 2 N( ) = 2 k B 1 B 2 B
//1 Adapted from: Kevin Wayne B k B k B k : a binomial tree with the addition of a left child with another binomial tree Number of nodes with respect to k? N(B o ) = 1 N(B k ) = 2 N( ) = 2 k B 1 B 2 B
Heaps. Heap/Priority queue. Binomial heaps: Advanced Algorithmics (4AP) Heaps Binary heap. Binomial heap. Jaak Vilo 2009 Spring
 .0.00 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Advanced Algorithmics (4AP) Heaps Jaak Vilo 00 Spring Binary heap http://en.wikipedia.org/wiki/binary_heap Binomial heap http://en.wikipedia.org/wiki/binomial_heap
.0.00 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Advanced Algorithmics (4AP) Heaps Jaak Vilo 00 Spring Binary heap http://en.wikipedia.org/wiki/binary_heap Binomial heap http://en.wikipedia.org/wiki/binomial_heap
Data Structures. Binomial Heaps Fibonacci Heaps. Haim Kaplan & Uri Zwick December 2013
 Data Structures Binomial Heaps Fibonacci Heaps Haim Kaplan & Uri Zwick December 13 1 Heaps / Priority queues Binary Heaps Binomial Heaps Lazy Binomial Heaps Fibonacci Heaps Insert Find-min Delete-min Decrease-key
Data Structures Binomial Heaps Fibonacci Heaps Haim Kaplan & Uri Zwick December 13 1 Heaps / Priority queues Binary Heaps Binomial Heaps Lazy Binomial Heaps Fibonacci Heaps Insert Find-min Delete-min Decrease-key
Heaps
 AdvancedAlgorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary_heap
AdvancedAlgorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary_heap
Advanced Algorithmics (4AP) Heaps
 Advanced Algorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary
Advanced Algorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary
Design and Analysis of Algorithms
 Design and Analysis of Algorithms Instructor: Sharma Thankachan Lecture 9: Binomial Heap Slides modified from Dr. Hon, with permission 1 About this lecture Binary heap supports various operations quickly:
Design and Analysis of Algorithms Instructor: Sharma Thankachan Lecture 9: Binomial Heap Slides modified from Dr. Hon, with permission 1 About this lecture Binary heap supports various operations quickly:
Priority queue. Advanced Algorithmics (6EAP) Binary heap. Heap/Priority queue. Binomial heaps: Merge two heaps.
 Priority queue Advanced Algorithmics (EAP) MTAT.03.38 Heaps Jaak Vilo 0 Spring Insert Q, x Retrieve x from Q s.t. x.value is min (or max) Sorted linked list: O(n) to insert x into right place O() access-
Priority queue Advanced Algorithmics (EAP) MTAT.03.38 Heaps Jaak Vilo 0 Spring Insert Q, x Retrieve x from Q s.t. x.value is min (or max) Sorted linked list: O(n) to insert x into right place O() access-
The potential function φ for the amortized analysis of an operation on Fibonacci heap at time (iteration) i is given by the following equation:
 Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600 127, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 01 Advanced Data Structures
Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600 127, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 01 Advanced Data Structures
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Binomial Heaps CLRS 6.1, 6.2, 6.3 University of Manitoba Priority queues A priority queue is an abstract data type formed by a set S of
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Binomial Heaps CLRS 6.1, 6.2, 6.3 University of Manitoba Priority queues A priority queue is an abstract data type formed by a set S of
Binomial Heaps. Bryan M. Franklin
 Binomial Heaps Bryan M. Franklin bmfrankl@mtu.edu 1 Tradeoffs Worst Case Operation Binary Heap Binomial Heap Make-Heap Θ(1) Θ(1) Insert Θ(lg n) O(lg n) Minimum Θ(1) O(lg n) Extract-Min Θ(lg n) Θ(lg n)
Binomial Heaps Bryan M. Franklin bmfrankl@mtu.edu 1 Tradeoffs Worst Case Operation Binary Heap Binomial Heap Make-Heap Θ(1) Θ(1) Insert Θ(lg n) O(lg n) Minimum Θ(1) O(lg n) Extract-Min Θ(lg n) Θ(lg n)
Priority Queues 9/10. Binary heaps Leftist heaps Binomial heaps Fibonacci heaps
 Priority Queues 9/10 Binary heaps Leftist heaps Binomial heaps Fibonacci heaps Priority queues are important in, among other things, operating systems (process control in multitasking systems), search
Priority Queues 9/10 Binary heaps Leftist heaps Binomial heaps Fibonacci heaps Priority queues are important in, among other things, operating systems (process control in multitasking systems), search
Meld(Q 1,Q 2 ) merge two sets
 Priority Queues MakeQueue Insert(Q,k,p) Delete(Q,k) DeleteMin(Q) Meld(Q 1,Q 2 ) Empty(Q) Size(Q) FindMin(Q) create new empty queue insert key k with priority p delete key k (given a pointer) delete key
Priority Queues MakeQueue Insert(Q,k,p) Delete(Q,k) DeleteMin(Q) Meld(Q 1,Q 2 ) Empty(Q) Size(Q) FindMin(Q) create new empty queue insert key k with priority p delete key k (given a pointer) delete key
Fibonacci Heaps Y Y o o u u c c an an s s u u b b m miitt P P ro ro b blle e m m S S et et 3 3 iin n t t h h e e b b o o x x u u p p fro fro n n tt..
