Lecture 2: The Simple Story of 2-SAT
|
|
|
- Kathleen Martina Carpenter
- 6 years ago
- Views:
Transcription
1 : Topics in Algorithms - Random Satisfiability March 04, 2014 Lecture 2: The Simple Story of 2-SAT Lecturer: Benny Applebaum Scribe(s): Mor Baruch 1 Lecture Outline In this talk we will show that it is possible to efficiently decide if a 2-CNF formula is satisfiable. We will also study the satisfiability threshold of random 2-CNF formulas. 2 Notation Recall that we used the following terminology: Variables: x 1, x 2,..., x n. Literals: x 1, x 1, x 2, x 2,..., x n, x n. k-clause: a conjunction (OR) of k distinct literals. For example, a 2-clause: l i l j, a 1-clause (unit-clause): l i, and a 0-clause: (contradiction). k-cnf formula ϕ = (C 1,..., C m ) where C i is k-clause. Assignment σ {0, 1} n. Partial assignment σ {0, 1, } n. 3 Example Consider the following 2-CNF formula: x 1 x 2, x 1 x 2, x 2 x 3, x 3 x 4, x 1 x 2. Let s try to set x 1 = 0. Then the formula simplifies to: T, x 2, x 2 x 3, x 3 x 4, x 2. where T denotes the value Truth. We are now forced to assign x 2 = 1 (as there is a unit-clause), and the formula simplifies to T, T, x 3, x 3 x 4,, 2: The Simple Story of 2-SAT-1
2 where is the empty clause which denotes contradiction. So we have to backtrack to the last free step. Let s try x 1 = 1: We are now forced to set x 2 = 1: We are now forced to set x 3 = 1: x 2, T, x 2 x 3, x 3 x 4, T. T, T, x 3, x 3 x 4, T. T, T, T, T, T, and any value for x 4 will satisfy the formula. Hence, we ve found two satisfying assignments: (1,1,1,0), (1,1,1,1). 4 An Efficient Algorithm based on Unit Clause Propogation Abstracting the above example, we present an algorithm that attempts to satisfy a 2-CNF formula ϕ as follows. Algorithm(ϕ) (0) Initialize empty assignment σ = n. (1) If all variables are assigned return σ. (2) Choose an unassigned variable x i. (a) (Try x i = 1) - Set σ i = 1, ϕ Simplify(ϕ, x i ). - ϕ Unit Clause Propagation(ϕ ). - If ϕ does not contain goto (1). (b) (Try x i = 0) - Unassign variables from step (a). - Set σ i = 0, ϕ Simplify(ϕ, x i ). - ϕ Unit Clause Propagation(ϕ ). - If ϕ does not contain goto (1). (3) Halt with UNSAT. Simplify(ϕ, l i ) clause C ϕ: - If l i C, remove C. - If l i C, C C \ l i. 2: The Simple Story of 2-SAT-2
3 - Otherwise, copy C as is. Output the modified formula. Unit Clause Propagation(ϕ) While unit clause l i : - Update σ: if l i = x i set σ i = 1, else (l i = x i ) set σ i = 0. - ϕ Simplify(ϕ, l i ). Complexity. Let n denote the number of variables and let m denote the number of clauses. It is not hard to verify that there are at most n outer iterations and that each call to UCP takes at most O(m) time, therefore the running time of Algorithm is O(m n). (Home assignment: Find an implementation in O(n + m) complexity.) 4.1 Correctness Lemma 1 If the algorithm outputs an assignment σ, then σ satisfies ϕ. We will need the following definition: A partial assignment σ {0, 1, } n violate a clause C = l i l j if: σ i and σ j are assigned (i.e.,σ i, σ j ) and σ i doesn t satisfy l i and σ j doesn t satisfy l j. The lemma follows from the following invariance. Invariance 2 At the beginning of each iteration, the current partial assignment σ (i) does not violate any of the clauses of C. Proof of Invariance 2: By induction on i. The basis is trivial as in the first iteration σ = n and so none of the clauses are violated. Step: we ll prove that none of the clauses C are violated by σ (i+1). If both variables of C were assigned before the last iteration, then, by the induction hypothesis, σ (i) doesn t violate C, and therefore, so is σ (i+1). If both variables of C were assigned in the last iteration, then C must be satisfied by σ (i+1), otherwise, the algorithm finds a contradiction. Lemma 3 If the algorithm outputs UNSAT, then ϕ is unsatisfiable. Proof Let ϕ be the formula at the beginning of the iteration in which A halts, and let x i be the variable chosen at step (2) of this last iteration. Note that ϕ is a 2-CNF formula and ϕ ϕ (i.e., all the clauses of ϕ appear as clauses in ϕ). Hence, it suffices to show that ϕ is unsatisfiable. Let ϕ 0 =Simplify(ϕ, x i = 0) and ϕ 1 =Simplify(ϕ, x i = 1). It suffices to show that both ϕ 0 and ϕ 1 are unsatisfiable. Recall that the formula UCP(ϕ 0 ) and the formula UCP(ϕ 1 ) contain a contradiction. The proof now follows by noting that if UCP(ψ) contains a contradiction, then ψ is UNSAT. Therefore, we have an efficient algorithm for SAT of 2-CNF. 2: The Simple Story of 2-SAT-3
4 5 Graphical View For a 2-CNF formula ϕ, define the implication graph G = G ϕ as follows: nodes x 1, x 1, x 2, x 2,..., x n, x n for a clause l i l j define the edges: l i l j l j l i Main property: Let σ be a satisfying assignment. If σ satisfies a node v, then σ satisfies all nodes u achievable from v. The property can be proven by induction on the length of the path. Theorem 4 ϕ is satisfiable iff the graph G does not contain a contradiction path of the form: l i l i l i. Proof 1. ( contradiction path ϕ is UNSAT): - Take a potential assignment σ. - If σ satisfies l i, then by Property it must satisfy l i. Contradiction. - If σ satisfies l i, then by Property it must satisfy l i. Contradiction. 2. (ϕ is UNSAT contradiction path): If ϕ is UNSAT Algorithm Halts. for some x i we have: (a) l j x i l j (b) l k x i l k In our graph, if l i l j is an edge, then l j l i is also an edge. By reversing edges and negating: (a) x i l j x i (b) x i l k x i Therefore, there exists a contradiction path. 2: The Simple Story of 2-SAT-4
5 6 The Satisfiability Threshold for Random 2-CNF Reminder: F 2 (n, m) is the distribution over 2-CNF with n variables, m clauses and each clause is chosen uniformly at random from all possible 2-clauses. Theorem 5 Let r be a positive constant. Then: lim Pr[F 2(n, r n) is Satisfiable] = n Proof of the first case (r < 1): A bicycle of length s 2 is a sequence of clauses of the form: (u, l 1 ), ( l 1, l 2 ),..., ( l s, v), { 1 if r < 1 0 if r > 1. where l 1,..., l s are distinct literals and u, v {l 1,..., l s, l 1,..., l s }. By the previous theorem, if ϕ is UNSAT, then G ϕ contains a bicycle. We ll show that for r < 1, Pr[F 2 (n, r n)contains bicycle] = o(1). For a fixed s-bicycle A, Pr[A F 2 (n, m)] = ( ) ( s+1 m 1 )) s ( n 2 ( m 2n(n 1) # of all possible s-bicycles 2 s n s (2s) 2 = 4(2n) s s 2. Overall, we get: ( ) 2 n 1 Pr[ bicycle F 2 (n, m)] 4m ( ) 2n m s = s 2 = 2m 2n(n 1) 2n(n 1) n(n 1) n 0.1 (n 0.2 const) + ) = O (*) m = r n and r < 1. s=n 0.1 (n 2 r n0.1 ) s+1 ( ) 4(2n) s s 2 m s+1 = 2n(n 1) ( ) m s s 2 n 1 ( n 0.1 n 0.2 n ) + n n2 r n0.1 ( ) = o(1) n 2: The Simple Story of 2-SAT-5
SAT and DPLL. Introduction. Preliminaries. Normal forms DPLL. Complexity. Espen H. Lian. DPLL Implementation. Bibliography.
