IT PAYS TO KNOW. FRAUD IN TRAVEL PAYMENTS.
|
|
|
- Clarence Anderson
- 5 years ago
- Views:
Transcription
1 IT PAYS TO KNOW. FRAUD IN TRAVEL PAYMENTS. enett International exposes fraud in travel payments and best practices travel companies can use to limit its impact.
2 2
3 A WORD FROM OUR CEO. The introduction of the Boeing 747 in 1970 was a major step in democratising travel, as it brought air travel within the reach of greater portions of the population. Online travel agencies (OTAs) began to appear in the mid-1990s. In 1996, Expedia launched as a division of Microsoft and Booking.com started. The following year, Priceline.com commenced operations, and Ctrip started in The emergence of these giant OTAs and the digitisation of travel meant greater opportunities to connect consumers with unique travel experiences. Today s consumers have greater control and choice than ever before. Exotic holidays, previously considered once in a lifetime trips, can now be booked and paid for on smartphones during a lunch break. But this comes at a cost for the travel industry. Unfortunately it makes travel intermediaries especially vulnerable to fraud. And the problem has grown with the increase in volume of travel and the shift toward online bookings across the globe. The game has changed. As of 2017, the impact of fraud for travel intermediaries was already estimated to be USD21B. By 2020 the impact of fraud is expected to reach USD25B, driven by both a migration from offline to online and an uptick in the rate of fraud. But there is good news. Travel intermediaries can take action, including in the way they pay suppliers, to reduce the incidence and impact of fraud as well as aid recovery if fraud occurs. enett s vision is to work with the industry and our customers to take the cost and complexity out of travel payments. So, we engaged Edgar, Dunn & Company, a global payments focused consultancy, to investigate fraud in travel payments. And identify best practices travel intermediaries can implement to limit the occurrence and impact of fraud. This report presents key results of the research, which included 210+ interviews with travel intermediaries across the world, expert interviews, and insights from our own fraud team. We want to help the industry understand and reduce fraud, so they can stay focused on growing their own businesses. It pays to know. I hope you enjoy the read. Anthony Hynes Managing Director & CEO enett International. enett s vision is to take the cost and complexity out of travel payments. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 3
4 WHAT WE D LIKE YOU TO KNOW. The travel industry is particularly susceptible to fraud, based on seven factors that make it both attractive and vulnerable to the efforts of fraudsters. Fraud can occur at various stages of the value chain in C2B and B2B payments. There are eight key types of fraud that can occur at many points in the travel value chain. New fraud patterns are appearing more regularly, which makes controlling fraud an ongoing effort best coordinated across the industry. Direct and indirect impacts from fraud are observable and include financial as well as nonfinancial components. Indirect costs of fraud are approximately 2.5x the value of direct losses. The total impact of fraud for travel intermediaries is currently around USD21B. Total fraud impact for travel intermediaries is expected to exceed USD25B in 2020, with close to USD11B being borne by OTAs. Fraud was cited as a concern in relation to receiving payments by 57% of travel intermediaries interviewed for this research. 29% of respondents identified foreign credit cards as the highest fraud risk when receiving payments. 35% of respondents identified web as the channel with the highest fraud risk when receiving payments. Fraud risk is also a concern for 60% of organisations when making payments to suppliers. The three most common types of fraud cited in relation to paying suppliers are: stolen payment method details, cyber breach of online booking platforms, and stolen security credentials for online payment facilities. Applying industry best practices outlined in this report can help reduce fraud risk, and improve the rate of recovery if fraud occurs. Best practices cover the full range of people, processes and technology. Quick wins to reduce fraud risk and impact in B2B travel payments include the use of payment methods that provide a breadth of transaction controls and recovery mechanisms should fraud occur. C2B: Consumer-to-business B2B: Business-to-business 4
5 ONLINE ALLOWS FRAUDSTERS TO OPERATE GLOBALLY AND FIND FRAUD OPPORTUNITIES ANYWHERE. Expert interview, conducted by Edgar, Dunn & Company.
6 TABLE OF CONTENTS. FRAUD IN TRAVEL TYPES OF FRAUD IMPACT OF FRAUD Travel is especially susceptible to fraud Payment flows and fraud areas in the travel value chain 8 10 Types of fraud in the travel value chain Other key concepts in relation to fraud Types of impacts from fraud Direct losses from fraud Indirect costs of fraud Recent developments in travel payment fraud 16 Total costs of fraud for intermediated travel payments 24 Fraud related losses and costs are expected to increase for OTAs
7 CONTROLLING FRAUD IN CLOSING Best practices for controlling fraud 26 To sum up Mapping best practices to intermediated travel value chain 30 About this research 34 Mapping best practices to fraud types 31 enett VANs minimise fraud risk and aid recovery
8 PART 1 FRAUD IN TRAVEL TRAVEL IS ESPECIALLY SUSCEPTIBLE TO FRAUD. 1. HIGH VALUE ITEMS. 2. GLOBAL REACH AND DIGITAL ANONYMITY. 3. RAPID CONSUMPTION. MERCHANT S TIME TO ASSESS FRAUD RISK Travel services are often high value. This makes them very attractive for resale on the black market and particularly on so-called dark net marketplaces. Silk Road, for example, was an early dark net marketplace, operating from 2011, with various versions shut down by authorities in 2013 and 2014 before the latest iteration went offline in Contemporary versions of Silk Road offer a wide range of sophisticated services that include escrow with crypto currencies, seller feedback mechanisms, and other capabilities similar to mainstream marketplaces. The internet provides global reach, companies can provide instant fulfilment, and tools such as VPNs (Virtual Private Networks) and Tor enable protection of identity online. These tools and attributes increase the pool of potential targets for fraudsters, decrease the chance of apprehension, and provide additional opportunities to trade in fraudulent services. Merchants in the travel industry often have very little time to assess fraud risk, especially on last minute bookings or in the case of changes to bookings. Some merchants choose to reject last minute bookings and changes, but fraudsters target such weaknesses regardless. And with the rise of last minute bookings, the sales cycle is only getting faster. HIGH Financial Risk LOW INSTANT <1 HOUR 6 HOURS 24 HOURS Virtual gift cards Online gaming Last minute travel Other ticketing Music and ebooks General ecommerce Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 8
9 4. BARRIERS TO RECOVERY. 5. DISINCENTIVES FOR PREVENTION. 6. RELATIVELY LOW MARGINS. 7. NUMBER AND DIVERSITY OF SUPPLIERS. Unlike some physical goods, travel services are often much harder to recover once fraudulently stolen and consumed. This means there is less incentive to pursue fraudsters, potentially reducing the risk of getting caught. This increases the attractiveness of travel as a fraud target. Some fraud minimisation tools can increase friction in transactions with legitimate customers and suppliers, impacting sales, which travel intermediaries wish to avoid. This can lead to decisions to lower protection efforts, resulting in greater fraud risk and related losses. Travel agencies are typically high volume low margin businesses, which makes them vulnerable to the financial impacts of fraud. It can take a large volume of sales to offset the cost of a single fraud event. Online travel agents in particular tend to have a wide range of suppliers, with large OTAs typically listing hundreds of thousands of properties, hundreds of airlines, and dozens of other suppliers across many countries and jurisdictions. Managing a large global supplier set brings increased risk of fraud in B2B payments, with financial and non-financial risks for OTAs. 9
10 PART 1 FRAUD IN TRAVEL PAYMENT FLOWS AND FRAUD AREAS IN THE TRAVEL VALUE CHAIN. There are three main types of payment flows in the travel value chain, each of which can be targeted by fraudsters Merchant model payment flows include two or more separate payments, first from the traveller to the travel intermediary, who usually functions as the merchant of record, and subsequently makes payment(s) to the travel supplier. Agency model payment flows are still part of an intermediated booking, but the payment itself flows through to the travel supplier, typically without the intermediary acting as merchant of record. (The travel supplier may then make separate payments, such as commissions, back to the travel intermediary.) Travellers can also book direct with a travel supplier, without using a travel intermediary. There may be multiple travel intermediaries, such as consolidators, included in some instances, and additional payments may occur between those travel intermediaries. Travel intermediaries and travel suppliers may both be victims of fraud in B2B payments but such fraud is not widely reported, making it more complex to detect, prevent or resolve. The remainder of this report focuses specifically on fraud within intermediated travel payments.