 Fibonacci Heaps You You can can submit submit Problem Problem Set Set 3 in in the the box box up up front. front. Outline for Today Review from Last Time Quick refresher on binomial heaps and lazy binomial
Fibonacci Heaps You You can can submit submit Problem Problem Set Set 3 in in the the box box up up front. front. Outline for Today Review from Last Time Quick refresher on binomial heaps and lazy binomial
Outline for Today. Quick refresher on binomial heaps and lazy binomial heaps. An important operation in many graph algorithms.
 Fibonacci Heaps Outline for Today Review from Last Time Quick refresher on binomial heaps and lazy binomial heaps. The Need for decrease-key An important operation in many graph algorithms. Fibonacci Heaps
Fibonacci Heaps Outline for Today Review from Last Time Quick refresher on binomial heaps and lazy binomial heaps. The Need for decrease-key An important operation in many graph algorithms. Fibonacci Heaps
Priority Queues. Fibonacci Heap
 ibonacci Heap hans to Sartaj Sahni for the original version of the slides Operation mae-heap insert find-min delete-min union decrease-ey delete Priority Queues Lined List Binary Binomial Heaps ibonacci
ibonacci Heap hans to Sartaj Sahni for the original version of the slides Operation mae-heap insert find-min delete-min union decrease-ey delete Priority Queues Lined List Binary Binomial Heaps ibonacci
Outline for this Week
 Binomial Heaps Outline for this Week Binomial Heaps (Today) A simple, fexible, and versatile priority queue. Lazy Binomial Heaps (Today) A powerful building block for designing advanced data structures.
Binomial Heaps Outline for this Week Binomial Heaps (Today) A simple, fexible, and versatile priority queue. Lazy Binomial Heaps (Today) A powerful building block for designing advanced data structures.
Outline for this Week
 Binomial Heaps Outline for this Week Binomial Heaps (Today) A simple, flexible, and versatile priority queue. Lazy Binomial Heaps (Today) A powerful building block for designing advanced data structures.
Binomial Heaps Outline for this Week Binomial Heaps (Today) A simple, flexible, and versatile priority queue. Lazy Binomial Heaps (Today) A powerful building block for designing advanced data structures.
PARELLIZATION OF DIJKSTRA S ALGORITHM: COMPARISON OF VARIOUS PRIORITY QUEUES
 PARELLIZATION OF DIJKSTRA S ALGORITHM: COMPARISON OF VARIOUS PRIORITY QUEUES WIKTOR JAKUBIUK, KESHAV PURANMALKA 1. Introduction Dijkstra s algorithm solves the single-sourced shorest path problem on a
PARELLIZATION OF DIJKSTRA S ALGORITHM: COMPARISON OF VARIOUS PRIORITY QUEUES WIKTOR JAKUBIUK, KESHAV PURANMALKA 1. Introduction Dijkstra s algorithm solves the single-sourced shorest path problem on a
1 Binomial Tree. Structural Properties:
 Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 0 Advanced Data Structures
Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 0 Advanced Data Structures
Initializing A Max Heap. Initializing A Max Heap
 Initializing A Max Heap 3 4 5 6 7 8 70 8 input array = [-,,, 3, 4, 5, 6, 7, 8,, 0, ] Initializing A Max Heap 3 4 5 6 7 8 70 8 Start at rightmost array position that has a child. Index is n/. Initializing
Initializing A Max Heap 3 4 5 6 7 8 70 8 input array = [-,,, 3, 4, 5, 6, 7, 8,, 0, ] Initializing A Max Heap 3 4 5 6 7 8 70 8 Start at rightmost array position that has a child. Index is n/. Initializing
AVL Trees. The height of the left subtree can differ from the height of the right subtree by at most 1.
 AVL Trees In order to have a worst case running time for insert and delete operations to be O(log n), we must make it impossible for there to be a very long path in the binary search tree. The first balanced
AVL Trees In order to have a worst case running time for insert and delete operations to be O(log n), we must make it impossible for there to be a very long path in the binary search tree. The first balanced
Lecture l(x) 1. (1) x X
 Lecture 14 Agenda for the lecture Kraft s inequality Shannon codes The relation H(X) L u (X) = L p (X) H(X) + 1 14.1 Kraft s inequality While the definition of prefix-free codes is intuitively clear, we
Lecture 14 Agenda for the lecture Kraft s inequality Shannon codes The relation H(X) L u (X) = L p (X) H(X) + 1 14.1 Kraft s inequality While the definition of prefix-free codes is intuitively clear, we
Administration CSE 326: Data Structures
 Administration CSE : Data Structures Binomial Queues Neva Cherniavsky Summer Released today: Project, phase B Due today: Homework Released today: Homework I have office hours tomorrow // Binomial Queues
Administration CSE : Data Structures Binomial Queues Neva Cherniavsky Summer Released today: Project, phase B Due today: Homework Released today: Homework I have office hours tomorrow // Binomial Queues
1.6 Heap ordered trees
 1.6 Heap ordered trees A heap ordered tree is a tree satisfying the following condition. The key of a node is not greater than that of each child if any In a heap ordered tree, we can not implement find
1.6 Heap ordered trees A heap ordered tree is a tree satisfying the following condition. The key of a node is not greater than that of each child if any In a heap ordered tree, we can not implement find
SET 1C Binary Trees. 2. (i) Define the height of a binary tree or subtree and also define a height balanced (AVL) tree. (2)
 SET 1C Binary Trees 1. Construct a binary tree whose preorder traversal is K L N M P R Q S T and inorder traversal is N L K P R M S Q T 2. (i) Define the height of a binary tree or subtree and also define
SET 1C Binary Trees 1. Construct a binary tree whose preorder traversal is K L N M P R Q S T and inorder traversal is N L K P R M S Q T 2. (i) Define the height of a binary tree or subtree and also define
1 Solutions to Tute09
 s to Tute0 Questions 4. - 4. are straight forward. Q. 4.4 Show that in a binary tree of N nodes, there are N + NULL pointers. Every node has outgoing pointers. Therefore there are N pointers. Each node,
s to Tute0 Questions 4. - 4. are straight forward. Q. 4.4 Show that in a binary tree of N nodes, there are N + NULL pointers. Every node has outgoing pointers. Therefore there are N pointers. Each node,
COSC160: Data Structures Binary Trees. Jeremy Bolton, PhD Assistant Teaching Professor
