Partial Redundancy in HPC Systems with Non-Uniform Node Reliabilities
|
|
|
- Delphia Price
- 5 years ago
- Views:
Transcription
1 Partial Redundancy in HPC Systems with Non-Uniform Node Reliabilities Zaeem Hussain Department of Computer Science University of Pittsburgh Taieb Znati Department of Computer Science University of Pittsburgh Rami Melhem Department of Computer Science University of Pittsburgh Abstract We study the usefulness of partial redundancy in HPC message passing systems where individual node failure distributions are not identical. Prior research works on fault tolerance have generally assumed identical failure distributions for the nodes of the system. In such settings, partial replication has never been shown to outperform the two extremes(full and no-replication) for any significant range of node counts. In this work, we argue that partial redundancy may provide the best performance under the more realistic assumption of non-identical node failure distributions. We provide theoretical results on arranging nodes with different reliability values among replicas such that system reliability is maximized. Moreover, using system reliability to compute MTTI (mean-time-to-interrupt) and expected completion time of a partially replicated system, we numerically determine the optimal partial replication degree. Our results indicate that partial replication can be a more efficient alternative to full replication at system scales where Checkpoint/Restart alone is not sufficient. Keywords HPC, fault tolerance, resilience, replication, checkpoint. I. INTRODUCTION With the increasing scale of modern day high performance computing systems, faults are becoming a growing concern. This is simply a consequence of the increasing number of resources being used in HPC platforms. Even though, on average, individual components fail after several years, the sheer number of these components inside the system means that the entire system experiences failures at a much higher rate, usually on the order of days[1]. One of the most common techniques to deal with faults is Checkpointing and Rollback recovery. However, as system scale increases, the overall failure rate is also expected to increase, which means more checkpoints need to be taken. This causes a lot of system time to be spent writing checkpoints and recovering from failures, rather than doing useful work. As an alternative to checkpointing, [2] proposed replication to improve the system reliability at large scales. In pure replication with dual redundancy, all work is duplicated on separate hardware resources. This allows the application to continue execution even in the presence of failures as long as both processes (or nodes) that are replicas of each other have not failed. This significantly improves the mean time to interrupt (MTTI) of the system[2][3], requiring fewer checkpoints compared to the case without replication. However, it comes at the cost of system efficiency, which is capped at 5%. Hence, the argument for pure replication as a fault tolerance mechanism holds weight only at system scales at which the efficiency of checkpointing alone drops below 5%. To break the 5% efficiency barrier of pure replication, [4] studied partial replication where only a subset of application visible nodes are replicated. However, neither [4] nor any other works since then have established any range of node counts for which it makes sense to only partially replicate an execution. The above mentioned fault tolerance techniques have traditionally been studied in the HPC community with the assumption that all of the individual nodes in a system have independent and identical (iid) failure distributions. While this does simplify the theoretical analysis, there is no experimental evidence to suggest that this assumption holds true in reality. In fact, several studies[5][6][7][8] on failures experienced by supercomputing systems have concluded that failures are spatially non-uniform. One natural approach to model such systems is to assume that individual node failure distributions are still independent, but not identical. In this work, we study the usefulness of partial redundancy for such systems. It should be noted that changing the iid failure assumption does not simply mean redoing the theoretical and numerical analysis, but rather brings up other questions as well. One such question, for example, that we answer in this paper, is: which nodes in the system should be replicated and which nodes should they be replicated with? We answer this and other questions exploring the optimal replication factor (ratio of total nodes used to the number of application visible nodes) of such systems through a combination of theoretical and numerical analyses. To the best of our knowledge, this is the first work that assumes a non-uniform failure distribution of individual nodes and provides theoretical insights into how such a system should be partially replicated. Specifically, we make the following contributions: 1) We theoretically determine, given the total number of nodes in a system with non-identical node failure distributions and the fraction of nodes to be replicated, the selection of nodes into replicated and nonreplicated sets and the pairing of replicas such that system reliability is maximized. 2) Using the system reliability to compute the MTTI and average completion time of an execution, we numerically determine the optimal partial replication factor and demonstrate that optimal performance can often be achieved through partial redundancy. 3) We investigate in detail a hypothetical system involving two kinds of nodes: Good, that are less likely to SC18, November 11-16, 218, Dallas, Texas, USA /18/$31. c 218 IEEE