 SAT and Espen H. Lian Ifi, UiO Implementation May 4, 2010 Espen H. Lian (Ifi, UiO) SAT and May 4, 2010 1 / 59 Espen H. Lian (Ifi, UiO) SAT and May 4, 2010 2 / 59 Introduction Introduction SAT is the problem
SAT and Espen H. Lian Ifi, UiO Implementation May 4, 2010 Espen H. Lian (Ifi, UiO) SAT and May 4, 2010 1 / 59 Espen H. Lian (Ifi, UiO) SAT and May 4, 2010 2 / 59 Introduction Introduction SAT is the problem
SAT and DPLL. Espen H. Lian. May 4, Ifi, UiO. Espen H. Lian (Ifi, UiO) SAT and DPLL May 4, / 59
 SAT and DPLL Espen H. Lian Ifi, UiO May 4, 2010 Espen H. Lian (Ifi, UiO) SAT and DPLL May 4, 2010 1 / 59 Normal forms Normal forms DPLL Complexity DPLL Implementation Bibliography Espen H. Lian (Ifi, UiO)
SAT and DPLL Espen H. Lian Ifi, UiO May 4, 2010 Espen H. Lian (Ifi, UiO) SAT and DPLL May 4, 2010 1 / 59 Normal forms Normal forms DPLL Complexity DPLL Implementation Bibliography Espen H. Lian (Ifi, UiO)
Another Variant of 3sat. 3sat. 3sat Is NP-Complete. The Proof (concluded)
 3sat k-sat, where k Z +, is the special case of sat. The formula is in CNF and all clauses have exactly k literals (repetition of literals is allowed). For example, (x 1 x 2 x 3 ) (x 1 x 1 x 2 ) (x 1 x
3sat k-sat, where k Z +, is the special case of sat. The formula is in CNF and all clauses have exactly k literals (repetition of literals is allowed). For example, (x 1 x 2 x 3 ) (x 1 x 1 x 2 ) (x 1 x
Levin Reduction and Parsimonious Reductions
 Levin Reduction and Parsimonious Reductions The reduction R in Cook s theorem (p. 266) is such that Each satisfying truth assignment for circuit R(x) corresponds to an accepting computation path for M(x).
Levin Reduction and Parsimonious Reductions The reduction R in Cook s theorem (p. 266) is such that Each satisfying truth assignment for circuit R(x) corresponds to an accepting computation path for M(x).
Lecture 6. 1 Polynomial-time algorithms for the global min-cut problem
 ORIE 633 Network Flows September 20, 2007 Lecturer: David P. Williamson Lecture 6 Scribe: Animashree Anandkumar 1 Polynomial-time algorithms for the global min-cut problem 1.1 The global min-cut problem
ORIE 633 Network Flows September 20, 2007 Lecturer: David P. Williamson Lecture 6 Scribe: Animashree Anandkumar 1 Polynomial-time algorithms for the global min-cut problem 1.1 The global min-cut problem
Practical SAT Solving
 Practical SAT Solving Lecture 1 Carsten Sinz, Tomáš Balyo April 18, 2016 NSTITUTE FOR THEORETICAL COMPUTER SCIENCE KIT University of the State of Baden-Wuerttemberg and National Laboratory of the Helmholtz
Practical SAT Solving Lecture 1 Carsten Sinz, Tomáš Balyo April 18, 2016 NSTITUTE FOR THEORETICAL COMPUTER SCIENCE KIT University of the State of Baden-Wuerttemberg and National Laboratory of the Helmholtz
Another Variant of 3sat
 Another Variant of 3sat Proposition 32 3sat is NP-complete for expressions in which each variable is restricted to appear at most three times, and each literal at most twice. (3sat here requires only that
Another Variant of 3sat Proposition 32 3sat is NP-complete for expressions in which each variable is restricted to appear at most three times, and each literal at most twice. (3sat here requires only that
Lecture 23: April 10
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 23: April 10 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 23: April 10 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
You Have an NP-Complete Problem (for Your Thesis)
 You Have an NP-Complete Problem (for Your Thesis) From Propositions 27 (p. 242) and Proposition 30 (p. 245), it is the least likely to be in P. Your options are: Approximations. Special cases. Average
You Have an NP-Complete Problem (for Your Thesis) From Propositions 27 (p. 242) and Proposition 30 (p. 245), it is the least likely to be in P. Your options are: Approximations. Special cases. Average
Notes on Natural Logic
 Notes on Natural Logic Notes for PHIL370 Eric Pacuit November 16, 2012 1 Preliminaries: Trees A tree is a structure T = (T, E), where T is a nonempty set whose elements are called nodes and E is a relation
Notes on Natural Logic Notes for PHIL370 Eric Pacuit November 16, 2012 1 Preliminaries: Trees A tree is a structure T = (T, E), where T is a nonempty set whose elements are called nodes and E is a relation
TABLEAU-BASED DECISION PROCEDURES FOR HYBRID LOGIC
 TABLEAU-BASED DECISION PROCEDURES FOR HYBRID LOGIC THOMAS BOLANDER AND TORBEN BRAÜNER Abstract. Hybrid logics are a principled generalization of both modal logics and description logics. It is well-known
TABLEAU-BASED DECISION PROCEDURES FOR HYBRID LOGIC THOMAS BOLANDER AND TORBEN BRAÜNER Abstract. Hybrid logics are a principled generalization of both modal logics and description logics. It is well-known
Sublinear Time Algorithms Oct 19, Lecture 1
 0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
Yao s Minimax Principle
 Complexity of algorithms The complexity of an algorithm is usually measured with respect to the size of the input, where size may for example refer to the length of a binary word describing the input,
Complexity of algorithms The complexity of an algorithm is usually measured with respect to the size of the input, where size may for example refer to the length of a binary word describing the input,
Lecture 5: Tuesday, January 27, Peterson s Algorithm satisfies the No Starvation property (Theorem 1)
 Com S 611 Spring Semester 2015 Advanced Topics on Distributed and Concurrent Algorithms Lecture 5: Tuesday, January 27, 2015 Instructor: Soma Chaudhuri Scribe: Nik Kinkel 1 Introduction This lecture covers