 COSC160: Data Structures Binary Trees Jeremy Bolton, PhD Assistant Teaching Professor Outline I. Binary Trees I. Implementations I. Memory Management II. Binary Search Tree I. Operations Binary Trees A
COSC160: Data Structures Binary Trees Jeremy Bolton, PhD Assistant Teaching Professor Outline I. Binary Trees I. Implementations I. Memory Management II. Binary Search Tree I. Operations Binary Trees A
> asympt( ln( n! ), n ); n 360n n
 8.4 Heap Sort (heapsort) We will now look at our first (n ln(n)) algorithm: heap sort. It will use a data structure that we have already seen: a binary heap. 8.4.1 Strategy and Run-time Analysis Given
8.4 Heap Sort (heapsort) We will now look at our first (n ln(n)) algorithm: heap sort. It will use a data structure that we have already seen: a binary heap. 8.4.1 Strategy and Run-time Analysis Given
Successor. CS 361, Lecture 19. Tree-Successor. Outline
 Successor CS 361, Lecture 19 Jared Saia University of New Mexico The successor of a node x is the node that comes after x in the sorted order determined by an in-order tree walk. If all keys are distinct,
Successor CS 361, Lecture 19 Jared Saia University of New Mexico The successor of a node x is the node that comes after x in the sorted order determined by an in-order tree walk. If all keys are distinct,
2 all subsequent nodes. 252 all subsequent nodes. 401 all subsequent nodes. 398 all subsequent nodes. 330 all subsequent nodes
 ¼ À ÈÌ Ê ½¾ ÈÊÇ Ä ÅË ½µ ½¾º¾¹½ ¾µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º ¹ µ ½¾º ¹ µ ½¾º ¹¾ µ ½¾º ¹ µ ½¾¹¾ ½¼µ ½¾¹ ½ (1) CLR 12.2-1 Based on the structure of the binary tree, and the procedure of Tree-Search, any
¼ À ÈÌ Ê ½¾ ÈÊÇ Ä ÅË ½µ ½¾º¾¹½ ¾µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º ¹ µ ½¾º ¹ µ ½¾º ¹¾ µ ½¾º ¹ µ ½¾¹¾ ½¼µ ½¾¹ ½ (1) CLR 12.2-1 Based on the structure of the binary tree, and the procedure of Tree-Search, any
Lecture 5: Tuesday, January 27, Peterson s Algorithm satisfies the No Starvation property (Theorem 1)
 Com S 611 Spring Semester 2015 Advanced Topics on Distributed and Concurrent Algorithms Lecture 5: Tuesday, January 27, 2015 Instructor: Soma Chaudhuri Scribe: Nik Kinkel 1 Introduction This lecture covers
Com S 611 Spring Semester 2015 Advanced Topics on Distributed and Concurrent Algorithms Lecture 5: Tuesday, January 27, 2015 Instructor: Soma Chaudhuri Scribe: Nik Kinkel 1 Introduction This lecture covers
Fundamental Algorithms - Surprise Test
 Technische Universität München Fakultät für Informatik Lehrstuhl für Effiziente Algorithmen Dmytro Chibisov Sandeep Sadanandan Winter Semester 007/08 Sheet Model Test January 16, 008 Fundamental Algorithms
Technische Universität München Fakultät für Informatik Lehrstuhl für Effiziente Algorithmen Dmytro Chibisov Sandeep Sadanandan Winter Semester 007/08 Sheet Model Test January 16, 008 Fundamental Algorithms
Homework #4. CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class
 Homework #4 CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class o Grades depend on neatness and clarity. o Write your answers with enough detail about your approach and concepts
Homework #4 CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class o Grades depend on neatness and clarity. o Write your answers with enough detail about your approach and concepts
On the Optimality of a Family of Binary Trees Techical Report TR
 On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
Splay Trees. Splay Trees - 1
 Splay Trees In balanced tree schemes, explicit rules are followed to ensure balance. In splay trees, there are no such rules. Search, insert, and delete operations are like in binary search trees, except
Splay Trees In balanced tree schemes, explicit rules are followed to ensure balance. In splay trees, there are no such rules. Search, insert, and delete operations are like in binary search trees, except
Heaps. c P. Flener/IT Dept/Uppsala Univ. AD1, FP, PK II Heaps 1
 Heaps (Version of 21 November 2005) A min-heap (resp. max-heap) is a data structure with fast extraction of the smallest (resp. largest) item (in O(lg n) time), as well as fast insertion (also in O(lg
Heaps (Version of 21 November 2005) A min-heap (resp. max-heap) is a data structure with fast extraction of the smallest (resp. largest) item (in O(lg n) time), as well as fast insertion (also in O(lg
Introduction to Greedy Algorithms: Huffman Codes
 Introduction to Greedy Algorithms: Huffman Codes Yufei Tao ITEE University of Queensland In computer science, one interesting method to design algorithms is to go greedy, namely, keep doing the thing that
Introduction to Greedy Algorithms: Huffman Codes Yufei Tao ITEE University of Queensland In computer science, one interesting method to design algorithms is to go greedy, namely, keep doing the thing that
CSCI 104 B-Trees (2-3, 2-3-4) and Red/Black Trees. Mark Redekopp David Kempe
 1 CSCI 104 B-Trees (2-3, 2-3-4) and Red/Black Trees Mark Redekopp David Kempe 2 An example of B-Trees 2-3 TREES 3 Definition 2-3 Tree is a tree where Non-leaf nodes have 1 value & 2 children or 2 values
1 CSCI 104 B-Trees (2-3, 2-3-4) and Red/Black Trees Mark Redekopp David Kempe 2 An example of B-Trees 2-3 TREES 3 Definition 2-3 Tree is a tree where Non-leaf nodes have 1 value & 2 children or 2 values
Data Structures, Algorithms, & Applications in C++ ( Chapter 9 )
 ) Priority Queues Two kinds of priority queues: Min priority queue. Max priority queue. Min Priority Queue Collection of elements. Each element has a priority or key. Supports following operations: isempty
) Priority Queues Two kinds of priority queues: Min priority queue. Max priority queue. Min Priority Queue Collection of elements. Each element has a priority or key. Supports following operations: isempty
Chapter 16. Binary Search Trees (BSTs)
 Chapter 16 Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types of search trees designed
Chapter 16 Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types of search trees designed
Heap Building Bounds
 Heap Building Bounds Zhentao Li 1 and Bruce A. Reed 2 1 School of Computer Science, McGill University zhentao.li@mail.mcgill.ca 2 School of Computer Science, McGill University breed@cs.mcgill.ca Abstract.