11 SIMPLIFIED VIEW OF THE TRAVEL VALUE CHAIN Merchant model payment flow Intermediaries Merchant model payment flow Travellers Agency model payment flow Direct booking payment flow Suppliers Consumer-to-business (C2B) payments Fraud can occur when the end traveller or fraudster is making a payment to a travel intermediary or travel supplier. Business-to-business (B2B) payments Fraud can occur when the travel intermediary is making a payment to a travel supplier. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 11
12 PART 2 TYPES OF FRAUD TYPES OF FRAUD IN THE TRAVEL VALUE CHAIN. There are eight main types of fraud in the intermediated travel value chain, split between C2B and B2B payments. C2B PAYMENTS FRAUD TYPE DESCRIPTION PERPETRATOR(S) 1 Use of stolen payment details Also known as card-not-present fraud, this category is now the main concern for travel intermediaries when receiving payments. A fraudster using stolen payment details, such as credit card information, purchases goods or services and either uses it themselves or sells it on to others (who may not know of the fraud event). The ultimate financial impact typically sits with the merchant of record, which may be the travel intermediary. Criminal fraudster 2 Personal ID theft and impersonation Includes two sub-types: account takeover fraud and account opening fraud. Fraudsters employing account takeover will seek personal information to take control of an account that is capable of making bookings or payments, while account opening fraud relates to creating a new account with a new profile. Financial victims of this fraud may be travel intermediaries where the account is with the intermediary, although banks may offer compensation where a fraudster was able to create a new account with the bank itself. Criminal fraudster 3 Chargeback fraud Also known as friendly fraud, this relates to a specific type of fraud that happens after a legitimate traveller has used legitimate payment details and has consumed the travel service purchased, and then triggers a chargeback against the travel intermediary or travel supplier. Travel intermediaries or suppliers may struggle to prove the original payment was legitimate or may not be able to challenge the chargeback and can become financial victims of chargeback fraud. End traveller 12
13 B2B PAYMENTS FRAUD TYPE DESCRIPTION PERPETRATOR(S) 4 Stolen security credentials An external fraudster can use phishing s or other social engineering techniques to dupe an unwitting employee in a travel intermediary into sharing security credentials for a payment platform operated by their employer. The fraudster then uses this platform to transfer funds to one or more external accounts or to make purchases of items or services that can be sold later. Travel intermediaries may find it very difficult to recover such funds, and support or compensation from banks will depend on the specific event as well as local rules and regulations. Criminal fraudster 5 Intermediary impersonation A fraudster can take control of a travel intermediary s account and purchase travel services from a travel supplier on the intermediary s account. Typically, a fraudster will use the professional registration details of a travel intermediary but may change other information to enable the later sale of the fraudulently obtained services, for example via the dark net. Unfortunately a travel intermediary may not be aware their account has been taken over, and recovery of funds used by the fraudster may be difficult or impossible. Criminal fraudster 6 Payment method fraud It is relatively common for travel intermediaries to share payment details, such as information about cards used for procurement, with trusted travel suppliers. Travel supplier information may be compromised, or a rogue employee at the travel intermediary or travel supplier may choose to dishonestly use a card outside of agreed terms to obtain a financial advantage. Travel intermediaries may be able to resolve a dispute with a supplier, and chargeback processes may be available in instances where the payment method was a physical or virtual credit card. Virtual cards, such as enett VANs, can also include controls that a travel intermediary can employ to reduce or eliminate their misuse. Rogue employee, criminal fraudster 7 Fictitious billing Criminal fraudsters or rogue employees may introduce fake charges into the payment system of a travel intermediary, generally via a supplier. The fraud may be initiated from the travel supplier only, or there may be collusion from rogue employees at the travel intermediary. Transaction amounts may be kept below a known threshold value to conceal the fraud for as long as possible. Rogue employee, criminal fraudster 8 Price manipulation This complex and damaging fraud event usually includes collusion between multiple parties. Typically, a travel supplier will raise their own prices on the platform of the travel intermediary, while another party, such as a fraudster or a rogue employee at the travel intermediary, pays for these services at the inflated price via stolen card details. This results in a transfer of value to the owner or operator of the travel supplier. This process may continue for weeks or months before it is discovered, at which time it may disappear. Travel intermediaries will typically lose money on two fronts: chargebacks from the holder of the stolen card, plus loss of funds transferred to the travel supplier. Owner/operator of travel supplier, rogue employee, criminal fraudster 13
14 PART 2 TYPES OF FRAUD OTHER KEY CONCEPTS IN RELATION TO FRAUD. Phishing, social engineering, and data breaches. Low value testing. Fraudsters may seek to gain access to payment information, such as details of a credit card or the payment system of a travel intermediary, through several mechanisms. Approaches directed towards employees include phishing s or other social engineering techniques. Phishing s look and sound genuine and may seem to come from a friend, family member, colleague, boss, customer, supplier, utility company, bank or other service provider. Similar approaches may include phone calls that appear to be from a genuine source, such as an internet service provider. Communications in these cases are carefully designed to trick unsuspecting employees into: Providing some or all details needed by a fraudster to impersonate them; Gaining access to payment details or systems; Installing malware that will provide fraudsters with ongoing access to details or systems. Reducing the risk of attacks aimed at people should focus on education of employees. Other approaches may be directed towards systems (or processes) and typically include a hack to gain information (such as credit card details) that may be sold, or information that may be used to gain access that can be exploited later for financial gain. Such data breaches may have direct financial consequences and may also result in reputational damage to the affected organisations. A standard part of many fraudulent activities, especially those involving credit cards, is a single low value test. A fraudster will typically test a credit card with a low value transaction, usually for an amount assumed to be under system-based thresholds, for example with a purchase via legitimate online music vendors, app stores, or similar merchants. Higher value purchases may follow until the card is exhausted, suspended, or cancelled. 14
15 THERE IS A HUGE DIFFERENCE BETWEEN PERCEPTION AND REALITY [OF FRAUD] AT TRAVEL COMPANIES. Expert interview, conducted by Edgar, Dunn & Company. 15
16 PART 2 TYPES OF FRAUD RECENT DEVELOPMENTS IN TRAVEL PAYMENT FRAUD. Fraudsters targeting the travel industry are becoming more sophisticated in their methods, utilising social media and technological advances in their attacks on travel intermediaries. Recent developments in travel payment fraud include fake hotels and inflated room prices, crimeas-a-service, and large numbers of low value transactions. Fake hotels. A fraudster will list a property and use stolen credit cards to make bookings via the OTA s website. The OTA makes payment to the fake hotel but will then receive chargebacks for the bookings. The fake hotel will have withdrawn all the funds paid by the OTA and won t respond to any contact attempts. OTAs need to ensure they are verifying the legitimacy of a new supplier during onboarding and perform appropriate due diligence to limit the risk of this type of fraud. Inflated room prices. There are instances of room prices being inflated dramatically followed by a spike in booking volume. This indicates collusion between a hotel and a fraudster. The hotel will raise the cost of their room and the fraudster will then use stolen card details to book rooms via an OTA. The OTA will receive chargebacks but the hotel will provide documentation related to the guest to avoid being debited for the fraud. OTAs need to implement a check for price spikes/booking increases to identify this type of fraud. It s recommended OTAs also review their supplier contracts regarding liabilities for this type of fraud. Tickets to attractions. Fraudsters may use stolen credit card details to purchase tickets to tourist attractions. These tickets may then be on-sold via a social media platform for a discounted price. In this situation the ticket is either utilised, leaving the tourist attraction operator or travel intermediary out of pocket after a chargeback, or when the tourist arrives at the attraction the operator advises the ticket has been cancelled as it has been reported as fraud, leaving the tourist out of pocket, not to mention a bad holiday experience. This type of fraud occurs with velocity and in a short time window. OTAs need to be alert to volume increases to a particular supplier. 16
17 Pop-up shops on social media. Crime-as-a-service. Brute force card number generation and testing. Low value flood on credit cards. (instead of one large transaction) Some fraudsters are setting up social media accounts masquerading as shop fronts and offering cheap, last minute flights. They ask travellers to pay via a method that is difficult or impossible to trace and then use stolen card details to purchase the ticket for the tourist. By the time the fraud is reported by the valid credit card holder, the services may have already been provided to the unwitting tourist. A recent trend in organised crime has also arrived in travel. Law enforcement has targeted fake online travel agencies, specialising in purchasing airline tickets with stolen card information for other criminals providing them a service. One criminal enterprise offered financial services, fake documents, and fraudulently purchased tickets. Rather than seeking to find and compromise a known existing credit card, fraudsters are using brute force card generation and testing mechanisms that automatically and rapidly create variations of credit card details and test them with low value transactions. Once a working card is found, the fraudster receives an alert and can begin to use the card. After an initial low value test, a large volume of low value charges may be posted against a compromised credit card in quick succession, either via automated or manual means. Some fraudsters share information with communities of people who may use the card details to make small purchases, such as add-ons in mobile apps or games. The large number and low value of transactions, combined with the direct and indirect (i.e. effort) costs of chargebacks or other recovery mechanisms related to each transaction may mean these types of fraud events require bespoke approaches to prevent and recover from them. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 17
18 PART 3 IMPACT OF FRAUD TYPES OF IMPACTS FROM FRAUD. 2.5X The costs of fraud include direct losses resulting from fraud, and indirect costs such as revenue loss, higher operating expenses, and reputational damage. Relatively few organisations measure indirect costs of fraud in a comprehensive manner, yet such costs are generally 2.5x higher than direct fraud losses. INDIRECT COSTS OF FRAUD ARE 2.5X HIGHER THAN DIRECT FRAUD LOSSES 1 Direct losses 2 Indirect costs Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 18
19 MOST THAT SUFFER FROM FRAUD DON T HAVE THE SYSTEMS IN PLACE TO EVEN KNOW ABOUT IT. Expert interview, conducted by Edgar, Dunn & Company. A note on the measurement of fraud impacts There are two main approaches for measuring direct losses and indirect costs from fraud: frequency based and value based assessments. Value based assessments express impacts as a percentage of gross sales or travel spend to arrive at a total financial impact. This is a harder metric to track than fraud frequency and is therefore less reported, but it is arguably a better reflection of fraud impacts overall. For this reason, the value based approach was taken in this report. 19