Com S 611 Spring Semester 2015 Advanced Topics on Distributed and Concurrent Algorithms Lecture 5: Tuesday, January 27, 2015 Instructor: Soma Chaudhuri Scribe: Nik Kinkel 1 Introduction This lecture covers
The Probabilistic Method - Probabilistic Techniques. Lecture 7: Martingales
 The Probabilistic Method - Probabilistic Techniques Lecture 7: Martingales Sotiris Nikoletseas Associate Professor Computer Engineering and Informatics Department 2015-2016 Sotiris Nikoletseas, Associate
The Probabilistic Method - Probabilistic Techniques Lecture 7: Martingales Sotiris Nikoletseas Associate Professor Computer Engineering and Informatics Department 2015-2016 Sotiris Nikoletseas, Associate
The Traveling Salesman Problem. Time Complexity under Nondeterminism. A Nondeterministic Algorithm for tsp (d)
 The Traveling Salesman Problem We are given n cities 1, 2,..., n and integer distances d ij between any two cities i and j. Assume d ij = d ji for convenience. The traveling salesman problem (tsp) asks
The Traveling Salesman Problem We are given n cities 1, 2,..., n and integer distances d ij between any two cities i and j. Assume d ij = d ji for convenience. The traveling salesman problem (tsp) asks
Maximizing the Spread of Influence through a Social Network Problem/Motivation: Suppose we want to market a product or promote an idea or behavior in
 Maximizing the Spread of Influence through a Social Network Problem/Motivation: Suppose we want to market a product or promote an idea or behavior in a society. In order to do so, we can target individuals,
Maximizing the Spread of Influence through a Social Network Problem/Motivation: Suppose we want to market a product or promote an idea or behavior in a society. In order to do so, we can target individuals,
monotone circuit value
 monotone circuit value A monotone boolean circuit s output cannot change from true to false when one input changes from false to true. Monotone boolean circuits are hence less expressive than general circuits.
monotone circuit value A monotone boolean circuit s output cannot change from true to false when one input changes from false to true. Monotone boolean circuits are hence less expressive than general circuits.
Tug of War Game. William Gasarch and Nick Sovich and Paul Zimand. October 6, Abstract
 Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Computing Unsatisfiable k-sat Instances with Few Occurrences per Variable
 Computing Unsatisfiable k-sat Instances with Few Occurrences per Variable Shlomo Hoory and Stefan Szeider Department of Computer Science, University of Toronto, shlomoh,szeider@cs.toronto.edu Abstract.
Computing Unsatisfiable k-sat Instances with Few Occurrences per Variable Shlomo Hoory and Stefan Szeider Department of Computer Science, University of Toronto, shlomoh,szeider@cs.toronto.edu Abstract.
On the Optimality of a Family of Binary Trees Techical Report TR
 On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
Finding Equilibria in Games of No Chance
 Finding Equilibria in Games of No Chance Kristoffer Arnsfelt Hansen, Peter Bro Miltersen, and Troels Bjerre Sørensen Department of Computer Science, University of Aarhus, Denmark {arnsfelt,bromille,trold}@daimi.au.dk
Finding Equilibria in Games of No Chance Kristoffer Arnsfelt Hansen, Peter Bro Miltersen, and Troels Bjerre Sørensen Department of Computer Science, University of Aarhus, Denmark {arnsfelt,bromille,trold}@daimi.au.dk
Lecture 5. 1 Online Learning. 1.1 Learning Setup (Perspective of Universe) CSCI699: Topics in Learning & Game Theory
 CSCI699: Topics in Learning & Game Theory Lecturer: Shaddin Dughmi Lecture 5 Scribes: Umang Gupta & Anastasia Voloshinov In this lecture, we will give a brief introduction to online learning and then go
CSCI699: Topics in Learning & Game Theory Lecturer: Shaddin Dughmi Lecture 5 Scribes: Umang Gupta & Anastasia Voloshinov In this lecture, we will give a brief introduction to online learning and then go
Structural Induction
 Structural Induction Jason Filippou CMSC250 @ UMCP 07-05-2016 Jason Filippou (CMSC250 @ UMCP) Structural Induction 07-05-2016 1 / 26 Outline 1 Recursively defined structures 2 Proofs Binary Trees Jason
Structural Induction Jason Filippou CMSC250 @ UMCP 07-05-2016 Jason Filippou (CMSC250 @ UMCP) Structural Induction 07-05-2016 1 / 26 Outline 1 Recursively defined structures 2 Proofs Binary Trees Jason
Cook s Theorem: the First NP-Complete Problem
 Cook s Theorem: the First NP-Complete Problem Theorem 37 (Cook (1971)) sat is NP-complete. sat NP (p. 113). circuit sat reduces to sat (p. 284). Now we only need to show that all languages in NP can be
Cook s Theorem: the First NP-Complete Problem Theorem 37 (Cook (1971)) sat is NP-complete. sat NP (p. 113). circuit sat reduces to sat (p. 284). Now we only need to show that all languages in NP can be
Computing Unsatisfiable k-sat Instances with Few Occurrences per Variable
 Computing Unsatisfiable k-sat Instances with Few Occurrences per Variable Shlomo Hoory and Stefan Szeider Abstract (k, s)-sat is the propositional satisfiability problem restricted to instances where each
Computing Unsatisfiable k-sat Instances with Few Occurrences per Variable Shlomo Hoory and Stefan Szeider Abstract (k, s)-sat is the propositional satisfiability problem restricted to instances where each
The Real Numbers. Here we show one way to explicitly construct the real numbers R. First we need a definition.