Heap Building Bounds Zhentao Li 1 and Bruce A. Reed 2 1 School of Computer Science, McGill University zhentao.li@mail.mcgill.ca 2 School of Computer Science, McGill University breed@cs.mcgill.ca Abstract.
CSE 100: TREAPS AND RANDOMIZED SEARCH TREES
 CSE 100: TREAPS AND RANDOMIZED SEARCH TREES Midterm Review Practice Midterm covered during Sunday discussion Today Run time analysis of building the Huffman tree AVL rotations and treaps Huffman s algorithm
CSE 100: TREAPS AND RANDOMIZED SEARCH TREES Midterm Review Practice Midterm covered during Sunday discussion Today Run time analysis of building the Huffman tree AVL rotations and treaps Huffman s algorithm
Sublinear Time Algorithms Oct 19, Lecture 1
 0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
Ch 10 Trees. Introduction to Trees. Tree Representations. Binary Tree Nodes. Tree Traversals. Binary Search Trees
 Ch 10 Trees Introduction to Trees Tree Representations Binary Tree Nodes Tree Traversals Binary Search Trees 1 Binary Trees A binary tree is a finite set of elements called nodes. The set is either empty
Ch 10 Trees Introduction to Trees Tree Representations Binary Tree Nodes Tree Traversals Binary Search Trees 1 Binary Trees A binary tree is a finite set of elements called nodes. The set is either empty
9.7 Binomial Queues. This excerpt made available by permission of Robert Sedgewick, and of Pearson Education, Inc.
 406 9.7 CH lgorithms, 3rd dition, in Java, arts 1-4: Fundamentals, Data tructures, orting, and earching. obert edgewick, ddison-esley 2002. his excerpt made available by permission of obert edgewick, and
406 9.7 CH lgorithms, 3rd dition, in Java, arts 1-4: Fundamentals, Data tructures, orting, and earching. obert edgewick, ddison-esley 2002. his excerpt made available by permission of obert edgewick, and
CSE 21 Winter 2016 Homework 6 Due: Wednesday, May 11, 2016 at 11:59pm. Instructions
 CSE 1 Winter 016 Homework 6 Due: Wednesday, May 11, 016 at 11:59pm Instructions Homework should be done in groups of one to three people. You are free to change group members at any time throughout the
CSE 1 Winter 016 Homework 6 Due: Wednesday, May 11, 016 at 11:59pm Instructions Homework should be done in groups of one to three people. You are free to change group members at any time throughout the
CSCE 750, Fall 2009 Quizzes with Answers
 CSCE 750, Fall 009 Quizzes with Answers Stephen A. Fenner September 4, 011 1. Give an exact closed form for Simplify your answer as much as possible. k 3 k+1. We reduce the expression to a form we ve already
CSCE 750, Fall 009 Quizzes with Answers Stephen A. Fenner September 4, 011 1. Give an exact closed form for Simplify your answer as much as possible. k 3 k+1. We reduce the expression to a form we ve already
Supporting Information
 Supporting Information Novikoff et al. 0.073/pnas.0986309 SI Text The Recap Method. In The Recap Method in the paper, we described a schedule in terms of a depth-first traversal of a full binary tree,
Supporting Information Novikoff et al. 0.073/pnas.0986309 SI Text The Recap Method. In The Recap Method in the paper, we described a schedule in terms of a depth-first traversal of a full binary tree,
THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE
 THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE GÜNTER ROTE Abstract. A salesperson wants to visit each of n objects that move on a line at given constant speeds in the shortest possible time,
THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE GÜNTER ROTE Abstract. A salesperson wants to visit each of n objects that move on a line at given constant speeds in the shortest possible time,
Max Registers, Counters and Monotone Circuits
 James Aspnes 1 Hagit Attiya 2 Keren Censor 2 1 Yale 2 Technion Counters Model Collects Our goal: build a cheap counter for an asynchronous shared-memory system. Two operations: increment and read. Read
James Aspnes 1 Hagit Attiya 2 Keren Censor 2 1 Yale 2 Technion Counters Model Collects Our goal: build a cheap counter for an asynchronous shared-memory system. Two operations: increment and read. Read
Practical session No. 5 Trees
 Practical session No. 5 Trees Tree Binary Tree k-tree Trees as Basic Data Structures ADT that stores elements hierarchically. Each node in the tree has a parent (except for the root), and zero or more
Practical session No. 5 Trees Tree Binary Tree k-tree Trees as Basic Data Structures ADT that stores elements hierarchically. Each node in the tree has a parent (except for the root), and zero or more
The suffix binary search tree and suffix AVL tree
 Journal of Discrete Algorithms 1 (2003) 387 408 www.elsevier.com/locate/jda The suffix binary search tree and suffix AVL tree Robert W. Irving, Lorna Love Department of Computing Science, University of
Journal of Discrete Algorithms 1 (2003) 387 408 www.elsevier.com/locate/jda The suffix binary search tree and suffix AVL tree Robert W. Irving, Lorna Love Department of Computing Science, University of
Structural Induction
 Structural Induction Jason Filippou CMSC250 @ UMCP 07-05-2016 Jason Filippou (CMSC250 @ UMCP) Structural Induction 07-05-2016 1 / 26 Outline 1 Recursively defined structures 2 Proofs Binary Trees Jason