20 PART 3 IMPACT OF FRAUD DIRECT LOSSES FROM FRAUD. DIRECT LOSSES VERSUS INDIRECT COSTS OF FRAUD AMOUNT (USD) OF DIRECT FRAUD LOSS PER USD10,000 IN SALES* 1 Direct losses Physical travel intermediary Online travel intermediaries overall APAC AMS EMEA APAC AMS EMEA $26 to $39 $33 to $52 $39 to $59 $76 to $134 $92 to $151 $61 to $101 2 Indirect costs OTAs specifically APAC AMS EMEA $84 to $134 $101 to $151 $67 to $101 $0 $50 $100 $150 Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018). Direct fraud losses as a portion of sales vary significantly between physical and online travel intermediaries, with online travel intermediaries facing rates of fraud approximately twice as high as their offline counterparts. *Sales is defined as reported total travel volume. APAC: Asia Pacific AMS: North and South America EMEA: Europe, Middle East, and Africa 20
21 ESTIMATES OF FRAUD RATES AND DIRECT LOSS BY REGION (USD) 1.50% AMS $0.9B Fraud rate 1.00% EMEA $0.7B APAC $0.9B Mid-point fraud rate of 106bps Fraud is global and fraudsters simply target weak, not small agents or those in a particular country. 0.50% $600M $1B Direct losses from fraud Expert interview, conducted by Edgar, Dunn & Company. Note: This chart relates to direct costs of fraud only and does not include indirect losses. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018). 21
22 PART 3 IMPACT OF FRAUD INDIRECT COSTS OF FRAUD. DIRECT LOSSES VERSUS INDIRECT COSTS OF FRAUD The indirect costs of fraud, which include revenue loss, higher operating expenses, and reputational damage are estimated to be 2.5x the losses directly attributable to fraud. Revenue loss. 1 Direct losses 2 Indirect costs Revenue loss may include booking attempts rejected (at C2B transaction stage) or lost due to delays in reviews of last minute bookings. For travel intermediaries this can also include listing fewer properties, airlines, activities and other services on offer due to concerns about fraud in B2B payments. This may result in less choice for customers and potentially losing business to competitors. The right balance between protection from fraud without rejecting or impeding legitimate travellers and suppliers typically depends on company-specific fraud capabilities and risk appetite. Higher operational expenses. Travel businesses manually review a much higher proportion of transactions than in other industries, leading to significantly higher operating costs. Edgar, Dunn & Company estimates 20-30% of purchase attempts by end travellers are manually reviewed for fraud. Travel companies in emerging online markets, such as Asia Pacific, the Middle East, and Africa, are more likely to conduct manual reviews than their counterparts in established markets like Europe and North America. Effort and cost related to recovering from fraud events, for example via chargebacks, also increase operational expenses. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018). 22
23 Reputational damage and other costs. Lasting reputational damage and consequent financial impacts can result from customers having booking attempts rejected or cancelled, or from customer and supplier exposure to fraud events. Reputational damage may be increased by regulatory violations, including events that later feed fraud attempts, such as data breaches. Regulatory violations may also result in fines or costly remediation requirements. Each of these categories is hard to identify, isolate, and measure. Fortunately, a reduction in direct losses from fraud typically brings with it a multiplied benefit from a reduction in indirect costs. Travel companies will know their own market intimately and may be uncomfortable expanding globally, [they] may choose to manually review all cross border bookings for example. Expert interview, conducted by Edgar, Dunn & Company. 23
24 PART 3 IMPACT OF FRAUD TOTAL COSTS OF FRAUD FOR INTERMEDIATED TRAVEL PAYMENTS. USD2.5B Edgar, Dunn & Company estimates direct loss from fraud for travel intermediaries at approximately USD6.0B, with USD2.5B borne by OTAs. OVERVIEW OF 2017 GLOBAL TRAVEL SPEND AND FRAUD COST ESTIMATES (USD) $232B $78B OTA APAC $2.5B $0.9B $373B $6.3B $2.3B Online USD6.3B $904B Intermediated bookings $3.7B $9.3B $142B TMC & Other $75B AMS Indirect costs, based on a 2.5x multiplier of direct losses, are approximately USD15.0B for travel intermediaries overall, and USD6.3B for OTAs specifically. $6.0B $15.0B $531B Physical $2.3B $1.2B $3.0B $0.9B $2.3B $79B $5.8B EMEA Total travel spend $0.7B Direct losses from fraud Indirect costs of fraud $1.8B Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. Note: Figures may not add exactly to displayed totals due to rounding. APAC: Asia Pacific AMS: North and South America EMEA: Europe, Middle East, and Africa 24
25 PART 3 IMPACT OF FRAUD FRAUD RELATED LOSSES AND COSTS ARE EXPECTED TO INCREASE FOR OTAS. USD3.1B Our research concluded that direct fraud losses are likely to continue to rise, and that regional spread is not expected to change materially. Indirect costs related to fraud as a multiple of direct losses from fraud have typically trended up, and these costs will continue to be significant even without further increases. By 2020, the total cost of fraud for OTAs is expected to increase by approximately 24% to almost USD11B, including USD3.1B in direct losses and USD7.8B in indirect costs. That s almost half of the entire cost for all travel intermediaries, which is expected to reach USD25B by DIRECT LOSSES BY 2020 USD7.8B INDIRECT COSTS BY 2020 FORECAST INCREASE IN FRAUD COSTS FOR OTAS (USD) Direct fraud losses are forecast to increase with a knock-on effect for indirect costs resulting in major increase in impacts for OTAs. +24% $10.9B $7.8B $8.8B $3.9B EMEA AMS APAC $2.5B $0.9B $0.9B $0.7B $3.1B $1.1B $1.2B $0.8B EMEA AMS APAC $6.3B $2.3B $2.3B $1.8B $2.8B $3.0B $2.0B EMEA AMS APAC $3.2B $3.2B $2.5B $4.2B $2.8B Note: Figures may not add exactly to displayed totals due to rounding. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 25
26 PART 4 CONTROLLING FRAUD BEST PRACTICES FOR CONTROLLING FRAUD. Efforts to control fraud can focus on decreasing the risk of fraud occurring, lowering potential impact, and aiding recovery from fraud once it has occurred. There are twelve observed best practices travel intermediaries can follow to control fraud. BEST PRACTICE SOME TIPS 1 Encourage customer registration A customer registration process that includes contact details, nationality, date of birth, payment details and other information allows companies to develop positive lists and negative lists for later monitoring and filtering of transactions. Such lists can also form the foundation for configurations and refinement of fraud control tools and processes, and can enable collaboration with other organisations (by sharing positive and negative lists).* 2 Implement and refine fraud control tools Authentication tools, customer history records, supplier history, device tracking and use of multi-merchant data can enable near-real-time profiling of transactions and inform risk assessment decisions. Systems-based fraud rules can then be refined to best balance the need to control fraud with the desire for higher conversion rates and smooth transaction flows. 3 Communicate at point of sale Prominent displays at point of sale of the penalties fraudsters can face, including steps that can destroy the value of the fraudulently obtained travel service before it is consumed, have been shown to discourage fraudsters and reassure legitimate customers. 4 Establish rules and practices Limiting the number of declined transactions allowed per payment card, establishing a minimum timeframe from time of booking to use of travel service (e.g. departure), identification of higher risk third party purchases and manual reviews of higher risk bookings can all lower fraud rates. Listings from travel suppliers and subsequent payments to them may also be subjected to additional scrutiny if established rules indicate reason for suspicion. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. * Positive list: includes legitimate customers with no fraud record. Negative list: includes fraudsters or customers with a high fraud risk. 26
27 BEST PRACTICE SOME TIPS 5 Create comprehensive reporting and analysis of fraud patterns Rapid detection and reporting on fraud can aid recovery and inform prevention efforts. Reporting should include information such as IP addresses, account numbers, time of booking, routes or locations included, suppliers, price paid, item price fluctuation history, time to departure or stay, and other key data points. This information should then be analysed to identify fraud trends and inform activities, such as stricter controls for high-risk transactions. Effective fraud analysis can lead to less friction for legitimate customers and a decrease in fraud, false positives, and manual reviews. 6 Use payment methods that offer protection and recovery mechanisms Virtual cards (sometimes known as VCCs) generally allow various controls to be set that help significantly decrease the risk of fraud and also include mechanisms for recovering from fraud. However, not all VCCs are the same. enett Virtual Account Numbers (VANs) allow users to define booking and payment parameters, minimising the risk of fraud when paying travel suppliers. VANs also offer sophisticated chargeback capabilities, meaning funds may be recovered should fraud occur. 7 Educate employees about fraud, especially phishing attacks Social engineering attacks can include phishing attacks, such as bogus s that look like they are from trusted sources (manager, colleague, supplier, friend, etc.) or legitimate external providers (police, bank, utility company, etc.). Raising awareness through education is key to avoiding falling prey to such attacks and preventing a company s payment details or a person s login credentials from falling into the wrong hands. 8 Collaborate to detect fraud Internal collaboration, between company departments, and external collaboration, with trade associations or other legitimate players in the value chain, can help create greater system-wide reduction in fraud risk. Such a reduction can come about as a result of better fraud pattern recognition and blocking of known fraudsters. Networked sharing of information, for example via payment providers covering travel as well as other industries, can increase opportunities for identifying risk and preventing fraud. Some providers offer retrospective alerts, for example providing an alert for a transaction that was originally approved but the card is later reported as used in fraud, so steps can be taken before a service is consumed. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 27
28 BEST PRACTICE SOME TIPS 9 Know your supplier Travel intermediaries face a balancing act between offering a wide range of travel services and the need for a degree of due diligence in relation to travel suppliers. Travel intermediaries should consider a level of background or reference checking to satisfy themselves that a travel supplier legally exists and is who they say. Even a trusted relationship requires due care and attention as rogue employees may enter organisations at any time or fraudsters may infiltrate payment-related systems and platforms. 10 Include payments in cyber security scope Travel intermediaries should be diligent about employing good cyber security practices and include payment platforms and methods in their scope. This should typically cover requirements for password complexity and change frequency, tracking of login patterns for unusual activity (e.g. locations or IP addresses), use of multi-factor authentication, and account lockouts after failed attempts or account inactivity. 11 Apply internal controls Travel intermediaries should apply bank level internal control principles, including payment processes that include maker-checker controls and segregation of duties. No single employee should have complete control over transactions. Instead, a maker should enter the transaction, followed by a checker who verifies the data and authorises the transaction. Other important controls include reporting independence, whereby the maker should be made to report to an officer who is not in charge of the specific transaction authorisation. This supports red flagging of transactions without fear of retribution and reprimand from an immediate supervisor. 12 Show value of fraud control Mechanisms should be in place to evaluate fraud protection and recovery performance by assessing the benefits of fraud controls versus costs. This should typically include an assessment of value detection rate for fraud, comparing the proportion of fraud detected to fraud loss incurred; percentage of transactions wrongly identified as fraudulent (false positives); as well as frictional costs imposed on customers or the business from manual reviews, validations, or lower conversion rates. Such data should be tracked over time to identify and implement opportunities for improvement. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. 28
29 TRAVEL INTERMEDIARIES FACE FRAUD RISKS AT MULTIPLE STEPS OF THE VALUE CHAIN AND TRANSACTION SEQUENCE Travellers Intermediaries Suppliers Make Payment Accept Payment Make Payment Accept Payment Best practices are mapped to the intermediated travel value chain, its payment flows, and key fraud types in the following pages.