 The Real Numbers Here we show one way to explicitly construct the real numbers R. First we need a definition. Definitions/Notation: A sequence of rational numbers is a funtion f : N Q. Rather than write
The Real Numbers Here we show one way to explicitly construct the real numbers R. First we need a definition. Definitions/Notation: A sequence of rational numbers is a funtion f : N Q. Rather than write
Lecture l(x) 1. (1) x X
 Lecture 14 Agenda for the lecture Kraft s inequality Shannon codes The relation H(X) L u (X) = L p (X) H(X) + 1 14.1 Kraft s inequality While the definition of prefix-free codes is intuitively clear, we
Lecture 14 Agenda for the lecture Kraft s inequality Shannon codes The relation H(X) L u (X) = L p (X) H(X) + 1 14.1 Kraft s inequality While the definition of prefix-free codes is intuitively clear, we
Strong normalisation and the typed lambda calculus
 CHAPTER 9 Strong normalisation and the typed lambda calculus In the previous chapter we looked at some reduction rules for intuitionistic natural deduction proofs and we have seen that by applying these
CHAPTER 9 Strong normalisation and the typed lambda calculus In the previous chapter we looked at some reduction rules for intuitionistic natural deduction proofs and we have seen that by applying these
A relation on 132-avoiding permutation patterns
 Discrete Mathematics and Theoretical Computer Science DMTCS vol. VOL, 205, 285 302 A relation on 32-avoiding permutation patterns Natalie Aisbett School of Mathematics and Statistics, University of Sydney,
Discrete Mathematics and Theoretical Computer Science DMTCS vol. VOL, 205, 285 302 A relation on 32-avoiding permutation patterns Natalie Aisbett School of Mathematics and Statistics, University of Sydney,
Algebra homework 8 Homomorphisms, isomorphisms
 MATH-UA.343.005 T.A. Louis Guigo Algebra homework 8 Homomorphisms, isomorphisms For every n 1 we denote by S n the n-th symmetric group. Exercise 1. Consider the following permutations: ( ) ( 1 2 3 4 5
MATH-UA.343.005 T.A. Louis Guigo Algebra homework 8 Homomorphisms, isomorphisms For every n 1 we denote by S n the n-th symmetric group. Exercise 1. Consider the following permutations: ( ) ( 1 2 3 4 5
COMBINATORICS OF REDUCTIONS BETWEEN EQUIVALENCE RELATIONS
 COMBINATORICS OF REDUCTIONS BETWEEN EQUIVALENCE RELATIONS DAN HATHAWAY AND SCOTT SCHNEIDER Abstract. We discuss combinatorial conditions for the existence of various types of reductions between equivalence
COMBINATORICS OF REDUCTIONS BETWEEN EQUIVALENCE RELATIONS DAN HATHAWAY AND SCOTT SCHNEIDER Abstract. We discuss combinatorial conditions for the existence of various types of reductions between equivalence
Lecture 19: March 20
 CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 19: March 0 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They may
CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 19: March 0 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They may
CSCE 750, Fall 2009 Quizzes with Answers
 CSCE 750, Fall 009 Quizzes with Answers Stephen A. Fenner September 4, 011 1. Give an exact closed form for Simplify your answer as much as possible. k 3 k+1. We reduce the expression to a form we ve already
CSCE 750, Fall 009 Quizzes with Answers Stephen A. Fenner September 4, 011 1. Give an exact closed form for Simplify your answer as much as possible. k 3 k+1. We reduce the expression to a form we ve already
The Turing Definability of the Relation of Computably Enumerable In. S. Barry Cooper
 The Turing Definability of the Relation of Computably Enumerable In S. Barry Cooper Computability Theory Seminar University of Leeds Winter, 1999 2000 1. The big picture Turing definability/invariance
The Turing Definability of the Relation of Computably Enumerable In S. Barry Cooper Computability Theory Seminar University of Leeds Winter, 1999 2000 1. The big picture Turing definability/invariance
LECTURE 2: MULTIPERIOD MODELS AND TREES
 LECTURE 2: MULTIPERIOD MODELS AND TREES 1. Introduction One-period models, which were the subject of Lecture 1, are of limited usefulness in the pricing and hedging of derivative securities. In real-world
LECTURE 2: MULTIPERIOD MODELS AND TREES 1. Introduction One-period models, which were the subject of Lecture 1, are of limited usefulness in the pricing and hedging of derivative securities. In real-world
0/1 knapsack problem knapsack problem
 1 (1) 0/1 knapsack problem. A thief robbing a safe finds it filled with N types of items of varying size and value, but has only a small knapsack of capacity M to use to carry the goods. More precisely,
1 (1) 0/1 knapsack problem. A thief robbing a safe finds it filled with N types of items of varying size and value, but has only a small knapsack of capacity M to use to carry the goods. More precisely,
3 The Model Existence Theorem
 3 The Model Existence Theorem Although we don t have compactness or a useful Completeness Theorem, Henkinstyle arguments can still be used in some contexts to build models. In this section we describe
3 The Model Existence Theorem Although we don t have compactness or a useful Completeness Theorem, Henkinstyle arguments can still be used in some contexts to build models. In this section we describe
1) S = {s}; 2) for each u V {s} do 3) dist[u] = cost(s, u); 4) Insert u into a 2-3 tree Q with dist[u] as the key; 5) for i = 1 to n 1 do 6) Identify
![1) S = {s}; 2) for each u V {s} do 3) dist[u] = cost(s, u); 4) Insert u into a 2-3 tree Q with dist[u] as the key; 5) for i = 1 to n 1 do 6) Identify 1) S = {s}; 2) for each u V {s} do 3) dist[u] = cost(s, u); 4) Insert u into a 2-3 tree Q with dist[u] as the key; 5) for i = 1 to n 1 do 6) Identify](/thumbs/77/75720566.jpg) CSE 3500 Algorithms and Complexity Fall 2016 Lecture 17: October 25, 2016 Dijkstra s Algorithm Dijkstra s algorithm for the SSSP problem generates the shortest paths in nondecreasing order of the shortest
CSE 3500 Algorithms and Complexity Fall 2016 Lecture 17: October 25, 2016 Dijkstra s Algorithm Dijkstra s algorithm for the SSSP problem generates the shortest paths in nondecreasing order of the shortest
Sy D. Friedman. August 28, 2001
 0 # and Inner Models Sy D. Friedman August 28, 2001 In this paper we examine the cardinal structure of inner models that satisfy GCH but do not contain 0 #. We show, assuming that 0 # exists, that such
0 # and Inner Models Sy D. Friedman August 28, 2001 In this paper we examine the cardinal structure of inner models that satisfy GCH but do not contain 0 #. We show, assuming that 0 # exists, that such
Lecture 14: Basic Fixpoint Theorems (cont.)