2 Fig. 1. Selection and pairing of replicas to maximize reliability. fail, and Bad, that are more likely to fail. We show how different parameters affect the optimal partial replication factor. Our work provides a framework which can be used by system administrators and job schedulers to decide which nodes to replicate in systems where individual nodes mean-time-betweenfailures (MTBFs), while not necessarily accurately modeled, are known to take either a high or a low value to a first order approximation. Even at node counts where the performance of simple checkpoint/restart drops drastically, pure replication still seems like an overkill. Our work attempts to demonstrate that, instead of blindly replicating every node, a smarter choice can be made by understanding the failure characteristics of the underlying system and replicating accordingly. The remainder of this paper is organized as follows: section II provides results on the system configuration that maximizes reliability, section III presents the mathematical details of the model and the optimization problem, sections IV, V and VI present the results of the optimization for different types of systems, section VII surveys some of the related work and section VIII concludes. II. MAXIMIZING RELIABILITY We start with the question of how, knowing the number of nodes to replicate, should the replicated nodes be selected and paired. Consider a system with N nodes with individual node failure density functions given by h i (t), 1 i N, where t > is the time. These functions are typically taken to be exponential or Weibull, and characterized by failure rate λ i, where λ i is the inverse of node i s MTBF. Individual node MTBFs can be assigned by observing their failure history. For example, works such as [5], [6] and [7] explore the spatial distribution of failures by analyzing the number of failures over time at the cabinet, cage, blade and node granularities for multiple HPC systems at the Oak Ridge National Laboratory (ORNL) and Los Alamos National Laboratory (LANL) over several years. Such analyses can be used to estimate MTBF down to the level of individual nodes or group of nodes. A more sophisticated approach to compute the reliability of individual nodes is presented in [9]. We assume without loss of generality that the nodes are ordered by their failure rates, such that λ i (t) λ i+1 (t) for all 1 i N 1. Note that the iid failure distribution assumption is a special case of this in which all λ i s have the same value. In order to answer the question of optimal selection and pairing of replicas, it is simpler to work with the nodes probability of survival until time t (or reliability) given by g i (t) = 1 t h i(x)dx, 1 i N. With the nodes sorted by increasing failure rates, we see that g i (t) g i+1 (t) for all 1 i N 1. Assume, for now, that a particular job requires n nodes to execute in parallel, where n N. Moreover, assume that the remaining N n nodes are to be used as replicas of some of the n nodes, in order to provide better protection from failures. We will relax these assumptions in subsequent sections to make n variable in order to explore if partial replication is beneficial at all. For now, however, we try to answer the first question: Which of the n nodes should have replicas, and how should they be paired with the other N n nodes to form node-replica pairs? We restrict ourselves to maximum dual node replication only, so N/2 n N. In such a configuration, let a = n (N n) = 2n N be the number of non replicated nodes, and b = n a = N n be the number of node replica pairs, such that a + 2b = N and a + b = n. The partial replication factor, r, will thus be given by r = (a + 2b)/(a + b), and 1 r 2. Our original question can thus be reformulated as: Given values of a and b and reliability g i (t), 1 i N, which 2b out of the N nodes should be replicated and how should the replicated nodes be paired so that overall system reliability is maximized? The answer is to pick the least reliable 2b nodes for replication. Among those 2b nodes, the least reliable node should be paired with the most reliable node, and so on. This is shown in Fig 1, and formally stated in the following theorem: Theorem. Given a, b and an N node system (a + 2b = N) with node reliability given by g i (t) and g i (t) g i+1 (t) for 1 i N 1, let A {1, 