30 PART 4 CONTROLLING FRAUD MAPPING BEST PRACTICES TO INTERMEDIATED TRAVEL VALUE CHAIN. Travel intermediaries face fraud risks at multiple steps of the value chain and transaction sequence. The twelve best practices identified map to each of these steps and, in combination with company-specific evaluations of implementation effort, can serve to lower end-to-end fraud losses as well as related indirect costs. BEST PRACTICE EFFORT NEEDED TO IMPLEMENT ACCEPT PAYMENT INTERNAL PROCESSES MAKE PAYMENT 1. Encourage customer registration High 2. Implement and refine fraud control tools High 3. Communicate at the point of sale Low 4. Establish rules and practices High 5. Create comprehensive reporting and analysis of fraud patterns* Medium 6. Use payment methods that offer protection and recovery mechanisms 7. Educate employees about fraud, especially phishing attacks 8. Collaborate to detect fraud Medium Low High enett VANs offer controls to limit fraud risk and also provide mechanisms for fraud recovery. Implementation is straightforward and benefits can be significant. 9. Know your supplier Medium 10. Include payments in cyber security scope 11. Apply internal controls 12. Show value of fraud control Medium Medium Medium Assessing and demonstrating the end-to-end benefits of fraud control can help to better inform decisions related to investments in fraud control. * Effectiveness depends on how well foundational controls and reporting work. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. Some benefit Very high benefit 30
31 PART 4 CONTROLLING FRAUD MAPPING BEST PRACTICES TO FRAUD TYPES. Key best practices identified are typically applicable to various types of fraud, with a coordinated effort required to tackle fraud end-to-end. BEST PRACTICE USE OF STOLEN PAYMENT DETAILS PERSONAL ID THEFT AND IMPERSONATION CHARGEBACK FRAUD STOLEN SECURITY CREDENTIALS INTERMEDIARY IMPERSONATION PAYMENT METHOD FRAUD FICTITIOUS BILLING PRICE MANIPULATION 1. Encourage customer registration 2. Implement and refine fraud control tools 3. Communicate at the point of sale 4. Establish rules and practices 5. Create comprehensive reporting and analysis of fraud patterns* 6. Use payment methods that offer protection and recovery mechanisms 7. Educate employees about fraud, especially phishing attacks 8. Collaborate to detect fraud 9. Know your supplier 10. Include payments in cyber security scope 11. Apply internal controls 12. Show value of fraud control Demonstrating the value of fraud control by itself doesn t serve to decrease the probability and impact of specific types of fraud but instead helps to identify, implement, and refine practices that reduce fraud, forming a key component in overall fraud management. * Effectiveness depends on how well foundational controls and reporting work. Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018), enett International research. Some benefit Very high benefit 31
32 PART 4 CONTROLLING FRAUD ENETT VANS CAN CONTRIBUTE TO MINIMISING THE RISK OF FRAUD AND PROVIDE RECOVERY MECHANISMS. What are enett VANs? enett Virtual Account Numbers (VANs) are 16 digit Mastercard numbers that travel intermediaries can use to pay their suppliers quickly, efficiently, and with less risk. A unique number is used for each new booking or payment transaction. How do they help to protect travel intermediaries against fraud? enett VANs include a wide range of control mechanisms that significantly reduce the risk of the card being used for purposes other than intended, substantially reducing the risk of fraud. If fraud does occur, even when it is unrelated to compromising of the payment type itself, travel intermediaries can leverage chargeback mechanisms to recover funds that may otherwise stay lost to fraud. How do enett VANs protect against fraud? A range of controls are available for transactions (via individual VANs) to help significantly reduce fraud when making payments to travel suppliers. Single-use only VANs can be created as single use for a specific transaction. Once the VAN has been issued and charged by a supplier it can no longer be used. This addresses the risk of misuse if VAN details fall into the wrong hands. Card specific restrictions VAN value, activation date, expiry date and other details can be defined on setup and apply as they would for any other credit card payment, limiting the scope for misuse. Enhanced card controls Merchant category restrictions can be applied to limit VAN use to a single category (e.g. hotels). Additional options are available to limit the use of a VAN to a single merchant, further enhancing security and limiting opportunities for misuse. How do enett VANs help to recover from fraud? enett VANs include chargeback protection via the Mastercard guarantee for travel intermediaries of all types. What are chargebacks and how do they work? Chargebacks provide a mechanism to potentially recover funds from a merchant who should not have received them. Causes for triggering a chargeback toward a merchant may include the occurrence of fraud in the payment toward the merchant, charging higher than agreed rates, or failure to supply the services that have been paid for, such as in the event of a sudden airline bankruptcy. 32
33 PART 5 IN CLOSING TO SUM UP... Size doesn t really matter travel agencies of any size are being hit. Expert interview, conducted by Edgar, Dunn & Company. Time to act? Using payment methods that offer fraud protection and recovery mechanisms can help travel intermediaries reduce the incidence and impact of fraud as well as aid recovery when it occurs. enett VANs allow users to define booking and payment parameters, minimising the risk of fraud when paying travel suppliers. And sophisticated chargeback capabilities means funds may be recovered should fraud occur. For more on how enett VANs reduce the risk of fraud when paying travel suppliers and maximise recovery of funds, visit For more on enett VANs, visit what-are-vans Want to find out more? If you d like to find out more about fraud detection and prevention, or want us to explain the findings of this research in more detail, contact us via at service@enett.com 33
34 PART 5 IN CLOSING ABOUT THIS RESEARCH INTERVIEWS WITH TRAVEL INTERMEDIARIES AND INDUSTRY EXPERTS enett International engaged Edgar, Dunn & Company in late 2017 to investigate fraud in travel payments via primary and secondary research. This included interviews with 210+ travel intermediaries, interviews with industry experts across the world, input from enett s fraud team, and a review of the existing fraud management body of knowledge. Global (Selling >10% to customers outside the domestic region) 56% GEOGRAPHIC MARKET PRESENCE 30% 14% Domestic only (Selling mainly to domestic customers >90%) Regional (Selling >10% to non-domestic customers) 34% APAC REGION 33% EMEA 33% AMS employees (medium) 47% COMPANY SIZE 14% 39% employees (small) 250 employees and more (large) Both 15% JOB 74% IMPLICATION 11% Receive payments from customers Make payment to travel suppliers APAC: Asia Pacific AMS: North and South America EMEA: Europe, Middle East, and Africa Source: Edgar, Dunn & Company Fraud in Travel Payments (January 2018). 34
35
36 Copyright 2018 enett International (Singapore) Pte Ltd (enett). This document is based on enett s assumptions and research. It may not take into account other factors that will impact your financial situation and is intended as a guide only. enett VANs terms and conditions apply. In Australia, enett (AFSL ) is not authorised to provide financial product advice. This document does not take into account your objectives, financial situation or needs. You should consider the appropriateness of the information in light of your own circumstances and the Product Disclosure Statement before acting.
A Review of Actual Fraud Cases in 2017 FRAUD REVIEW
 A Review of Actual Fraud Cases in 2017 FRAUD REVIEW Contents Introduction 3 Fraud Snapshot 4 Case Studies Credit Card Fraud 5 Business Email Compromise Fraud 6 Payroll Fraud 7 Supplier Fraud 8 Outlook
A Review of Actual Fraud Cases in 2017 FRAUD REVIEW Contents Introduction 3 Fraud Snapshot 4 Case Studies Credit Card Fraud 5 Business Email Compromise Fraud 6 Payroll Fraud 7 Supplier Fraud 8 Outlook
Kasasa Protect. FAQ and Product Overview
 Kasasa Protect FAQ and Product Overview Kasasa Protect... 3 Key Contact Info... 3 Included Benefits... 3 Credit Reporting... 4 Monthly Credit Score & Plotter... 4 24/7 Credit Monitoring... 5 Full-Service
Kasasa Protect FAQ and Product Overview Kasasa Protect... 3 Key Contact Info... 3 Included Benefits... 3 Credit Reporting... 4 Monthly Credit Score & Plotter... 4 24/7 Credit Monitoring... 5 Full-Service
Year-end 2016 fraud update: Payment cards, remote banking and cheque
 Year-end 2016 update: Payment cards, remote banking and cheque 30 March 2017 1. Introduction Financial Fraud Action UK (FFA UK) is responsible for leading the collective fight against in the UK payments
Year-end 2016 update: Payment cards, remote banking and cheque 30 March 2017 1. Introduction Financial Fraud Action UK (FFA UK) is responsible for leading the collective fight against in the UK payments
THE STATE OF CHARGEBACKS: 2018 REPORT
 THE STATE OF CHARGEBACKS: 2018 REPORT THE STATE OF CHARGEBACKS: 2018 REPORT 1 Contents Executive Summary... 2 Chargeback Management... 4 Chargeback Rates... 4 Chargeback Prevention and Challenges.................................
THE STATE OF CHARGEBACKS: 2018 REPORT THE STATE OF CHARGEBACKS: 2018 REPORT 1 Contents Executive Summary... 2 Chargeback Management... 4 Chargeback Rates... 4 Chargeback Prevention and Challenges.................................
Why your PSP should be your best defence against fraud
 Why your PSP should be your best defence against fraud July 2017 processing.paysafe.com Why your PSP should be your best defence against fraud If recent crime statistics have taught us anything, it s that
Why your PSP should be your best defence against fraud July 2017 processing.paysafe.com Why your PSP should be your best defence against fraud If recent crime statistics have taught us anything, it s that
January to June 2016 fraud update: Payment cards, remote banking and cheque
 January to update: Payment cards, remote banking and cheque October 1. Introduction Financial Fraud Action UK (FFA UK) is responsible for leading the collective fight against in the UK payments industry.
January to update: Payment cards, remote banking and cheque October 1. Introduction Financial Fraud Action UK (FFA UK) is responsible for leading the collective fight against in the UK payments industry.
STEPPING INTO THE A GUIDE TO CYBER AND DATA INSURANCE BREACH
 STEPPING INTO THE A GUIDE TO CYBER AND DATA INSURANCE BREACH 2 THE CYBER AND DATA RISK TO YOUR BUSINESS This digital guide will help you find out more about the potential cyber and data risks to your business,
STEPPING INTO THE A GUIDE TO CYBER AND DATA INSURANCE BREACH 2 THE CYBER AND DATA RISK TO YOUR BUSINESS This digital guide will help you find out more about the potential cyber and data risks to your business,
Synthetic Identities. Are you chasing invisible footprints? 2018 Fair Isaac Corporation. All rights reserved.
 Synthetic Identities Are you chasing invisible footprints? 2018 Fair Isaac Corporation. All rights reserved. Synthetic Identities A combination of fictitious and potentially stolen personally identifiable
Synthetic Identities Are you chasing invisible footprints? 2018 Fair Isaac Corporation. All rights reserved. Synthetic Identities A combination of fictitious and potentially stolen personally identifiable
By now you would ve heard about The Connected Practice. But what is it, exactly?
 Contents Introduction Late payment impact...3 Emerging payment trends...3 Types of fraud... 4 Adding value... 5 Seizing opportunities... 5 Adding to your knowledge... 6 Invoice Payments...7 Offering solutions...
Contents Introduction Late payment impact...3 Emerging payment trends...3 Types of fraud... 4 Adding value... 5 Seizing opportunities... 5 Adding to your knowledge... 6 Invoice Payments...7 Offering solutions...