 Lecture 14: Basic Fixpoint Theorems (cont) Predicate Transformers Monotonicity and Continuity Existence of Fixpoints Computing Fixpoints Fixpoint Characterization of CTL Operators 1 2 E M Clarke and E
Lecture 14: Basic Fixpoint Theorems (cont) Predicate Transformers Monotonicity and Continuity Existence of Fixpoints Computing Fixpoints Fixpoint Characterization of CTL Operators 1 2 E M Clarke and E
EXTENSIVE AND NORMAL FORM GAMES
 EXTENSIVE AND NORMAL FORM GAMES Jörgen Weibull February 9, 2010 1 Extensive-form games Kuhn (1950,1953), Selten (1975), Kreps and Wilson (1982), Weibull (2004) Definition 1.1 A finite extensive-form game
EXTENSIVE AND NORMAL FORM GAMES Jörgen Weibull February 9, 2010 1 Extensive-form games Kuhn (1950,1953), Selten (1975), Kreps and Wilson (1982), Weibull (2004) Definition 1.1 A finite extensive-form game
Introduction to Greedy Algorithms: Huffman Codes
 Introduction to Greedy Algorithms: Huffman Codes Yufei Tao ITEE University of Queensland In computer science, one interesting method to design algorithms is to go greedy, namely, keep doing the thing that
Introduction to Greedy Algorithms: Huffman Codes Yufei Tao ITEE University of Queensland In computer science, one interesting method to design algorithms is to go greedy, namely, keep doing the thing that
The Stackelberg Minimum Spanning Tree Game
 The Stackelberg Minimum Spanning Tree Game J. Cardinal, E. Demaine, S. Fiorini, G. Joret, S. Langerman, I. Newman, O. Weimann, The Stackelberg Minimum Spanning Tree Game, WADS 07 Stackelberg Game 2 players:
The Stackelberg Minimum Spanning Tree Game J. Cardinal, E. Demaine, S. Fiorini, G. Joret, S. Langerman, I. Newman, O. Weimann, The Stackelberg Minimum Spanning Tree Game, WADS 07 Stackelberg Game 2 players:
Homework #4. CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class
 Homework #4 CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class o Grades depend on neatness and clarity. o Write your answers with enough detail about your approach and concepts
Homework #4 CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class o Grades depend on neatness and clarity. o Write your answers with enough detail about your approach and concepts
Semantics with Applications 2b. Structural Operational Semantics
 Semantics with Applications 2b. Structural Operational Semantics Hanne Riis Nielson, Flemming Nielson (thanks to Henrik Pilegaard) [SwA] Hanne Riis Nielson, Flemming Nielson Semantics with Applications:
Semantics with Applications 2b. Structural Operational Semantics Hanne Riis Nielson, Flemming Nielson (thanks to Henrik Pilegaard) [SwA] Hanne Riis Nielson, Flemming Nielson Semantics with Applications:
Global Joint Distribution Factorizes into Local Marginal Distributions on Tree-Structured Graphs
 Teaching Note October 26, 2007 Global Joint Distribution Factorizes into Local Marginal Distributions on Tree-Structured Graphs Xinhua Zhang Xinhua.Zhang@anu.edu.au Research School of Information Sciences
Teaching Note October 26, 2007 Global Joint Distribution Factorizes into Local Marginal Distributions on Tree-Structured Graphs Xinhua Zhang Xinhua.Zhang@anu.edu.au Research School of Information Sciences
Single-Parameter Mechanisms
 Algorithmic Game Theory, Summer 25 Single-Parameter Mechanisms Lecture 9 (6 pages) Instructor: Xiaohui Bei In the previous lecture, we learned basic concepts about mechanism design. The goal in this area
Algorithmic Game Theory, Summer 25 Single-Parameter Mechanisms Lecture 9 (6 pages) Instructor: Xiaohui Bei In the previous lecture, we learned basic concepts about mechanism design. The goal in this area
Outline Introduction Game Representations Reductions Solution Concepts. Game Theory. Enrico Franchi. May 19, 2010
 May 19, 2010 1 Introduction Scope of Agent preferences Utility Functions 2 Game Representations Example: Game-1 Extended Form Strategic Form Equivalences 3 Reductions Best Response Domination 4 Solution
May 19, 2010 1 Introduction Scope of Agent preferences Utility Functions 2 Game Representations Example: Game-1 Extended Form Strategic Form Equivalences 3 Reductions Best Response Domination 4 Solution
ExpTime Tableau Decision Procedures for Regular Grammar Logics with Converse
 ExpTime Tableau Decision Procedures for Regular Grammar Logics with Converse Linh Anh Nguyen 1 and Andrzej Sza las 1,2 1 Institute of Informatics, University of Warsaw Banacha 2, 02-097 Warsaw, Poland
ExpTime Tableau Decision Procedures for Regular Grammar Logics with Converse Linh Anh Nguyen 1 and Andrzej Sza las 1,2 1 Institute of Informatics, University of Warsaw Banacha 2, 02-097 Warsaw, Poland
Algorithms for random k-sat and k-colourings of a random graph
 Algorithms for random k-sat and k-colourings of a random graph Dept of Computer Science University of Toronto Hard and Easy Distributions of SAT Problems. Mitchell, Selman, Levesque 1992 3-SAT: (x 1 x
Algorithms for random k-sat and k-colourings of a random graph Dept of Computer Science University of Toronto Hard and Easy Distributions of SAT Problems. Mitchell, Selman, Levesque 1992 3-SAT: (x 1 x
arxiv: v1 [math.lo] 24 Feb 2014
![arxiv: v1 [math.lo] 24 Feb 2014 arxiv: v1 [math.lo] 24 Feb 2014](/thumbs/74/69787486.jpg) Residuated Basic Logic II. Interpolation, Decidability and Embedding Minghui Ma 1 and Zhe Lin 2 arxiv:1404.7401v1 [math.lo] 24 Feb 2014 1 Institute for Logic and Intelligence, Southwest University, Beibei
Residuated Basic Logic II. Interpolation, Decidability and Embedding Minghui Ma 1 and Zhe Lin 2 arxiv:1404.7401v1 [math.lo] 24 Feb 2014 1 Institute for Logic and Intelligence, Southwest University, Beibei
Semantics and Verification of Software
 Semantics and Verification of Software Thomas Noll Software Modeling and Verification Group RWTH Aachen University http://moves.rwth-aachen.de/teaching/ws-1718/sv-sw/ Recap: CCPOs and Continuous Functions
Semantics and Verification of Software Thomas Noll Software Modeling and Verification Group RWTH Aachen University http://moves.rwth-aachen.de/teaching/ws-1718/sv-sw/ Recap: CCPOs and Continuous Functions
15-451/651: Design & Analysis of Algorithms October 23, 2018 Lecture #16: Online Algorithms last changed: October 22, 2018
 15-451/651: Design & Analysis of Algorithms October 23, 2018 Lecture #16: Online Algorithms last changed: October 22, 2018 Today we ll be looking at finding approximately-optimal solutions for problems
15-451/651: Design & Analysis of Algorithms October 23, 2018 Lecture #16: Online Algorithms last changed: October 22, 2018 Today we ll be looking at finding approximately-optimal solutions for problems
Recall: Data Flow Analysis. Data Flow Analysis Recall: Data Flow Equations. Forward Data Flow, Again
 Data Flow Analysis 15-745 3/24/09 Recall: Data Flow Analysis A framework for proving facts about program Reasons about lots of little facts Little or no interaction between facts Works best on properties
Data Flow Analysis 15-745 3/24/09 Recall: Data Flow Analysis A framework for proving facts about program Reasons about lots of little facts Little or no interaction between facts Works best on properties
Solving MAXSAT by Solving a Sequence of Simpler SAT Instances
 Solving MAXSAT by Solving a Sequence of Simpler SAT Instances Jessica Davies and Fahiem Bacchus Department of Computer Science University of Toronto [jdavies fbacchus] @cs.toronto.edu The MAXSAT Problem
Solving MAXSAT by Solving a Sequence of Simpler SAT Instances Jessica Davies and Fahiem Bacchus Department of Computer Science University of Toronto [jdavies fbacchus] @cs.toronto.edu The MAXSAT Problem
4 Martingales in Discrete-Time
 4 Martingales in Discrete-Time Suppose that (Ω, F, P is a probability space. Definition 4.1. A sequence F = {F n, n = 0, 1,...} is called a filtration if each F n is a sub-σ-algebra of F, and F n F n+1
4 Martingales in Discrete-Time Suppose that (Ω, F, P is a probability space. Definition 4.1. A sequence F = {F n, n = 0, 1,...} is called a filtration if each F n is a sub-σ-algebra of F, and F n F n+1
Node betweenness centrality: the definition.