2,..., N}, A = a, be the set of non-replicated nodes and B = {(j, k) j, k {1, 2,... N} A and j k}, B = b, be the set of nodereplica pairs. Maximum overall system reliability is achieved when A = {1, 2,..., a} and B = {(j, 2(a + b) + 1 j) j {a + 1, a + 2,... a + b}}. To determine the overall reliability for a given partial replication configuration, we observe that, for a node-replica pair (j, k), application failure occurs when both nodes in the pair fail. Hence, the reliability of pair (j, k) is given by 1 (1 g j (t))(1 g k (t)). For sets A and B as defined above, the overall system reliability R(t) can thus be written as R(t) = g i (t) (1 (1 g j (t))(1 g k (t))) (1) i A (j,k) B For simplicity, we remove variable t and obtain R = g i (1 (1 g j )(1 g k )) (2) i A (j,k) B We prove the above theorem in two lemmas. First we prove that maximum reliability is achieved when the set of nonreplicated nodes consists of the most reliable nodes. Lemma 1. R is maximized when A = {1, 2,..., a}. Proof: Assume by contradiction that we have a configuration in which A {1, 2,..., a}. This means there is a node with higher reliability in the replicated set and a node with lower reliability that is not replicated. In other words, g i where i A and i > a and a pair (j, k) B such that
3 at least one of j or k is in {1, 2,..., a}. Assume without loss of generality that j {1, 2,..., a}. This means that j < i, and we know, from the ordering of node reliability, that g j g i. The contribution of nodes i, j, k in this configuration to system reliability, R, is given by g i (1 (1 g j )(1 g k )) = g i (g j + g k g j g k ). We have g i (g j + g k g j g k ) = g i g j + g i g k g i g j g k g i g j + g j g k g i g j g k (since g i g j ) = g j (1 (1 g i )(1 g k )) (3) Since g i (1 (1 g j )(1 g k )) g j (1 (1 g i )(1 g k )) with equality iff g j = g i, we observe that if we exchange nodes i and j between sets A and B, while keeping everything else the same, we obtain a system with reliability R such that R R. We can keep performing these exchanges as long as A {1, 2,..., a}. Each exchange step will either improve the system reliability, R, or keep it the same. Hence, R will be maximized when A = {1, 2,..., a}. We now move to the second part of the theorem regarding the pairing of replicas. Rewriting R = R A R B where R A = i A g i and R B = (j,k) B (1 (1 g j)(1 g k )), we focus solely on R B since R A is determined from lemma 1. Our job, then, is to show that, given 2b numbers g 1 g 2 g 2b, R B is maximized when B = {(j, 2b+1 j) j {1, 2,... b}}. To simplify the expressions, we will rewrite R B in terms of the node failure probabilities, p i = 1 g i, 1 i 2b as R B = (j,k) B (1 p jp k ). The ordering of the failure probabilities then becomes p 1 p 2 p 2b. Lemma 2. R B is maximum when B = {(j, 2b + 1 j) j {1, 2,..., b}}. Proof: We prove this through induction on b. When b = 1, there are only 2 nodes, and only one possible pairing, so B = {(1, 2)} trivially. For the inductive hypothesis, assume that the lemma is true for b = k. For b = k + 1, we first prove that, for R B to be maximum, (1, 2k + 2) B. Assume by contradiction that (1, 2k + 2) B. This means that (1, i), (j, 2k + 2) B where i, j {2,..., 2b 1 = 2k + 1}. Similar to lemma 1, we will show that swapping the nodes in the two pairs to get B, where (1, 2k + 2), (i, j) B, will improve system reliability. The contribution of pairs (1, i), (j, 2k + 2) to R B is given by (1 p 1 p i )(1 p j p 2k+2 ). We have (1 p 1 p i )(1 p j p 2k+2 ) = 1 p 1 p i p j p 2k+2 + p 1 p i p j p 2k+2 1 p 1 p 2k+2 p i p j + p 1 p i p j p 2k+2 = (1 p 1 p 2k+2 )(1 p i p j ) (4) The inequality on the second line is obtained by noting that p 1 p j and p i p 2k+2. By rearrangement inequality[1], we know that p 1 p i + p j p 2b p 1 p 2k+2 + p i p j which leads to the inequality obtained above. This means that for any B such that (1, i), (j, 2k + 2) B, we can get R B R B where B = (B {(1, i), (j, 2k + 2)}) {(1, 2b), (i, j)}. Using the same argument as in lemma 1, we conclude that R B is maximum when (1, 2k + 2) B. We can thus write the maximum R B as R B = (1 p 1 p 2k+2 )R B where R B is the combined reliability of all node-replica pairs other than (1, 2k + 2). R B can also be considered as the reliability of 2k nodes making k pairs which, according to the inductive assumption, is maximum when the 2k nodes are paired as stated in the lemma. The overall reliability, R B, is therefore maximized when B = {(j, 2(k + 1) + 1 j) j {1, 2,... k + 1}} which concludes the proof. Lemma 1 and lemma 2 combined complete the proof of the theorem. At this point, one may also wonder if a similar result can be obtained for replication degrees greater than 2, for example if triple replication is also allowed. In that case, the only result we can obtain is the following Lemma 3. If B contains replica groups with degrees 2, i.e. x B x 2, R is still maximized when A = {1, 2,..., a}. Proof: The proof proceeds by contradiction in the same way as lemma 1 by taking a tuple in B which has an element i where i a, and