Structural Induction Jason Filippou CMSC250 @ UMCP 07-05-2016 Jason Filippou (CMSC250 @ UMCP) Structural Induction 07-05-2016 1 / 26 Outline 1 Recursively defined structures 2 Proofs Binary Trees Jason
Stanford University, CS 106X Homework Assignment 5: Priority Queue Binomial Heap Optional Extension
 Stanford University, CS 106X Homework Assignment 5: Priority Queue Binomial Heap Optional Extension Extension description by Jerry Cain. This document describes an optional extension to the assignment.
Stanford University, CS 106X Homework Assignment 5: Priority Queue Binomial Heap Optional Extension Extension description by Jerry Cain. This document describes an optional extension to the assignment.
CS4311 Design and Analysis of Algorithms. Lecture 14: Amortized Analysis I
 CS43 Design and Analysis of Algorithms Lecture 4: Amortized Analysis I About this lecture Given a data structure, amortized analysis studies in a sequence of operations, the average time to perform an
CS43 Design and Analysis of Algorithms Lecture 4: Amortized Analysis I About this lecture Given a data structure, amortized analysis studies in a sequence of operations, the average time to perform an
CMPSCI 311: Introduction to Algorithms Second Midterm Practice Exam SOLUTIONS
 CMPSCI 311: Introduction to Algorithms Second Midterm Practice Exam SOLUTIONS November 17, 2016. Name: ID: Instructions: Answer the questions directly on the exam pages. Show all your work for each question.
CMPSCI 311: Introduction to Algorithms Second Midterm Practice Exam SOLUTIONS November 17, 2016. Name: ID: Instructions: Answer the questions directly on the exam pages. Show all your work for each question.
UNIT 2. Greedy Method GENERAL METHOD
 UNIT 2 GENERAL METHOD Greedy Method Greedy is the most straight forward design technique. Most of the problems have n inputs and require us to obtain a subset that satisfies some constraints. Any subset
UNIT 2 GENERAL METHOD Greedy Method Greedy is the most straight forward design technique. Most of the problems have n inputs and require us to obtain a subset that satisfies some constraints. Any subset
Chapter 5: Algorithms
 Chapter 5: Algorithms Computer Science: An Overview Tenth Edition by J. Glenn Brookshear Presentation files modified by Farn Wang Copyright 2008 Pearson Education, Inc. Publishing as Pearson Addison-Wesley
Chapter 5: Algorithms Computer Science: An Overview Tenth Edition by J. Glenn Brookshear Presentation files modified by Farn Wang Copyright 2008 Pearson Education, Inc. Publishing as Pearson Addison-Wesley
Binary Tree Applications
 Binary Tree Applications Lecture 32 Section 19.2 Robb T. Koether Hampden-Sydney College Wed, Apr 17, 2013 Robb T. Koether (Hampden-Sydney College) Binary Tree Applications Wed, Apr 17, 2013 1 / 46 1 Expression
Binary Tree Applications Lecture 32 Section 19.2 Robb T. Koether Hampden-Sydney College Wed, Apr 17, 2013 Robb T. Koether (Hampden-Sydney College) Binary Tree Applications Wed, Apr 17, 2013 1 / 46 1 Expression
Smoothed Analysis of Binary Search Trees
 Smoothed Analysis of Binary Search Trees Bodo Manthey and Rüdiger Reischuk Universität zu Lübeck, Institut für Theoretische Informatik Ratzeburger Allee 160, 23538 Lübeck, Germany manthey/reischuk@tcs.uni-luebeck.de
Smoothed Analysis of Binary Search Trees Bodo Manthey and Rüdiger Reischuk Universität zu Lübeck, Institut für Theoretische Informatik Ratzeburger Allee 160, 23538 Lübeck, Germany manthey/reischuk@tcs.uni-luebeck.de
On the Optimality of a Family of Binary Trees
 On the Optimality of a Family of Binary Trees Dana Vrajitoru Computer and Information Sciences Department Indiana University South Bend South Bend, IN 46645 Email: danav@cs.iusb.edu William Knight Computer
On the Optimality of a Family of Binary Trees Dana Vrajitoru Computer and Information Sciences Department Indiana University South Bend South Bend, IN 46645 Email: danav@cs.iusb.edu William Knight Computer
1) S = {s}; 2) for each u V {s} do 3) dist[u] = cost(s, u); 4) Insert u into a 2-3 tree Q with dist[u] as the key; 5) for i = 1 to n 1 do 6) Identify
![1) S = {s}; 2) for each u V {s} do 3) dist[u] = cost(s, u); 4) Insert u into a 2-3 tree Q with dist[u] as the key; 5) for i = 1 to n 1 do 6) Identify 1) S = {s}; 2) for each u V {s} do 3) dist[u] = cost(s, u); 4) Insert u into a 2-3 tree Q with dist[u] as the key; 5) for i = 1 to n 1 do 6) Identify](/thumbs/77/75720566.jpg) CSE 3500 Algorithms and Complexity Fall 2016 Lecture 17: October 25, 2016 Dijkstra s Algorithm Dijkstra s algorithm for the SSSP problem generates the shortest paths in nondecreasing order of the shortest
CSE 3500 Algorithms and Complexity Fall 2016 Lecture 17: October 25, 2016 Dijkstra s Algorithm Dijkstra s algorithm for the SSSP problem generates the shortest paths in nondecreasing order of the shortest
Practical session No. 5 Trees
 Practical session No. 5 Trees Tree Trees as Basic Data Structures ADT that stores elements hierarchically. With the exception of the root, each node in the tree has a parent and zero or more children nodes.