 Brandes algorithm These notes supplement the notes and slides for Task 11. They do not add any new material, but may be helpful in understanding the Brandes algorithm for calculating node betweenness centrality.
Brandes algorithm These notes supplement the notes and slides for Task 11. They do not add any new material, but may be helpful in understanding the Brandes algorithm for calculating node betweenness centrality.
CS599: Algorithm Design in Strategic Settings Fall 2012 Lecture 6: Prior-Free Single-Parameter Mechanism Design (Continued)
 CS599: Algorithm Design in Strategic Settings Fall 2012 Lecture 6: Prior-Free Single-Parameter Mechanism Design (Continued) Instructor: Shaddin Dughmi Administrivia Homework 1 due today. Homework 2 out
CS599: Algorithm Design in Strategic Settings Fall 2012 Lecture 6: Prior-Free Single-Parameter Mechanism Design (Continued) Instructor: Shaddin Dughmi Administrivia Homework 1 due today. Homework 2 out
Maximum Contiguous Subsequences
 Chapter 8 Maximum Contiguous Subsequences In this chapter, we consider a well-know problem and apply the algorithm-design techniques that we have learned thus far to this problem. While applying these
Chapter 8 Maximum Contiguous Subsequences In this chapter, we consider a well-know problem and apply the algorithm-design techniques that we have learned thus far to this problem. While applying these
Online Algorithms SS 2013
 Faculty of Computer Science, Electrical Engineering and Mathematics Algorithms and Complexity research group Jun.-Prof. Dr. Alexander Skopalik Online Algorithms SS 2013 Summary of the lecture by Vanessa
Faculty of Computer Science, Electrical Engineering and Mathematics Algorithms and Complexity research group Jun.-Prof. Dr. Alexander Skopalik Online Algorithms SS 2013 Summary of the lecture by Vanessa
Binary Decision Diagrams
 Binary Decision Diagrams Hao Zheng Department of Computer Science and Engineering University of South Florida Tampa, FL 33620 Email: zheng@cse.usf.edu Phone: (813)974-4757 Fax: (813)974-5456 Hao Zheng
Binary Decision Diagrams Hao Zheng Department of Computer Science and Engineering University of South Florida Tampa, FL 33620 Email: zheng@cse.usf.edu Phone: (813)974-4757 Fax: (813)974-5456 Hao Zheng
Probability. An intro for calculus students P= Figure 1: A normal integral
 Probability An intro for calculus students.8.6.4.2 P=.87 2 3 4 Figure : A normal integral Suppose we flip a coin 2 times; what is the probability that we get more than 2 heads? Suppose we roll a six-sided
Probability An intro for calculus students.8.6.4.2 P=.87 2 3 4 Figure : A normal integral Suppose we flip a coin 2 times; what is the probability that we get more than 2 heads? Suppose we roll a six-sided
LECTURE 3: FREE CENTRAL LIMIT THEOREM AND FREE CUMULANTS
 LECTURE 3: FREE CENTRAL LIMIT THEOREM AND FREE CUMULANTS Recall from Lecture 2 that if (A, φ) is a non-commutative probability space and A 1,..., A n are subalgebras of A which are free with respect to
LECTURE 3: FREE CENTRAL LIMIT THEOREM AND FREE CUMULANTS Recall from Lecture 2 that if (A, φ) is a non-commutative probability space and A 1,..., A n are subalgebras of A which are free with respect to
10.1 Elimination of strictly dominated strategies
 Chapter 10 Elimination by Mixed Strategies The notions of dominance apply in particular to mixed extensions of finite strategic games. But we can also consider dominance of a pure strategy by a mixed strategy.
Chapter 10 Elimination by Mixed Strategies The notions of dominance apply in particular to mixed extensions of finite strategic games. But we can also consider dominance of a pure strategy by a mixed strategy.
1 Online Problem Examples
 Comp 260: Advanced Algorithms Tufts University, Spring 2018 Prof. Lenore Cowen Scribe: Isaiah Mindich Lecture 9: Online Algorithms All of the algorithms we have studied so far operate on the assumption
Comp 260: Advanced Algorithms Tufts University, Spring 2018 Prof. Lenore Cowen Scribe: Isaiah Mindich Lecture 9: Online Algorithms All of the algorithms we have studied so far operate on the assumption
MAT 4250: Lecture 1 Eric Chung
 1 MAT 4250: Lecture 1 Eric Chung 2Chapter 1: Impartial Combinatorial Games 3 Combinatorial games Combinatorial games are two-person games with perfect information and no chance moves, and with a win-or-lose
1 MAT 4250: Lecture 1 Eric Chung 2Chapter 1: Impartial Combinatorial Games 3 Combinatorial games Combinatorial games are two-person games with perfect information and no chance moves, and with a win-or-lose
Binary Decision Diagrams
 Binary Decision Diagrams Hao Zheng Department of Computer Science and Engineering University of South Florida Tampa, FL 33620 Email: zheng@cse.usf.edu Phone: (813)974-4757 Fax: (813)974-5456 Hao Zheng
Binary Decision Diagrams Hao Zheng Department of Computer Science and Engineering University of South Florida Tampa, FL 33620 Email: zheng@cse.usf.edu Phone: (813)974-4757 Fax: (813)974-5456 Hao Zheng
Optimal Satisficing Tree Searches
 Optimal Satisficing Tree Searches Dan Geiger and Jeffrey A. Barnett Northrop Research and Technology Center One Research Park Palos Verdes, CA 90274 Abstract We provide an algorithm that finds optimal
Optimal Satisficing Tree Searches Dan Geiger and Jeffrey A. Barnett Northrop Research and Technology Center One Research Park Palos Verdes, CA 90274 Abstract We provide an algorithm that finds optimal
Optimal Stopping. Nick Hay (presentation follows Thomas Ferguson s Optimal Stopping and Applications) November 6, 2008
 (presentation follows Thomas Ferguson s and Applications) November 6, 2008 1 / 35 Contents: Introduction Problems Markov Models Monotone Stopping Problems Summary 2 / 35 The Secretary problem You have
(presentation follows Thomas Ferguson s and Applications) November 6, 2008 1 / 35 Contents: Introduction Problems Markov Models Monotone Stopping Problems Summary 2 / 35 The Secretary problem You have
Game Theory: Normal Form Games
 Game Theory: Normal Form Games Michael Levet June 23, 2016 1 Introduction Game Theory is a mathematical field that studies how rational agents make decisions in both competitive and cooperative situations.