similarly a j A where j > a. It can then be shown that swapping i and j between the two sets causes R to increase. We omit the detailed steps since they are identical to that of lemma 1. The same result, however, does not extend to the case of deciding, for example, which nodes should be doubly replicated and which should be triply replicated. In this paper, we restrict our focus to partially redundant systems where nodes are at most doubly replicated. It should be noted that, although the proof in this section is formulated in terms of node reliabilities, the result holds for any time interval in which the relative ordering of the individual nodes likelihoods of failure is known. This means that if, at different time intervals, the ordering of nodes based on their likelihoods of failure changes, the optimal configuration, while still determined based on the result in this section, will be different during different time intervals. Handling such configuration changes in practical settings may be possible through an adaptive method to switch replicas on the fly, as in [11]. A theoretical analysis to determine when to change the configuration, taking into consideration the cost of reconfiguring the system during execution, is beyond the scope of the current work and is left for future work. In this paper, we will only consider cases where the nodes failure densities are exponential, or Weibull with the same shape parameter. In both of these cases, the relative ordering of node reliabilities remains the same throughout the lifetime and is determined from the individual node MTBFs. III. EXPECTED COMPLETION TIME In the previous section, we looked at how the nodes should be grouped into replicas when the number of nodes to be replicated is fixed. In other words, the number of application visible nodes n was already decided, a and b were then determined from the equations a+2b = N and a+b = n, and the goal was to intelligently pick nodes to be placed in sets A and B based on their individual reliability g 1 (t) g 2 (t) g N (t). In that case, it made sense to look at system reliability alone, because the number of nodes to use and the partial replication factor was fixed. In the rest of this paper, however, we attempt
4 to answer the more general question: Given an N node system with node reliability g 1 (t) g 2 (t) g N (t), how many of the N nodes should be used and what should be the optimal partial replication factor? This makes both a and b as variables to be determined since the equations relating them to n and N become the following inequalities: a + 2b N and a + b = n 1. This question cannot be answered by considering system reliability alone. Although a higher value of n will reduce the work per node due to parallelism, system reliability will go down making failures more likely. On the other hand, higher replication factors are likely to add more runtime overhead to the application, although they lead to a more resilient configuration. These trade offs can only be captured by computing the expected completion time for given a and b, and then picking the values of these variables that yield the minimum completion time. Parameter Description N Total number of system nodes n Number of application visible nodes a Number of non replicated nodes b Number of replica pairs r Partial replication factor (1 r 2) α Communication ratio ( α 1) γ Serial portion of application code W Work duration on single node W n Work duration on n parallel nodes W r Work duration with replication factor r M Mean Time To Interrupt (MTTI) C Checkpointing cost τ Checkpointing interval A. Job Model The first thing to determine, as n becomes variable, is the amount of work that will be distributed over each node and executed in parallel. Assuming that a particular job on a single node takes W units of time to finish execution, we use the following job model[12] to determine, W n,the time required to execute the same job on n parallel nodes without failures: W n = (1 γ)w/n + γw (5) where γ 1 represents the sequential part of the job. Smaller values of γ indicate higher potential for parallelism in the application. Larger values of γ, on the other hand, offer diminishing returns with increasing parallelism. Since increasing the value of r = (a + 2b)/(a + b), while keeping a + 2b fixed, means reducing n = a + b, higher values of γ are more favorable towards replication. In this work, most of the analysis we perform and the results we report will be for values of γ equal to, or close to,. This is for two reasons: i) as explained above, lower values of γ are more favorable towards no replication versus replication, and ii) HPC jobs typically should be highly parallelizable, and so γ is small in those settings. One could also use more sophisticated job models, taking into account the kind of computation and/or domain decomposition that the application performs. However, any model that is less than perfectly parallel is more favorable towards replication. Thus, by focusing on the perfectly parallel job