Credit fraud is a serious problem for airlines and travel agents alike
 Reducing Fraudulent Transactions and Chargeback Agent Debit Memos Credit fraud is a serious problem for airlines and travel agents alike Jennifer Watkins, ARC s Director, Credit Card Services & Fraud Prevention
Reducing Fraudulent Transactions and Chargeback Agent Debit Memos Credit fraud is a serious problem for airlines and travel agents alike Jennifer Watkins, ARC s Director, Credit Card Services & Fraud Prevention
2017 annual fraud update:
 2017 annual update: Payment cards, remote banking, cheque and authorised push payment scams March 2018 The threat from is always changing, but the finance industry is continuously enhancing its response,
2017 annual update: Payment cards, remote banking, cheque and authorised push payment scams March 2018 The threat from is always changing, but the finance industry is continuously enhancing its response,
Insuring your online world, even when you re offline. Masterpiece Cyber Protection
 Insuring your online world, even when you re offline Masterpiece Cyber Protection Protect your online information from being an open network 97% of Chubb clients who had a claim paid were highly satisfied
Insuring your online world, even when you re offline Masterpiece Cyber Protection Protect your online information from being an open network 97% of Chubb clients who had a claim paid were highly satisfied
minimise card fraud in your business.
 minimise card fraud in your business. First National Bank Tanzania Limited - a subsidiary of FirstRand Limited. A Registered Commercial Bank in Tanzania (CBA00050). There is a real possibility that your
minimise card fraud in your business. First National Bank Tanzania Limited - a subsidiary of FirstRand Limited. A Registered Commercial Bank in Tanzania (CBA00050). There is a real possibility that your
Recognizing Credit Card Fraud
 1 Recognizing Credit Card Fraud Credit card fraud happens when consumers give their credit card number to unfamiliar individuals, when cards are lost or stolen, when mail is diverted from the intended
1 Recognizing Credit Card Fraud Credit card fraud happens when consumers give their credit card number to unfamiliar individuals, when cards are lost or stolen, when mail is diverted from the intended
Additional Information on the Dirty Dozen
 Additional Information on the Dirty Dozen 1. Identity Theft Topping this year s list Dirty Dozen list is identity theft. In response to growing identity theft concerns, the IRS has embarked on a comprehensive
Additional Information on the Dirty Dozen 1. Identity Theft Topping this year s list Dirty Dozen list is identity theft. In response to growing identity theft concerns, the IRS has embarked on a comprehensive
FIGHTING FRAUD & CHARGEBACKS 5 STRATEGIES FOR WINNING
 FIGHTING FRAUD & CHARGEBACKS 5 STRATEGIES FOR WINNING 2 2016 was a strong year for online sales growth. But fraud and chargebacks more than kept pace. The good news? You can dramatically reduce losses
FIGHTING FRAUD & CHARGEBACKS 5 STRATEGIES FOR WINNING 2 2016 was a strong year for online sales growth. But fraud and chargebacks more than kept pace. The good news? You can dramatically reduce losses
CONSUMER FRAUD GLOBAL HEADQUARTERS THE GREGOR BUILDING 716 WEST AVE AUSTIN, TX USA
 CONSUMER FRAUD GLOBAL HEADQUARTERS THE GREGOR BUILDING 716 WEST AVE AUSTIN, TX 78701-2727 USA VII. CREDIT CARD FRAUD SCHEMES Introduction Consumers make purchases using credit every day. Credit card companies
CONSUMER FRAUD GLOBAL HEADQUARTERS THE GREGOR BUILDING 716 WEST AVE AUSTIN, TX 78701-2727 USA VII. CREDIT CARD FRAUD SCHEMES Introduction Consumers make purchases using credit every day. Credit card companies
Banking Title Application Fraud: The Enemy at the Gates
 WHITE PAPER Banking Title Application Fraud: The Enemy at the Gates It is a fraud to borrow what we are unable to pay. Publilius Syrus, first century B.C. ii Contents Overview... 1 What Is Application
WHITE PAPER Banking Title Application Fraud: The Enemy at the Gates It is a fraud to borrow what we are unable to pay. Publilius Syrus, first century B.C. ii Contents Overview... 1 What Is Application
Visa s Approach to Card Fraud and Identity Theft
 Visa s Approach to Card Fraud and Identity Theft Paul Russinoff June 7, 2007 Discussion Topics Visa s Comprehensive Security Approach Multiple Layers Commitment to Cardholders Consumer Tips Protecting
Visa s Approach to Card Fraud and Identity Theft Paul Russinoff June 7, 2007 Discussion Topics Visa s Comprehensive Security Approach Multiple Layers Commitment to Cardholders Consumer Tips Protecting
Bulletin 40 December 2003
 Bulletin 40 December 2003 Online and Offline Credit Card Fraud: hazards for small business In this issue: a discussion of the issues arising for small business merchants accepting credit card payments
Bulletin 40 December 2003 Online and Offline Credit Card Fraud: hazards for small business In this issue: a discussion of the issues arising for small business merchants accepting credit card payments
27 th Year of Publication. A monthly publication from South Indian Bank. To kindle interest in economic affairs... To empower the student community...
 Experience Next Generation Banking A monthly publication from South Indian Bank To kindle interest in economic affairs... To empower the student community... www.southindianbank.com Student s corner ho2099@sib.co.in
Experience Next Generation Banking A monthly publication from South Indian Bank To kindle interest in economic affairs... To empower the student community... www.southindianbank.com Student s corner ho2099@sib.co.in
Aligning Risk Management with CU Business Strategy
 Aligning Risk Management with CU Business Strategy Managing your most pressing risks CUNA Mutual Group Proprietary Reproduction, Adaptation or Distribution Prohibited 2016 CUNA Mutual Group, All Rights
Aligning Risk Management with CU Business Strategy Managing your most pressing risks CUNA Mutual Group Proprietary Reproduction, Adaptation or Distribution Prohibited 2016 CUNA Mutual Group, All Rights
protect fraudulent against transactions your business Introduction What is a fraudulent transaction? Merchant Responsibilities Card Present
 protect your business against fraudulent transactions Reg. No. 1929/001225/06. Introduction There is a real possibility that your business could be a victim of fraudulent card transactions given the sophistication
protect your business against fraudulent transactions Reg. No. 1929/001225/06. Introduction There is a real possibility that your business could be a victim of fraudulent card transactions given the sophistication
Customer Protection Policy (Unauthorized Electronic Banking Transactions)
 Customer Protection Policy (Unauthorized Electronic Banking Transactions) Customer Protection Policy Electronic Banking Transactions Page 1 of 12 1) Introduction: PMC Bank is committed to provide superior
Customer Protection Policy (Unauthorized Electronic Banking Transactions) Customer Protection Policy Electronic Banking Transactions Page 1 of 12 1) Introduction: PMC Bank is committed to provide superior
SAFEGUARDING YOUR CHILD S FUTURE. Child Identity Theft. Protecting Your Child s Identity
 SAFEGUARDING YOUR CHILD S FUTURE Child Identity Theft Child identity theft happens when someone uses a minor s personal information to commit fraud. A thief may steal and use a child s information to get
SAFEGUARDING YOUR CHILD S FUTURE Child Identity Theft Child identity theft happens when someone uses a minor s personal information to commit fraud. A thief may steal and use a child s information to get
The Stark Reality of Synthetic ID Fraud How to Battle the Leading Identity Fraud Tactic in The Digital Age
 The Stark Reality of Synthetic ID Fraud How to Battle the Leading Identity Fraud Tactic in The Digital Age Scoping Out Synthetic ID Fraud In the 18 years since synthetic identity fraud emerged as a significant
The Stark Reality of Synthetic ID Fraud How to Battle the Leading Identity Fraud Tactic in The Digital Age Scoping Out Synthetic ID Fraud In the 18 years since synthetic identity fraud emerged as a significant
Loaded Everyday card terms and conditions
 Loaded Everyday card terms and conditions Posted Online: 1 October 2013 Effective: 15 October 2013 The Loaded TM range of cards is issued by Kiwibank Limited and distributed by various organisations, including
Loaded Everyday card terms and conditions Posted Online: 1 October 2013 Effective: 15 October 2013 The Loaded TM range of cards is issued by Kiwibank Limited and distributed by various organisations, including
State of Card Fraud: 2018
 State of Card Fraud: 2018 A deep dive into the evolution of card fraud + industry benchmark data for financial institutions. Stopping Fraud at the Speed of Data Continuing the trend of prior years, the
State of Card Fraud: 2018 A deep dive into the evolution of card fraud + industry benchmark data for financial institutions. Stopping Fraud at the Speed of Data Continuing the trend of prior years, the
Up for Grabs: Taking Charge of Your Digital Identity
 Up for Grabs: Taking Charge of Your Digital Identity AARP Wisconsin Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.022
Up for Grabs: Taking Charge of Your Digital Identity AARP Wisconsin Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.022
Your Guide to. Credit Card Skimming: How to Spot and Avoid Fraudulent Charges
 Your Guide to Credit Card Skimming: How to Spot and Avoid Fraudulent Charges The term skimming, as applied to credit cards, involves stealing card account data during a legitimate transaction. It is then
Your Guide to Credit Card Skimming: How to Spot and Avoid Fraudulent Charges The term skimming, as applied to credit cards, involves stealing card account data during a legitimate transaction. It is then
FRAUD ALERT! Cyber-Crime Impact on IDENTITY THEFT ACCOUNT FRAUD. n Minimize Risk n Vigilance Works n Fraud Prevention Tools
 FRAUD ALERT! Cyber-Crime Impact on IDENTITY THEFT & ACCOUNT FRAUD n Minimize Risk n Vigilance Works n Fraud Prevention Tools As you probably already know one of the three major consumer credit reporting
FRAUD ALERT! Cyber-Crime Impact on IDENTITY THEFT & ACCOUNT FRAUD n Minimize Risk n Vigilance Works n Fraud Prevention Tools As you probably already know one of the three major consumer credit reporting
Fay Servicing, LLC 901 S. 2 nd St., Suite 201 Springfield, IL 62704
 RE: Identity Theft Claim You recently notified Fay Servicing, LLC that you are the victim of identity theft with respect to the above referenced loan (also referred to in this notice as the debt or account
RE: Identity Theft Claim You recently notified Fay Servicing, LLC that you are the victim of identity theft with respect to the above referenced loan (also referred to in this notice as the debt or account
White Paper. Banking Application Fraud: The Enemy at the Gates. It is a fraud to borrow what we are unable to pay. Publilius Syrus, first century B.C.
 White Paper Banking Application Fraud: The Enemy at the Gates It is a fraud to borrow what we are unable to pay. Publilius Syrus, first century B.C. Contents Overview... 1 What Is Application Fraud?...
White Paper Banking Application Fraud: The Enemy at the Gates It is a fraud to borrow what we are unable to pay. Publilius Syrus, first century B.C. Contents Overview... 1 What Is Application Fraud?...
Card and Account Security. Important information about your card and account.