Practical session No. 5 Trees Tree Trees as Basic Data Structures ADT that stores elements hierarchically. With the exception of the root, each node in the tree has a parent and zero or more children nodes.
NOTES ON FIBONACCI TREES AND THEIR OPTIMALITY* YASUICHI HORIBE INTRODUCTION 1. FIBONACCI TREES
 0#0# NOTES ON FIBONACCI TREES AND THEIR OPTIMALITY* YASUICHI HORIBE Shizuoka University, Hamamatsu, 432, Japan (Submitted February 1982) INTRODUCTION Continuing a previous paper [3], some new observations
0#0# NOTES ON FIBONACCI TREES AND THEIR OPTIMALITY* YASUICHI HORIBE Shizuoka University, Hamamatsu, 432, Japan (Submitted February 1982) INTRODUCTION Continuing a previous paper [3], some new observations
Optimal Satisficing Tree Searches
 Optimal Satisficing Tree Searches Dan Geiger and Jeffrey A. Barnett Northrop Research and Technology Center One Research Park Palos Verdes, CA 90274 Abstract We provide an algorithm that finds optimal
Optimal Satisficing Tree Searches Dan Geiger and Jeffrey A. Barnett Northrop Research and Technology Center One Research Park Palos Verdes, CA 90274 Abstract We provide an algorithm that finds optimal
CSE 417 Algorithms. Huffman Codes: An Optimal Data Compression Method
 CSE 417 Algorithms Huffman Codes: An Optimal Data Compression Method 1 Compression Example 100k file, 6 letter alphabet: a 45% b 13% c 12% d 16% e 9% f 5% File Size: ASCII, 8 bits/char: 800kbits 2 3 >
CSE 417 Algorithms Huffman Codes: An Optimal Data Compression Method 1 Compression Example 100k file, 6 letter alphabet: a 45% b 13% c 12% d 16% e 9% f 5% File Size: ASCII, 8 bits/char: 800kbits 2 3 >
CEC login. Student Details Name SOLUTIONS
 Student Details Name SOLUTIONS CEC login Instructions You have roughly 1 minute per point, so schedule your time accordingly. There is only one correct answer per question. Good luck! Question 1. Searching
Student Details Name SOLUTIONS CEC login Instructions You have roughly 1 minute per point, so schedule your time accordingly. There is only one correct answer per question. Good luck! Question 1. Searching
Lecture 8 Feb 16, 2017
 CS 4: Advanced Algorithms Spring 017 Prof. Jelani Nelson Lecture 8 Feb 16, 017 Scribe: Tiffany 1 Overview In the last lecture we covered the properties of splay trees, including amortized O(log n) time
CS 4: Advanced Algorithms Spring 017 Prof. Jelani Nelson Lecture 8 Feb 16, 017 Scribe: Tiffany 1 Overview In the last lecture we covered the properties of splay trees, including amortized O(log n) time
6.854J / J Advanced Algorithms Fall 2008
 MIT OpenCourseWare http://ocw.mit.edu 6.854J / 18.415J Advanced Algorithms Fall 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advanced
MIT OpenCourseWare http://ocw.mit.edu 6.854J / 18.415J Advanced Algorithms Fall 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advanced
Lecture 4: Divide and Conquer
 Lecture 4: Divide and Conquer Divide and Conquer Merge sort is an example of a divide-and-conquer algorithm Recall the three steps (at each level to solve a divideand-conquer problem recursively Divide
Lecture 4: Divide and Conquer Divide and Conquer Merge sort is an example of a divide-and-conquer algorithm Recall the three steps (at each level to solve a divideand-conquer problem recursively Divide
COMP251: Amortized Analysis
 COMP251: Amortized Analysis Jérôme Waldispühl School of Computer Science McGill University Based on (Cormen et al., 2009) T n = 2 % T n 5 + n( What is the height of the recursion tree? log ( n log, n log
COMP251: Amortized Analysis Jérôme Waldispühl School of Computer Science McGill University Based on (Cormen et al., 2009) T n = 2 % T n 5 + n( What is the height of the recursion tree? log ( n log, n log
useful than solving these yourself, writing up your solution and then either comparing your
 CSE 441T/541T: Advanced Algorithms Fall Semester, 2003 September 9, 2004 Practice Problems Solutions Here are the solutions for the practice problems. However, reading these is far less useful than solving
CSE 441T/541T: Advanced Algorithms Fall Semester, 2003 September 9, 2004 Practice Problems Solutions Here are the solutions for the practice problems. However, reading these is far less useful than solving
Chapter wise Question bank
 GOVERNMENT ENGINEERING COLLEGE - MODASA Chapter wise Question bank Subject Name Analysis and Design of Algorithm Semester Department 5 th Term ODD 2015 Information Technology / Computer Engineering Chapter
GOVERNMENT ENGINEERING COLLEGE - MODASA Chapter wise Question bank Subject Name Analysis and Design of Algorithm Semester Department 5 th Term ODD 2015 Information Technology / Computer Engineering Chapter
COMPUTER SCIENCE 20, SPRING 2014 Homework Problems Recursive Definitions, Structural Induction, States and Invariants
 COMPUTER SCIENCE 20, SPRING 2014 Homework Problems Recursive Definitions, Structural Induction, States and Invariants Due Wednesday March 12, 2014. CS 20 students should bring a hard copy to class. CSCI