model, we can ensure that conclusions drawn from the cases in which replication (full or partial) performs better than no-replication can be generalized to other job models as well. B. Overhead of Replication In addition to reducing the nodes over which work is parallelized, increasing replication also increases the overhead to message passing applications because of the communication required between replicas in order maintain consistency among them. The replication system then guarantees that every replica receives the same messages in the same order and that a copy of each message from one rank is sent to each replica in the destination rank[2]. This requires duplicating the communication of a process to its replica as well. While [2] provided estimates of overhead of replication based on implementation on a real system, that work only applies to full replication. An approach to model the overhead of partial replication was proposed in [4] using α, the ratio of application time spent in communication under no replication. According to that model, for an application executing under partial replication factor r, the time, W r, that includes the overhead of partial replication, is given by W r = (1 α)w n + rαw n = W n + (r 1)αW n (6) where W n is computed using Eq. 5. The rationale provided in [4] for this model is that every message involving a replicated node will be duplicated. Hence, the additional communication overhead will be linearly related to the replication factor, r. The experimental results in [4], though, showed Eq. 6 actually underestimated the overhead of partial replication. Similarly, [13] reported overheads with replication factor of 1.5 which, in some cases, went as high as 7% of the overhead of full replication (r = 2). Since this would indicate that the communication overhead of replication is not linear w.r.t the replication degree, which is the assumption for Eq. 6, we update it as W r = W n + r 1αW n (7) This estimate, while yielding the same overhead for full replication as Eq. 6, provides a more pessimistic overhead for partial replication compared to Eq. 6. Moreover, it matches with the experimental result of [13] on real systems since, for r = 1.5, the overhead will be 1/ 2.71% of the overhead of full replication. We, therefore, use Eq. 7 to compute and add the overhead of partial replication. C. Combining with Checkpointing Having figured out the failure-free execution time, W r, of a partially replicated application, we now proceed to compute the expected completion time of such an application under failures. Since even a fully replicated system is subject to failures when both nodes that are replicas of each other fail, both [2] and [4] combined checkpointing with a fully or partially replicated system. However, the checkpointing interval would be larger compared to the no replication case since it depends on the mean time to interrupt (MTTI). The MTTI, M, can be computed using the reliability as: M = R(t)dt (8) where R(t) is given by Eq. 1. Although, in subsequent sections, we will discuss closed form approximations for the MTTI for some specific cases of systems with exponential node distributions, in general it is not possible to evaluate the
5 integral in Eq. 8 analytically. We, therefore, resort to numerical integration to obtain the MTTI for our results. To compute the checkpointing interval, τ, we use Daly s[14] approximation to the optimum checkpointing interval, given a checkpointing cost, C and the MTTI M. This approximation was derived for exponential failure distributions. The failure distribution of a partially replicated system is not exponential even when the node failures are exponentially distributed[15]. However, [3] observed that Daly s approximation still yields results close to optimal even when the underlying failure distribution is not exponential. Hence, we use it as a reasonable approximation for the optimal checkpointing interval. In order to determine the expected completion time, we employ the approach used in [16] and [17] that approximates the completion time of a system with a generic failure distribution by computing the extra work done in an execution. The extra work during an execution consists of the time spent writing checkpoints and the lost work due to the failures. By considering each failure as a renewal process, the average fraction of extra time during an execution can be taken to be the same as the fraction of extra time between two consecutive failures. Let F (t) = 1 R(t) be the cumulative failure distribution and f(t) = F (t) be the failure density function. The extra time between consecutive failures will be given by E(extra) = Ct C M f(t)dt + kτ = + kτ (9) τ τ where k is the average fraction of work lost during a checkpointing interval due to failure. To compute k, note that kτ is equal to the expected time of failure within an interval of length τ. If we divide the time into segments of length τ, where segment t i = [τ(i 1), τi), and i > is an integer, we can compute the expected time of