Game Theory: Normal Form Games Michael Levet June 23, 2016 1 Introduction Game Theory is a mathematical field that studies how rational agents make decisions in both competitive and cooperative situations.
Algorithmic Game Theory and Applications. Lecture 11: Games of Perfect Information
 Algorithmic Game Theory and Applications Lecture 11: Games of Perfect Information Kousha Etessami finite games of perfect information Recall, a perfect information (PI) game has only 1 node per information
Algorithmic Game Theory and Applications Lecture 11: Games of Perfect Information Kousha Etessami finite games of perfect information Recall, a perfect information (PI) game has only 1 node per information
Principles of Program Analysis: Algorithms
 Principles of Program Analysis: Algorithms Transparencies based on Chapter 6 of the book: Flemming Nielson, Hanne Riis Nielson and Chris Hankin: Principles of Program Analysis. Springer Verlag 2005. c
Principles of Program Analysis: Algorithms Transparencies based on Chapter 6 of the book: Flemming Nielson, Hanne Riis Nielson and Chris Hankin: Principles of Program Analysis. Springer Verlag 2005. c
CSE 21 Winter 2016 Homework 6 Due: Wednesday, May 11, 2016 at 11:59pm. Instructions
 CSE 1 Winter 016 Homework 6 Due: Wednesday, May 11, 016 at 11:59pm Instructions Homework should be done in groups of one to three people. You are free to change group members at any time throughout the
CSE 1 Winter 016 Homework 6 Due: Wednesday, May 11, 016 at 11:59pm Instructions Homework should be done in groups of one to three people. You are free to change group members at any time throughout the
Orthogonality to the value group is the same as generic stability in C-minimal expansions of ACVF
 Orthogonality to the value group is the same as generic stability in C-minimal expansions of ACVF Will Johnson February 18, 2014 1 Introduction Let T be some C-minimal expansion of ACVF. Let U be the monster
Orthogonality to the value group is the same as generic stability in C-minimal expansions of ACVF Will Johnson February 18, 2014 1 Introduction Let T be some C-minimal expansion of ACVF. Let U be the monster
A class of coherent risk measures based on one-sided moments
 A class of coherent risk measures based on one-sided moments T. Fischer Darmstadt University of Technology November 11, 2003 Abstract This brief paper explains how to obtain upper boundaries of shortfall
A class of coherent risk measures based on one-sided moments T. Fischer Darmstadt University of Technology November 11, 2003 Abstract This brief paper explains how to obtain upper boundaries of shortfall
CTL Model Checking. Goal Method for proving M sat σ, where M is a Kripke structure and σ is a CTL formula. Approach Model checking!
 CMSC 630 March 13, 2007 1 CTL Model Checking Goal Method for proving M sat σ, where M is a Kripke structure and σ is a CTL formula. Approach Model checking! Mathematically, M is a model of σ if s I = M
CMSC 630 March 13, 2007 1 CTL Model Checking Goal Method for proving M sat σ, where M is a Kripke structure and σ is a CTL formula. Approach Model checking! Mathematically, M is a model of σ if s I = M
2 Deduction in Sentential Logic
 2 Deduction in Sentential Logic Though we have not yet introduced any formal notion of deductions (i.e., of derivations or proofs), we can easily give a formal method for showing that formulas are tautologies:
2 Deduction in Sentential Logic Though we have not yet introduced any formal notion of deductions (i.e., of derivations or proofs), we can easily give a formal method for showing that formulas are tautologies:
The potential function φ for the amortized analysis of an operation on Fibonacci heap at time (iteration) i is given by the following equation:
 Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600 127, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 01 Advanced Data Structures
Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600 127, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 01 Advanced Data Structures
October An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution.
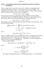 October 13..18.4 An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution. We now assume that the reservation values of the bidders are independently and identically distributed
October 13..18.4 An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution. We now assume that the reservation values of the bidders are independently and identically distributed
Satisfaction in outer models
 Satisfaction in outer models Radek Honzik joint with Sy Friedman Department of Logic Charles University logika.ff.cuni.cz/radek CL Hamburg September 11, 2016 Basic notions: Let M be a transitive model
Satisfaction in outer models Radek Honzik joint with Sy Friedman Department of Logic Charles University logika.ff.cuni.cz/radek CL Hamburg September 11, 2016 Basic notions: Let M be a transitive model
MAC Learning Objectives. Learning Objectives (Cont.)
 MAC 1140 Module 12 Introduction to Sequences, Counting, The Binomial Theorem, and Mathematical Induction Learning Objectives Upon completing this module, you should be able to 1. represent sequences. 2.
MAC 1140 Module 12 Introduction to Sequences, Counting, The Binomial Theorem, and Mathematical Induction Learning Objectives Upon completing this module, you should be able to 1. represent sequences. 2.
Chapter 7: SAMPLING DISTRIBUTIONS & POINT ESTIMATION OF PARAMETERS
 Chapter 7: SAMPLING DISTRIBUTIONS & POINT ESTIMATION OF PARAMETERS Part 1: Introduction Sampling Distributions & the Central Limit Theorem Point Estimation & Estimators Sections 7-1 to 7-2 Sample data
Chapter 7: SAMPLING DISTRIBUTIONS & POINT ESTIMATION OF PARAMETERS Part 1: Introduction Sampling Distributions & the Central Limit Theorem Point Estimation & Estimators Sections 7-1 to 7-2 Sample data
5 Deduction in First-Order Logic
 5 Deduction in First-Order Logic The system FOL C. Let C be a set of constant symbols. FOL C is a system of deduction for the language L # C. Axioms: The following are axioms of FOL C. (1) All tautologies.
5 Deduction in First-Order Logic The system FOL C. Let C be a set of constant symbols. FOL C is a system of deduction for the language L # C. Axioms: The following are axioms of FOL C. (1) All tautologies.
MAS115: R programming Lecture 3: Some more pseudo-code and Monte Carlo estimation Lab Class: for and if statements, input
 MAS115: R programming Lecture 3: Some more pseudo-code and Monte Carlo estimation Lab Class: for and if statements, input The University of Sheffield School of Mathematics and Statistics Aims Introduce
MAS115: R programming Lecture 3: Some more pseudo-code and Monte Carlo estimation Lab Class: for and if statements, input The University of Sheffield School of Mathematics and Statistics Aims Introduce
Additional questions for chapter 3
 Additional questions for chapter 3 1. Let ξ 1, ξ 2,... be independent and identically distributed with φθ) = IEexp{θξ 1 })
Additional questions for chapter 3 1. Let ξ 1, ξ 2,... be independent and identically distributed with φθ) = IEexp{θξ 1 })
Handout 4: Deterministic Systems and the Shortest Path Problem
 SEEM 3470: Dynamic Optimization and Applications 2013 14 Second Term Handout 4: Deterministic Systems and the Shortest Path Problem Instructor: Shiqian Ma January 27, 2014 Suggested Reading: Bertsekas
SEEM 3470: Dynamic Optimization and Applications 2013 14 Second Term Handout 4: Deterministic Systems and the Shortest Path Problem Instructor: Shiqian Ma January 27, 2014 Suggested Reading: Bertsekas
GAME THEORY. Department of Economics, MIT, Follow Muhamet s slides. We need the following result for future reference.