COMPUTER SCIENCE 20, SPRING 2014 Homework Problems Recursive Definitions, Structural Induction, States and Invariants Due Wednesday March 12, 2014. CS 20 students should bring a hard copy to class. CSCI
Basic Data Structures. Figure 8.1 Lists, stacks, and queues. Terminology for Stacks. Terminology for Lists. Chapter 8: Data Abstractions
 Chapter 8: Data Abstractions Computer Science: An Overview Tenth Edition by J. Glenn Brookshear Chapter 8: Data Abstractions 8.1 Data Structure Fundamentals 8.2 Implementing Data Structures 8.3 A Short
Chapter 8: Data Abstractions Computer Science: An Overview Tenth Edition by J. Glenn Brookshear Chapter 8: Data Abstractions 8.1 Data Structure Fundamentals 8.2 Implementing Data Structures 8.3 A Short
Algorithmic Game Theory and Applications. Lecture 11: Games of Perfect Information
 Algorithmic Game Theory and Applications Lecture 11: Games of Perfect Information Kousha Etessami finite games of perfect information Recall, a perfect information (PI) game has only 1 node per information
Algorithmic Game Theory and Applications Lecture 11: Games of Perfect Information Kousha Etessami finite games of perfect information Recall, a perfect information (PI) game has only 1 node per information
IEOR E4004: Introduction to OR: Deterministic Models
 IEOR E4004: Introduction to OR: Deterministic Models 1 Dynamic Programming Following is a summary of the problems we discussed in class. (We do not include the discussion on the container problem or the
IEOR E4004: Introduction to OR: Deterministic Models 1 Dynamic Programming Following is a summary of the problems we discussed in class. (We do not include the discussion on the container problem or the
1 Online Problem Examples
 Comp 260: Advanced Algorithms Tufts University, Spring 2018 Prof. Lenore Cowen Scribe: Isaiah Mindich Lecture 9: Online Algorithms All of the algorithms we have studied so far operate on the assumption
Comp 260: Advanced Algorithms Tufts University, Spring 2018 Prof. Lenore Cowen Scribe: Isaiah Mindich Lecture 9: Online Algorithms All of the algorithms we have studied so far operate on the assumption
c 2004 Society for Industrial and Applied Mathematics
 SIAM J. COMPUT. Vol. 33, No. 5, pp. 1011 1034 c 2004 Society for Industrial and Applied Mathematics EFFICIENT ALGORITHMS FOR OPTIMAL STREAM MERGING FOR MEDIA-ON-DEMAND AMOTZ BAR-NOY AND RICHARD E. LADNER
SIAM J. COMPUT. Vol. 33, No. 5, pp. 1011 1034 c 2004 Society for Industrial and Applied Mathematics EFFICIENT ALGORITHMS FOR OPTIMAL STREAM MERGING FOR MEDIA-ON-DEMAND AMOTZ BAR-NOY AND RICHARD E. LADNER
4/8/13. Part 6. Trees (2) Outline. Balanced Search Trees. 2-3 Trees Trees Red-Black Trees AVL Trees. to maximum n. Tree A. Tree B.
 art 6. Trees (2) C 200 Algorithms and Data tructures 1 Outline 2-3 Trees 2-3-4 Trees Red-Black Trees AV Trees 2 Balanced earch Trees Tree A Tree B to maximum n Tree D 3 1 Balanced earch Trees A search
art 6. Trees (2) C 200 Algorithms and Data tructures 1 Outline 2-3 Trees 2-3-4 Trees Red-Black Trees AV Trees 2 Balanced earch Trees Tree A Tree B to maximum n Tree D 3 1 Balanced earch Trees A search
UNIT VI TREES. Marks - 14
 UNIT VI TREES Marks - 14 SYLLABUS 6.1 Non-linear data structures 6.2 Binary trees : Complete Binary Tree, Basic Terms: level number, degree, in-degree and out-degree, leaf node, directed edge, path, depth,
UNIT VI TREES Marks - 14 SYLLABUS 6.1 Non-linear data structures 6.2 Binary trees : Complete Binary Tree, Basic Terms: level number, degree, in-degree and out-degree, leaf node, directed edge, path, depth,
Smoothed Analysis of the Height of Binary Search Trees
 Electronic Colloquium on Computational Complexity, Report No. 63 (2005) Smoothed Analysis of the Height of Binary Search Trees Bodo Manthey Rüdiger Reischuk Universität zu Lübeck Institut für Theoretische
Electronic Colloquium on Computational Complexity, Report No. 63 (2005) Smoothed Analysis of the Height of Binary Search Trees Bodo Manthey Rüdiger Reischuk Universität zu Lübeck Institut für Theoretische
Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Splay Trees Date: 9/27/16
 600.463 Introduction to lgoritms / lgoritms I Lecturer: Micael initz Topic: Splay Trees ate: 9/27/16 8.1 Introduction Today we re going to talk even more about binary searc trees. -trees, red-black trees,
600.463 Introduction to lgoritms / lgoritms I Lecturer: Micael initz Topic: Splay Trees ate: 9/27/16 8.1 Introduction Today we re going to talk even more about binary searc trees. -trees, red-black trees,
Chapter 7 Sorting (Part II)
 Data Structure t Chapter 7 Sorting (Part II) Angela Chih-Wei i Tang Department of Communication Engineering National Central University Jhongli, Taiwan 2010 Spring Outline Heap Max/min heap Insertion &
Data Structure t Chapter 7 Sorting (Part II) Angela Chih-Wei i Tang Department of Communication Engineering National Central University Jhongli, Taiwan 2010 Spring Outline Heap Max/min heap Insertion &
About this lecture. Three Methods for the Same Purpose (1) Aggregate Method (2) Accounting Method (3) Potential Method.