 Card and Account Security. Important information about your card and account. Card and Account Security 1. Peace of mind As a Bendigo Bank customer you can bank with confidence knowing that, if you take
Card and Account Security. Important information about your card and account. Card and Account Security 1. Peace of mind As a Bendigo Bank customer you can bank with confidence knowing that, if you take
Your defence toolkit. How to combat the cyber threat
 Your defence toolkit How to combat the cyber threat Contents The threat of cyber crime 4 How UK businesses are targeted 6 Case studies 8 Why cyber security is so important to manufacturers now 10 The
Your defence toolkit How to combat the cyber threat Contents The threat of cyber crime 4 How UK businesses are targeted 6 Case studies 8 Why cyber security is so important to manufacturers now 10 The
Ethoca Alerts. Pioneering a Better Way to Avoid Chargebacks & Stop Fraud Loss
 Ethoca Alerts Pioneering a Better Way to Avoid Chargebacks & Stop Fraud Loss The Issuer-Online Merchant Divide Before Ethoca, online merchants and card issuers relied on their own fraud detection systems
Ethoca Alerts Pioneering a Better Way to Avoid Chargebacks & Stop Fraud Loss The Issuer-Online Merchant Divide Before Ethoca, online merchants and card issuers relied on their own fraud detection systems
Bramalea City Centre FashioniCITY Rewards Club Program Terms
 Bramalea City Centre FashioniCITY Rewards Club Program Terms This agreement provides the terms and conditions under which individuals may participate (as members ) in the Bramalea City Centre / FashioniCITY
Bramalea City Centre FashioniCITY Rewards Club Program Terms This agreement provides the terms and conditions under which individuals may participate (as members ) in the Bramalea City Centre / FashioniCITY
Up for Grabs: Taking Charge of Your Digital Identity
 Up for Grabs: Taking Charge of Your Digital Identity AARP Nebraska Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.014
Up for Grabs: Taking Charge of Your Digital Identity AARP Nebraska Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.014
Up for Grabs: Taking Charge of Your Digital Identity
 Up for Grabs: Taking Charge of Your Digital Identity AARP Kentucky Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.007
Up for Grabs: Taking Charge of Your Digital Identity AARP Kentucky Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.007
Vanilla Mastercard Terms and Conditions
 Vanilla Mastercard Terms and Conditions The following Agreement governs the Cardholder s use of the Gift Card. Please read this Agreement carefully before you use your Gift Card. A copy of this Agreement
Vanilla Mastercard Terms and Conditions The following Agreement governs the Cardholder s use of the Gift Card. Please read this Agreement carefully before you use your Gift Card. A copy of this Agreement
MEASURING & PRICING THE COST DRIVERS OF A CYBER SECURITY RISK EVENT
 MEASURING & PRICING THE COST DRIVERS OF A CYBER SECURITY RISK EVENT IOWA ACTUARIES CLUB 2/25/16 EDUCATION DAY PRESENTED BY KEITH BURKHARDT, V.P. KRAUS-ANDERSON INSURANCE Overview I. Why are cyber security
MEASURING & PRICING THE COST DRIVERS OF A CYBER SECURITY RISK EVENT IOWA ACTUARIES CLUB 2/25/16 EDUCATION DAY PRESENTED BY KEITH BURKHARDT, V.P. KRAUS-ANDERSON INSURANCE Overview I. Why are cyber security
FACT OR FRICTION INDUSTRY COLLABORATION NOW TACKLING THE NEW #1 PROBLEM: FALSE DECLINES. Joel Siegmund, Manager of Market Development
 FACT OR FRICTION INDUSTRY COLLABORATION NOW TACKLING THE NEW #1 PROBLEM: FALSE DECLINES Joel Siegmund, Manager of Market Development SALES CHARGEBACKS INNOVATION FRAUD SALES CUSTOMER EXPERIENCE ACCEPTANCE
FACT OR FRICTION INDUSTRY COLLABORATION NOW TACKLING THE NEW #1 PROBLEM: FALSE DECLINES Joel Siegmund, Manager of Market Development SALES CHARGEBACKS INNOVATION FRAUD SALES CUSTOMER EXPERIENCE ACCEPTANCE
ADVANTAGES OF A RISK BASED AUTHENTICATION STRATEGY FOR MASTERCARD SECURECODE
 ADVANTAGES OF A RISK BASED AUTHENTICATION STRATEGY FOR MASTERCARD SECURECODE Purpose This document explains the benefits of using Risk Based Authentication (RBA) a dynamic method of cardholder authentication
ADVANTAGES OF A RISK BASED AUTHENTICATION STRATEGY FOR MASTERCARD SECURECODE Purpose This document explains the benefits of using Risk Based Authentication (RBA) a dynamic method of cardholder authentication
PayStand s Guide to Understanding ACH and echeck. How to Receive Direct Bank Payments Online
 PayStand s Guide to Understanding ACH and echeck How to Receive Direct Bank Payments Online Table of Contents Do direct bank payments make sense for your business? What s the difference between ACH and
PayStand s Guide to Understanding ACH and echeck How to Receive Direct Bank Payments Online Table of Contents Do direct bank payments make sense for your business? What s the difference between ACH and
Get the most out of your membership
 PRIVACY & SECURITY Get the most out of your membership W H AT W E V E D O N E TO G E T H E R S O FA R : Opened a new account! Reviewed the fee schedule, including any fees associated with your account
PRIVACY & SECURITY Get the most out of your membership W H AT W E V E D O N E TO G E T H E R S O FA R : Opened a new account! Reviewed the fee schedule, including any fees associated with your account
Chargeback and Dispute Guide. December 2, 2016
 Chargeback and Dispute Guide December 2, 2016 Table of Contents Definitions... 3 Introduction... 4 Responsibilities... 5 GoInterpay Responsibilities... 5 Seller Responsibilities... 5 Fraud-Dispute Procedures...
Chargeback and Dispute Guide December 2, 2016 Table of Contents Definitions... 3 Introduction... 4 Responsibilities... 5 GoInterpay Responsibilities... 5 Seller Responsibilities... 5 Fraud-Dispute Procedures...
Deluxe Provent SM : Protecting against expanded threats. Providing for expanded opportunities.
 Deluxe Provent SM : Protecting against expanded threats. Providing for expanded opportunities. deluxe growth services introduction Identity thieves are extending beyond credit relationships and are more
Deluxe Provent SM : Protecting against expanded threats. Providing for expanded opportunities. deluxe growth services introduction Identity thieves are extending beyond credit relationships and are more
You ve been hacked. Riekie Gordon & Roger Truebody & Alexandra Schudel. Actuarial Society 2017 Convention October 2017
 You ve been hacked Riekie Gordon & Roger Truebody & Alexandra Schudel Why should you care? U$4.6 - U$121 billion - Lloyds U$45 billion not covered 2 The plot thickens 2016 Barkly Survey: It s a business
You ve been hacked Riekie Gordon & Roger Truebody & Alexandra Schudel Why should you care? U$4.6 - U$121 billion - Lloyds U$45 billion not covered 2 The plot thickens 2016 Barkly Survey: It s a business
Money Laundering and Terrorist Financing Risks in the E-Money Sector
 Money Laundering and Terrorist Financing Risks in the E-Money Sector Thematic Review TR18/3 October 2018 TR18/3 Contents 1 Introduction 3 2 Overview 5 3 Findings 7 Annex 1 Glossary 16 How to navigate this
Money Laundering and Terrorist Financing Risks in the E-Money Sector Thematic Review TR18/3 October 2018 TR18/3 Contents 1 Introduction 3 2 Overview 5 3 Findings 7 Annex 1 Glossary 16 How to navigate this
Table 1: Historical Summary of Revenue Lost to Fraud. Estimate of Revenue Lost to Fraud
 Anchin Alert: ACFE Report to the Nations 2018 The Association of Certified Fraud Examiners ( ACFE ) recently published the Report to the Nations 2018 Global Study on Occupational Fraud and Abuse (the 2018
Anchin Alert: ACFE Report to the Nations 2018 The Association of Certified Fraud Examiners ( ACFE ) recently published the Report to the Nations 2018 Global Study on Occupational Fraud and Abuse (the 2018
card fraud business Helpful information for Merchants Avoiding card fraud
 card fraud business Helpful information for Merchants Avoiding card fraud How to stop card fraud before it happens. It is an unfortunate fact that not everyone with a card, or card number, is the card
card fraud business Helpful information for Merchants Avoiding card fraud How to stop card fraud before it happens. It is an unfortunate fact that not everyone with a card, or card number, is the card
O P C S. OPCS Overview 9/28/2017 (OPCS) The implementation of the Ohio Pooled Collateral System creates a unique partnership between:
 O P C S (OPCS) opcs.ohio.gov 1 OPCS Overview The implementation of the Ohio Pooled Collateral System creates a unique partnership between: Treasurer s Office Financial Institutions Local Governments opcs.ohio.gov
O P C S (OPCS) opcs.ohio.gov 1 OPCS Overview The implementation of the Ohio Pooled Collateral System creates a unique partnership between: Treasurer s Office Financial Institutions Local Governments opcs.ohio.gov
THE NEW WAY TO CARRY CURRENCY USER GUIDE
 THE NEW WAY TO CARRY CURRENCY USER GUIDE Find out how to; USE YOUR CARD OVERSEAS MANAGE YOUR BUDGET RELOAD YOUR CARD AND MUCH MORE... Welcome to your new The Cash Passport is a traveller s card, issued
THE NEW WAY TO CARRY CURRENCY USER GUIDE Find out how to; USE YOUR CARD OVERSEAS MANAGE YOUR BUDGET RELOAD YOUR CARD AND MUCH MORE... Welcome to your new The Cash Passport is a traveller s card, issued
APPLE BLOCKCHAIN COIN
 APPLE COIN www.apcoin.co APPLE BLOCKCHAIN COIN The world s advanced blockchain based platform with Secure, Fast and Infinite Opportunities. WHITEPAPER THE NEXT GLOBAL PAYING WHITEPAPER Introduction APPLE
APPLE COIN www.apcoin.co APPLE BLOCKCHAIN COIN The world s advanced blockchain based platform with Secure, Fast and Infinite Opportunities. WHITEPAPER THE NEXT GLOBAL PAYING WHITEPAPER Introduction APPLE
gamevy Anti- Money Laundering Detecting and Preventing Financial Crime Training for Gamevy
 gamevy Anti- Money Laundering Detecting and Preventing Financial Crime Training for Gamevy Introduction This document is Gamevy s training on anti- money laundering regulations within the context of our
gamevy Anti- Money Laundering Detecting and Preventing Financial Crime Training for Gamevy Introduction This document is Gamevy s training on anti- money laundering regulations within the context of our
Card fraud costs to banks increase to $40bn
 Card fraud costs to banks increase to $40bn Revisiting the benefits of advanced fraud risk management systems January 2017 source: Featurespace Advanced fraud management systems offer $15.8bn of savings
Card fraud costs to banks increase to $40bn Revisiting the benefits of advanced fraud risk management systems January 2017 source: Featurespace Advanced fraud management systems offer $15.8bn of savings
Bank Secrecy Act OFAC FinCEN
 Bank Secrecy Act OFAC FinCEN 2017 CREDIT UNION EMPLOYEE TRAINING Financial Crimes Identify Track Report Common BSA Acronyms CIP CDD CTR SAR FinCEN OFAC Customer Identification Program Customer Due Diligence
Bank Secrecy Act OFAC FinCEN 2017 CREDIT UNION EMPLOYEE TRAINING Financial Crimes Identify Track Report Common BSA Acronyms CIP CDD CTR SAR FinCEN OFAC Customer Identification Program Customer Due Diligence
EQUIFAX AFTERMATH ONE YEAR LATER. id theftcente r.o r g
 EQUIFAX ONE YEAR LATER AFTERMATH R E P O RT Ξ 2018 id theftcente r.o r g 1-8 8 8-40 0-5 5 3 0 A little over one year ago, Equifax announced one of the largest data breaches in history in which approximately
EQUIFAX ONE YEAR LATER AFTERMATH R E P O RT Ξ 2018 id theftcente r.o r g 1-8 8 8-40 0-5 5 3 0 A little over one year ago, Equifax announced one of the largest data breaches in history in which approximately
A report showing the merchant s settlement. The acquirer settlement report is generated by the acquiring bank at the end of every billing cycle.