 14.126 GAME THEORY MIHAI MANEA Department of Economics, MIT, 1. Existence and Continuity of Nash Equilibria Follow Muhamet s slides. We need the following result for future reference. Theorem 1. Suppose
14.126 GAME THEORY MIHAI MANEA Department of Economics, MIT, 1. Existence and Continuity of Nash Equilibria Follow Muhamet s slides. We need the following result for future reference. Theorem 1. Suppose
6.231 DYNAMIC PROGRAMMING LECTURE 3 LECTURE OUTLINE
 6.21 DYNAMIC PROGRAMMING LECTURE LECTURE OUTLINE Deterministic finite-state DP problems Backward shortest path algorithm Forward shortest path algorithm Shortest path examples Alternative shortest path
6.21 DYNAMIC PROGRAMMING LECTURE LECTURE OUTLINE Deterministic finite-state DP problems Backward shortest path algorithm Forward shortest path algorithm Shortest path examples Alternative shortest path
ECON Chapter 6: Economic growth: The Solow growth model (Part 1)
 ECON3102-005 Chapter 6: Economic growth: The Solow growth model (Part 1) Neha Bairoliya Spring 2014 Motivations Why do countries grow? Why are there poor countries? Why are there rich countries? Can poor
ECON3102-005 Chapter 6: Economic growth: The Solow growth model (Part 1) Neha Bairoliya Spring 2014 Motivations Why do countries grow? Why are there poor countries? Why are there rich countries? Can poor
15-451/651: Design & Analysis of Algorithms November 9 & 11, 2015 Lecture #19 & #20 last changed: November 10, 2015
 15-451/651: Design & Analysis of Algorithms November 9 & 11, 2015 Lecture #19 & #20 last changed: November 10, 2015 Last time we looked at algorithms for finding approximately-optimal solutions for NP-hard
15-451/651: Design & Analysis of Algorithms November 9 & 11, 2015 Lecture #19 & #20 last changed: November 10, 2015 Last time we looked at algorithms for finding approximately-optimal solutions for NP-hard
An effective perfect-set theorem
 An effective perfect-set theorem David Belanger, joint with Keng Meng (Selwyn) Ng CTFM 2016 at Waseda University, Tokyo Institute for Mathematical Sciences National University of Singapore The perfect
An effective perfect-set theorem David Belanger, joint with Keng Meng (Selwyn) Ng CTFM 2016 at Waseda University, Tokyo Institute for Mathematical Sciences National University of Singapore The perfect
0.1 Equivalence between Natural Deduction and Axiomatic Systems
 0.1 Equivalence between Natural Deduction and Axiomatic Systems Theorem 0.1.1. Γ ND P iff Γ AS P ( ) it is enough to prove that all axioms are theorems in ND, as MP corresponds to ( e). ( ) by induction
0.1 Equivalence between Natural Deduction and Axiomatic Systems Theorem 0.1.1. Γ ND P iff Γ AS P ( ) it is enough to prove that all axioms are theorems in ND, as MP corresponds to ( e). ( ) by induction
Quadrant marked mesh patterns in 123-avoiding permutations
 Quadrant marked mesh patterns in 23-avoiding permutations Dun Qiu Department of Mathematics University of California, San Diego La Jolla, CA 92093-02. USA duqiu@math.ucsd.edu Jeffrey Remmel Department
Quadrant marked mesh patterns in 23-avoiding permutations Dun Qiu Department of Mathematics University of California, San Diego La Jolla, CA 92093-02. USA duqiu@math.ucsd.edu Jeffrey Remmel Department
CMSC 858F: Algorithmic Game Theory Fall 2010 Introduction to Algorithmic Game Theory
 CMSC 858F: Algorithmic Game Theory Fall 2010 Introduction to Algorithmic Game Theory Instructor: Mohammad T. Hajiaghayi Scribe: Hyoungtae Cho October 13, 2010 1 Overview In this lecture, we introduce the
CMSC 858F: Algorithmic Game Theory Fall 2010 Introduction to Algorithmic Game Theory Instructor: Mohammad T. Hajiaghayi Scribe: Hyoungtae Cho October 13, 2010 1 Overview In this lecture, we introduce the
On Existence of Equilibria. Bayesian Allocation-Mechanisms
 On Existence of Equilibria in Bayesian Allocation Mechanisms Northwestern University April 23, 2014 Bayesian Allocation Mechanisms In allocation mechanisms, agents choose messages. The messages determine
On Existence of Equilibria in Bayesian Allocation Mechanisms Northwestern University April 23, 2014 Bayesian Allocation Mechanisms In allocation mechanisms, agents choose messages. The messages determine
Essays on Some Combinatorial Optimization Problems with Interval Data
 Essays on Some Combinatorial Optimization Problems with Interval Data a thesis submitted to the department of industrial engineering and the institute of engineering and sciences of bilkent university
Essays on Some Combinatorial Optimization Problems with Interval Data a thesis submitted to the department of industrial engineering and the institute of engineering and sciences of bilkent university
Lecture Quantitative Finance Spring Term 2015
 implied Lecture Quantitative Finance Spring Term 2015 : May 7, 2015 1 / 28 implied 1 implied 2 / 28 Motivation and setup implied the goal of this chapter is to treat the implied which requires an algorithm
implied Lecture Quantitative Finance Spring Term 2015 : May 7, 2015 1 / 28 implied 1 implied 2 / 28 Motivation and setup implied the goal of this chapter is to treat the implied which requires an algorithm
Reconfiguration of Satisfying Assignments and Subset Sums: Easy to Find, Hard to Connect
 Reconfiguration of Satisfying Assignments and Subset Sums: Easy to Find, Hard to Connect x x in x in x in y z y in F F z in t F F z in t F F t 0 y out T y out T z out T Jean Cardinal, Erik Demaine, David
Reconfiguration of Satisfying Assignments and Subset Sums: Easy to Find, Hard to Connect x x in x in x in y z y in F F z in t F F z in t F F t 0 y out T y out T z out T Jean Cardinal, Erik Demaine, David
A Translation of Intersection and Union Types
 A Translation of Intersection and Union Types for the λ µ-calculus Kentaro Kikuchi RIEC, Tohoku University kentaro@nue.riec.tohoku.ac.jp Takafumi Sakurai Department of Mathematics and Informatics, Chiba
A Translation of Intersection and Union Types for the λ µ-calculus Kentaro Kikuchi RIEC, Tohoku University kentaro@nue.riec.tohoku.ac.jp Takafumi Sakurai Department of Mathematics and Informatics, Chiba