 About this lecture Given a data structure, amortized analysis studies in a sequence of operations, the average time to perform an operation Introduce amortized cost of an operation Three Methods for the
About this lecture Given a data structure, amortized analysis studies in a sequence of operations, the average time to perform an operation Introduce amortized cost of an operation Three Methods for the
Lecture Quantitative Finance Spring Term 2015
 implied Lecture Quantitative Finance Spring Term 2015 : May 7, 2015 1 / 28 implied 1 implied 2 / 28 Motivation and setup implied the goal of this chapter is to treat the implied which requires an algorithm
implied Lecture Quantitative Finance Spring Term 2015 : May 7, 2015 1 / 28 implied 1 implied 2 / 28 Motivation and setup implied the goal of this chapter is to treat the implied which requires an algorithm
CS221 / Spring 2018 / Sadigh. Lecture 9: Games I
 CS221 / Spring 2018 / Sadigh Lecture 9: Games I Course plan Search problems Markov decision processes Adversarial games Constraint satisfaction problems Bayesian networks Reflex States Variables Logic
CS221 / Spring 2018 / Sadigh Lecture 9: Games I Course plan Search problems Markov decision processes Adversarial games Constraint satisfaction problems Bayesian networks Reflex States Variables Logic
Splay Trees Goodrich, Tamassia, Dickerson Splay Trees 1
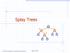 Spla Trees v 6 3 8 4 2004 Goodrich, Tamassia, Dickerson Spla Trees 1 Spla Trees are Binar Search Trees BST Rules: entries stored onl at internal nodes kes stored at nodes in the left subtree of v are less
Spla Trees v 6 3 8 4 2004 Goodrich, Tamassia, Dickerson Spla Trees 1 Spla Trees are Binar Search Trees BST Rules: entries stored onl at internal nodes kes stored at nodes in the left subtree of v are less
Tug of War Game. William Gasarch and Nick Sovich and Paul Zimand. October 6, Abstract
 Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Finding Equilibria in Games of No Chance
 Finding Equilibria in Games of No Chance Kristoffer Arnsfelt Hansen, Peter Bro Miltersen, and Troels Bjerre Sørensen Department of Computer Science, University of Aarhus, Denmark {arnsfelt,bromille,trold}@daimi.au.dk
Finding Equilibria in Games of No Chance Kristoffer Arnsfelt Hansen, Peter Bro Miltersen, and Troels Bjerre Sørensen Department of Computer Science, University of Aarhus, Denmark {arnsfelt,bromille,trold}@daimi.au.dk
Lecture 9: Games I. Course plan. A simple game. Roadmap. Machine learning. Example: game 1
 Lecture 9: Games I Course plan Search problems Markov decision processes Adversarial games Constraint satisfaction problems Bayesian networks Reflex States Variables Logic Low-level intelligence Machine
Lecture 9: Games I Course plan Search problems Markov decision processes Adversarial games Constraint satisfaction problems Bayesian networks Reflex States Variables Logic Low-level intelligence Machine
Lecture 14: Basic Fixpoint Theorems (cont.)
 Lecture 14: Basic Fixpoint Theorems (cont) Predicate Transformers Monotonicity and Continuity Existence of Fixpoints Computing Fixpoints Fixpoint Characterization of CTL Operators 1 2 E M Clarke and E
Lecture 14: Basic Fixpoint Theorems (cont) Predicate Transformers Monotonicity and Continuity Existence of Fixpoints Computing Fixpoints Fixpoint Characterization of CTL Operators 1 2 E M Clarke and E
Q1. [?? pts] Search Traces
![Q1. [?? pts] Search Traces Q1. [?? pts] Search Traces](/thumbs/80/81482567.jpg) CS 188 Spring 2010 Introduction to Artificial Intelligence Midterm Exam Solutions Q1. [?? pts] Search Traces Each of the trees (G1 through G5) was generated by searching the graph (below, left) with a
CS 188 Spring 2010 Introduction to Artificial Intelligence Midterm Exam Solutions Q1. [?? pts] Search Traces Each of the trees (G1 through G5) was generated by searching the graph (below, left) with a
Notes on Natural Logic
 Notes on Natural Logic Notes for PHIL370 Eric Pacuit November 16, 2012 1 Preliminaries: Trees A tree is a structure T = (T, E), where T is a nonempty set whose elements are called nodes and E is a relation
Notes on Natural Logic Notes for PHIL370 Eric Pacuit November 16, 2012 1 Preliminaries: Trees A tree is a structure T = (T, E), where T is a nonempty set whose elements are called nodes and E is a relation