 A Acquirer (acquiring bank) An acquirer is an organisation that is licensed as a member of Visa/MasterCard as an affiliated bank and processes credit card transactions for (online) businesses. Acquirers
A Acquirer (acquiring bank) An acquirer is an organisation that is licensed as a member of Visa/MasterCard as an affiliated bank and processes credit card transactions for (online) businesses. Acquirers
Money. 1 Numeracy and mathematics glossary. Terms Illustrations Definitions. Affordability
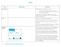 Terms Illustrations Definitions Affordability ATM Available balance Discussing if you can afford an item e.g. You have 5p, the apple is 8p, can you buy it? The toy is 2.50 and the tshirt is 4.30. You have
Terms Illustrations Definitions Affordability ATM Available balance Discussing if you can afford an item e.g. You have 5p, the apple is 8p, can you buy it? The toy is 2.50 and the tshirt is 4.30. You have
ARC s Guide to Travel Agency Payment Card Acceptance, Risk Mitigation and Chargeback Management
 ARC s Guide to Travel Agency Payment Card Acceptance, Risk Mitigation and Chargeback Management A concise guide with useful advice, best practices and practical examples for travel payment professionals
ARC s Guide to Travel Agency Payment Card Acceptance, Risk Mitigation and Chargeback Management A concise guide with useful advice, best practices and practical examples for travel payment professionals
Ball State University
 PCI Data Security Awareness Training Agenda What is PCI-DSS PCI-DDS Standards Training Definitions Compliance 6 Goals 12 Security Requirements Card Identification Basic Rules to Follow Myths 1 What is
PCI Data Security Awareness Training Agenda What is PCI-DSS PCI-DDS Standards Training Definitions Compliance 6 Goals 12 Security Requirements Card Identification Basic Rules to Follow Myths 1 What is
Up for Grabs: Taking Charge of Your Digital Identity
 Up for Grabs: Taking Charge of Your Digital Identity AARP Louisiana Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.008
Up for Grabs: Taking Charge of Your Digital Identity AARP Louisiana Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.008
Managing Chargebacks. April 2016
 Managing Chargebacks April 2016 Contents Introduction... 3 What is a Chargeback?... 3 Chargeback Process Overview... 3 Chargebacks Common Misunderstandings... 4 What is a Retrieval Request?... 4 Can all
Managing Chargebacks April 2016 Contents Introduction... 3 What is a Chargeback?... 3 Chargeback Process Overview... 3 Chargebacks Common Misunderstandings... 4 What is a Retrieval Request?... 4 Can all
Check conversion is the process of converting a consumer check payment into an electronic payment.
 J&B SOFTWARE ARC - FAQ ARC Frequently Asked Questions & Answers Q: What is check conversion and how does it work? Check conversion is the process of converting a consumer check payment into an electronic
J&B SOFTWARE ARC - FAQ ARC Frequently Asked Questions & Answers Q: What is check conversion and how does it work? Check conversion is the process of converting a consumer check payment into an electronic
Thomas Cook One Currency Prepaid Card Terms and Conditions
 Thomas Cook One Currency Prepaid Card Terms and Conditions 1 Thomas Cook One Currency Prepaid Card Terms and Conditions By purchasing the Thomas Cook One Currency Prepaid Card, you confirm that you are
Thomas Cook One Currency Prepaid Card Terms and Conditions 1 Thomas Cook One Currency Prepaid Card Terms and Conditions By purchasing the Thomas Cook One Currency Prepaid Card, you confirm that you are
Thomas Cook Borderless Prepaid Card Terms and Conditions
 Thomas Cook Borderless Prepaid Card Terms and Conditions Multicurrency MasterCard Thomas Cook Borderless Prepaid Card Terms and Conditions By purchasing the Thomas Cook Borderless Prepaid Card, you confirm
Thomas Cook Borderless Prepaid Card Terms and Conditions Multicurrency MasterCard Thomas Cook Borderless Prepaid Card Terms and Conditions By purchasing the Thomas Cook Borderless Prepaid Card, you confirm
How to combat card fraud. A guide to detecting and preventing card fraud
 How to combat card fraud A guide to detecting and preventing card fraud Contents Introduction 3 Card Present fraud 4 Card Not Present fraud 6 Payment card industry data security standards Your guide to
How to combat card fraud A guide to detecting and preventing card fraud Contents Introduction 3 Card Present fraud 4 Card Not Present fraud 6 Payment card industry data security standards Your guide to
Focused on card fraud prevention
 Focused on card fraud prevention The evolution of credit card fraud As EMV adoption increases, counterfeit cards are harder to create and use 76% decrease in counterfeit fraud at U.S. chip-enabled merchants*
Focused on card fraud prevention The evolution of credit card fraud As EMV adoption increases, counterfeit cards are harder to create and use 76% decrease in counterfeit fraud at U.S. chip-enabled merchants*
Debit Card Account Conditions of Use
 Debit Card Account Conditions of Use Contents SUMMARY OF IMPORTANT INFORMATION 4 SUMMARY OF ACCOUNT AND VISA CARD FEATURES AND RESTRICTIONS 8 PART A INTRODUCTION 12 1 About these Conditions of Use 12
Debit Card Account Conditions of Use Contents SUMMARY OF IMPORTANT INFORMATION 4 SUMMARY OF ACCOUNT AND VISA CARD FEATURES AND RESTRICTIONS 8 PART A INTRODUCTION 12 1 About these Conditions of Use 12
Credit Card Agreement regulated by the Consumer Credit Act 1974
 Credit Card Agreement regulated by the Consumer Credit Act 1974 This Agreement is between us, NewDay Ltd, 7 Handyside Street, London, N1C 4DA, and you, Your credit intermediary Laura Ashley Limited of
Credit Card Agreement regulated by the Consumer Credit Act 1974 This Agreement is between us, NewDay Ltd, 7 Handyside Street, London, N1C 4DA, and you, Your credit intermediary Laura Ashley Limited of
Selected Terms & Conditions for Wells Fargo Consumer Debit and ATM Cards
 Selected Terms & Conditions for Wells Fargo Consumer Debit and ATM s Terms and Conditions effective 04/24/2017. Introduction page 1 Using Your page 2 Using Your Through a Mobile Device page 4 One-Time
Selected Terms & Conditions for Wells Fargo Consumer Debit and ATM s Terms and Conditions effective 04/24/2017. Introduction page 1 Using Your page 2 Using Your Through a Mobile Device page 4 One-Time
At the Heart of Cyber Risk Mitigation
 At the Heart of Cyber Risk Mitigation De-risking Cyber Threats with Insurance Vikram Singh Abstract Management of risks is an integral part of the insurance industry. Companies have succeeded in identifying
At the Heart of Cyber Risk Mitigation De-risking Cyber Threats with Insurance Vikram Singh Abstract Management of risks is an integral part of the insurance industry. Companies have succeeded in identifying
The Risk of Economic Crime
 The Risk of Economic Crime 0 ACFE European Fraud Conference London, March 7, 0 GROUP SECURITY HERE TO PROTECT OUR WORLD Torsten Wolf Group Head of Crime and Fraud Prevention Agenda Introduction Economic
The Risk of Economic Crime 0 ACFE European Fraud Conference London, March 7, 0 GROUP SECURITY HERE TO PROTECT OUR WORLD Torsten Wolf Group Head of Crime and Fraud Prevention Agenda Introduction Economic
CUA Credit Cards. Conditions of Use and Credit Guide
 CUA Credit Cards Conditions of Use and Credit Guide Effective 8 August 2016 Note: This document does not contain all of the required precontractual information for your Agreement. You should also refer
CUA Credit Cards Conditions of Use and Credit Guide Effective 8 August 2016 Note: This document does not contain all of the required precontractual information for your Agreement. You should also refer
LENDING SHORT TERM AND INSTALMENT LENDING. 10 Reasons why Callcredit will help you make smarter decisions
 SHORT TERM AND INSTALMENT LENDING 10 Reasons why Callcredit will help you make smarter decisions CONTENTS WE HELP DELIVER FAST, ACCURATE AND RESPONSIBLE LENDING DECISIONS 2 1. Unrivalled Data Coverage
SHORT TERM AND INSTALMENT LENDING 10 Reasons why Callcredit will help you make smarter decisions CONTENTS WE HELP DELIVER FAST, ACCURATE AND RESPONSIBLE LENDING DECISIONS 2 1. Unrivalled Data Coverage
PRIVACY AND CYBER SECURITY
 PRIVACY AND CYBER SECURITY Presented by: Joe Marra, Senior Account Executive/Producer Stoya Corcoran, Assistant Vice President Presented to: CIFFA Members September 20, 2017 1 Disclaimer The information
PRIVACY AND CYBER SECURITY Presented by: Joe Marra, Senior Account Executive/Producer Stoya Corcoran, Assistant Vice President Presented to: CIFFA Members September 20, 2017 1 Disclaimer The information
WHITE PAPER. The Evolution of Fraud in the Insurance Industry
 WHITE PAPER The Evolution of Fraud in the Insurance Industry Introduction The insurance industry is certainly no stranger to online fraud, whether it s being directed at insurers or the consumers they
WHITE PAPER The Evolution of Fraud in the Insurance Industry Introduction The insurance industry is certainly no stranger to online fraud, whether it s being directed at insurers or the consumers they
Busting Fraud Rings with. Social Link Analysis
 Busting Fraud Rings with Social Link Analysis Table of Contents INTRODUCTION... 1 WHAT IS BUST-OUT FRAUD AND WHY IS IT SO HARD TO DETECT?... 2 SOCIAL LINK ANALYSIS (SLA): A POWERFUL NEW WEAPON... 3 HOW
Busting Fraud Rings with Social Link Analysis Table of Contents INTRODUCTION... 1 WHAT IS BUST-OUT FRAUD AND WHY IS IT SO HARD TO DETECT?... 2 SOCIAL LINK ANALYSIS (SLA): A POWERFUL NEW WEAPON... 3 HOW
EASY TRAVEL PAYOUTS FOR EMERGING MARKETS EXPANSION
 WHITE PAPER EASY TRAVEL PAYOUTS FOR EMERGING MARKETS EXPANSION www.transpay.com EMERGING MARKETS POISED FOR TOURISM GROWTH The global tourism industry is one of the most lucrative in the world contributing
WHITE PAPER EASY TRAVEL PAYOUTS FOR EMERGING MARKETS EXPANSION www.transpay.com EMERGING MARKETS POISED FOR TOURISM GROWTH The global tourism industry is one of the most lucrative in the world contributing
CUA Credit Cards Conditions of Use and Credit Guide
 CUA Credit Cards Conditions of Use and Credit Guide Effective 1 January 2019 Note: This document does not contain all of the required precontractual information for your Agreement. You should also refer
CUA Credit Cards Conditions of Use and Credit Guide Effective 1 January 2019 Note: This document does not contain all of the required precontractual information for your Agreement. You should also refer
Up for Grabs: Taking Charge of Your Digital Identity
 Up for Grabs: Taking Charge of Your Digital Identity AARP Massachusetts Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.009
Up for Grabs: Taking Charge of Your Digital Identity AARP Massachusetts Survey of Internet Users Age 18+ Report prepared by Karla Pak, Doug Shadel, and Alicia Williams August 2018 https://doi.org/10.26419/res.00228.009
Dig Deep into the Root Causes of Fraud to Prevent Future Attacks
 Dig Deep into the Root Causes of Fraud to Prevent Future Attacks Presented by: Ann Davidson, VP of Risk Consulting at Allied Solutions & Tammy Behnke, Credit Union Program Director at ProSight Specialty
Dig Deep into the Root Causes of Fraud to Prevent Future Attacks Presented by: Ann Davidson, VP of Risk Consulting at Allied Solutions & Tammy Behnke, Credit Union Program Director at ProSight Specialty
emoneysafe debit Mastercard Terms and Conditions of Use
 debit Mastercard Terms and Conditions of Use 1. The card 1.1 These terms and conditions apply to any holder of this card ( the card ). By using your card, you are demonstrating your agreement to these
debit Mastercard Terms and Conditions of Use 1. The card 1.1 These terms and conditions apply to any holder of this card ( the card ). By using your card, you are demonstrating your agreement to these
Stripe Snapshot. Online Fraud Trends and Behavior. December Stripe Snapshot: Online Fraud Trends and Behavior. December 2017
 Stripe Snapshot Online Fraud Trends and Behavior 1 Introduction In 2016, an estimated 1.61 billion people worldwide purchased goods online, and global e-retail sales amounted to $1.9 trillion. And recent
Stripe Snapshot Online Fraud Trends and Behavior 1 Introduction In 2016, an estimated 1.61 billion people worldwide purchased goods online, and global e-retail sales amounted to $1.9 trillion. And recent
CREDIT CARDS CONDITIONS OF USE
 CREDIT CARDS CONDITIONS OF USE EFFECTIVE 18 SEPTEMBER 2017 Important note This booklet does not contain all the pre-contractual information we are required by law to give you before the agreement is made.
CREDIT CARDS CONDITIONS OF USE EFFECTIVE 18 SEPTEMBER 2017 Important note This booklet does not contain all the pre-contractual information we are required by law to give you before the agreement is made.
Visa Debit Conditions of Use
 Visa Debit Conditions of Use BEFORE YOU USE YOUR VISA CARD Please read these Conditions of Use. They apply to: all transactions initiated by you through an Electronic Banking Terminal (which in these Conditions
Visa Debit Conditions of Use BEFORE YOU USE YOUR VISA CARD Please read these Conditions of Use. They apply to: all transactions initiated by you through an Electronic Banking Terminal (which in these Conditions
Revenue Scotland Counter-Fraud Policy
 Revenue Scotland Counter-Fraud Policy 0 Table of Contents Contents 1. Introduction and Scope... 2 2. Related Policies and Procedures... 2 3. Overview of Policy... 3 4. Responsibilities... 3 5. Exceptions...
Revenue Scotland Counter-Fraud Policy 0 Table of Contents Contents 1. Introduction and Scope... 2 2. Related Policies and Procedures... 2 3. Overview of Policy... 3 4. Responsibilities... 3 5. Exceptions...
BUILDING RELATIONSHIPS, ONE PAYOUT AT A TIME
 WHITE PAPER BUILDING RELATIONSHIPS, ONE PAYOUT AT A TIME www.transpay.com YOUR BUSINESS REST API WEB PORTAL TRANSPAY BUILDING RELATIONSHIPS, ONE PAYOUT AT A TIME Introduction TRANSPAY On the surface, sending
WHITE PAPER BUILDING RELATIONSHIPS, ONE PAYOUT AT A TIME www.transpay.com YOUR BUSINESS REST API WEB PORTAL TRANSPAY BUILDING RELATIONSHIPS, ONE PAYOUT AT A TIME Introduction TRANSPAY On the surface, sending
Visa Merchant Best Practice Guide for Cardholder Not Present Transactions
 Visa Merchant Best Practice Guide for Cardholder Not Present Transactions Table of Contents Section 1 About This Guide 03 Section 2 Merchant Procedures 05 Section 3 Authorisation 07 Authorisation Procedures
Visa Merchant Best Practice Guide for Cardholder Not Present Transactions Table of Contents Section 1 About This Guide 03 Section 2 Merchant Procedures 05 Section 3 Authorisation 07 Authorisation Procedures
VANIG BUSINESS ANALYSIS
 VANIG BUSINESS ANALYSIS About US Market Analysis Contents ASEAN Competitor Analysis Risk Analysis Financial Analysis ABOUT US What is Vanig Vanig is an integrated e-commerce and supply chain solution powered
VANIG BUSINESS ANALYSIS About US Market Analysis Contents ASEAN Competitor Analysis Risk Analysis Financial Analysis ABOUT US What is Vanig Vanig is an integrated e-commerce and supply chain solution powered
Fraud Control Framework
 London Pension Fund Authority Fraud Control Framework Dec 2017 Page 1 of 14 Introduction: From April 2016 the LPFA partnered with Lancashire County Pension Fund (LCPF) in order to establish Local Pensions
London Pension Fund Authority Fraud Control Framework Dec 2017 Page 1 of 14 Introduction: From April 2016 the LPFA partnered with Lancashire County Pension Fund (LCPF) in order to establish Local Pensions
CARD FRAUD BOOKLET Protect your card and information at all times PAGE: 1 // 42
 PAGE: 1 // 42 www.sabric.co.za CARD FRAUD BOOKLET Protect your card and information at all times Table of Contents Executive Summary 05 21 Card Fraud in the UK Qualification of Information Payments Association
PAGE: 1 // 42 www.sabric.co.za CARD FRAUD BOOKLET Protect your card and information at all times Table of Contents Executive Summary 05 21 Card Fraud in the UK Qualification of Information Payments Association
11/9/15. Fraud in Non-profit Organizations: What You Need to Know NOW!
 Fraud in Non-profit Organizations: What You Need to Know NOW! The CFE Credential The Certified Fraud Examiner (CFE) credential denotes proven expertise in fraud prevention, detection and deterrence. CFEs
Fraud in Non-profit Organizations: What You Need to Know NOW! The CFE Credential The Certified Fraud Examiner (CFE) credential denotes proven expertise in fraud prevention, detection and deterrence. CFEs
2014 AFP Payments Fraud and Control Survey
 lllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllll 2014 AFP Payments Fraud and Control Survey Report of Survey Results Underwritten by 2014 AFP
lllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllll 2014 AFP Payments Fraud and Control Survey Report of Survey Results Underwritten by 2014 AFP
A GUIDE TO CYBER RISKS COVER
 A GUIDE TO CYBER RISKS COVER Cyber risk the daily business threat to SMEs Cyber risks and data security breaches are a daily threat to everyday business. Less than 10% of UK companies have cyber insurance
A GUIDE TO CYBER RISKS COVER Cyber risk the daily business threat to SMEs Cyber risks and data security breaches are a daily threat to everyday business. Less than 10% of UK companies have cyber insurance
Honest and ethical behaviour policy
 Policy Take Ownership Honest and ethical behaviour policy Issue Date 27 June 2018 Policy Number 004 This version dated 27 June 2018 supersedes all earlier dated documents. Table of contents Section A Introduction
Policy Take Ownership Honest and ethical behaviour policy Issue Date 27 June 2018 Policy Number 004 This version dated 27 June 2018 supersedes all earlier dated documents. Table of contents Section A Introduction
How Credit Card Chargebacks Really Impact your Bottom Line
 How Credit Card Chargebacks Really Impact your Bottom Line Reducing Fraud, Chargebacks, and Lost Profits for Recurring Merchants There are many considerations to take into account when attempting to prevent,
How Credit Card Chargebacks Really Impact your Bottom Line Reducing Fraud, Chargebacks, and Lost Profits for Recurring Merchants There are many considerations to take into account when attempting to prevent,
Palomar Community College District Procedure AP 5900 PREVENTION OF IDENTITY THEFT IN STUDENT FINANCIAL TRANSACTIONS
 1 STUDENT SERVICES 2 3 AP 5900 PREVENTION OF IDENTITY THEFT IN STUDENT FINANCIAL TRANSACTIONS 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 References: Fair
1 STUDENT SERVICES 2 3 AP 5900 PREVENTION OF IDENTITY THEFT IN STUDENT FINANCIAL TRANSACTIONS 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 References: Fair
Chubb Cyber Enterprise Risk Management
 Chubb Cyber Enterprise Risk Management Fact Sheet Financial Lines Chubb Cyber Enterprise Risk Management When it comes to a data security breach or privacy loss, it isn t a matter of if it will happen
Chubb Cyber Enterprise Risk Management Fact Sheet Financial Lines Chubb Cyber Enterprise Risk Management When it comes to a data security breach or privacy loss, it isn t a matter of if it will happen