failure, f i, within segment t i as f i = τi τ(i 1) tf(t)dt/p i where p i = τi f(t)dt is τ(i 1) the probability of failure striking in interval t i. The average value of the failure within a τ interval will then be given by i=1 (f i τ(i 1))p i which we can divide by τ to obtain k. Since p i approaches as i increases, the value of this sum converges quickly, so a simple summation of the first few terms suffices. Even though the sum converges much earlier, for increased accuracy, we used the first 2 terms to compute the sum and obtain the value of k. Once we obtain E(extra), the useful work done between consecutive failures is given by M E(extra), where M is the MTTI. On average, therefore, the time it takes the system to complete a unit amount of work will be equal to M/(M E(extra)). Thus, the expected time it takes to finish work W r will be given by M E(W r ) = W r M E(extra) (1) where W r is determined from Eq. 7. This is the equation that we use to compute and compare the expected completion time of a system under different partial replication factors. D. Optimization Problem The purpose of computing the expected completion time was to find the replication factor r that minimizes it for a given Fig. 2. Expected Completion Time for different values of r normalized by the failure-free time it takes to finish the same work on all N nodes without replication or checkpointing. Node MTBF = 5 years. Checkpointing cost is taken to be 6 seconds. α = and also γ =. system. We thus formulate the search for r as an optimization problem as follows: minimize a,b subject to E(W r ) a + 2b N n = a + b 1 where r = (a + 2b)/(a + b) and a and b can only take nonnegative integer values. The inputs include work W, total number of system nodes N, individual node reliability functions 1 > g 1 (t) g N (t) >, checkpointing cost C, the parameter γ, and communication ratio, α. In subsequent sections, we will discuss our findings and results about the optimal r for different kinds of systems. In our results, we report the expected completion time normalized by W N, which is calculated from Eq. 5, and represents the time it takes to execute the job on all N nodes without replication or checkpointing and under no failures. IV. SYSTEM WITH IID NODES We start off with the simplest possible scenario, a system where the individual node failure distributions are identical. This has been the traditional assumption when analyzing fault tolerance techniques in HPC systems. Our goal is to explore whether there are cases in which partial replication, where r is strictly between 1 and 2, results in the lowest expected completion time. It should be noted that, since all nodes are identical, it does not matter which individual nodes are picked for replication or how they are paired together. A. Exponential Distribution We first consider a system where node failure probabilities are exponentially distributed. When taking both γ and α as, our optimization never yielded an optimal value of r strictly between 1 and 2 for any scenario we tested. This can also be seen in figure 2 where the expected completion time according to Eq. 1 (normalized by the time it takes to run the same job on N nodes without any fault tolerance and without failures) with different partial replication degrees is plotted against the
6 total number of nodes in the system. We see that the minimum time is always attained either when r = 1 or r = 2. The trend was the same for other node MTBF values, with the crossover between full and no replication occurring at higher node counts as the node MTBF increases. We further investigate this scenario analytically with the goal of determining if 1 < r < 2 is ever optimal for uniformly exponential node distributions when γ and α are both. Assuming that the configuration uses all of the system nodes N, so that a + 2b = N, and individual node failure rate is λ, we can write the MTTI, M, as: M = e aλt (1 (1 e λt ) 2 ) b dt = 2 N (e λt /2) N b (1 e λt /2) b dt (11) Since obtaining a closed form expression for the above integral is not possible, we try to provide a closed form approximation for M. Setting x = e λt /2 t = ln(2x)/λ in the above expression, we get M = 2N λ 1/2 x (N b 1) (1 x) b dx (12) We employ Laplace s method of approximating integrals[18] to derive an approximation of the above expression. We can rewrite the function inside the integral as x (N b 1) (1 x) b = e (N b 1)f(x) where f(x) = ln(x) + bln(1 x)/(k b 1). Assuming 2b < N, within the interval of integration f(x) is maximum at x = 1/2 which is the endpoint of the integration, so the integral can be approximated as 1/2 x (N b 1) (1 x) b dx e(n b 1)f(1/2) (N b 1)f (1/2) = (1/2)N N 2b 1 (13) Plugging this into the expression for MTTI above we obtain M 1/λ(N 2b 1). This reasonably approximates the MTTI as long as 2b is not close to N, which corresponds to the full replication case. To the best of our knowledge, this is the first closed form approximation of the MTTI of a partially replicated system with exponential node failure distributions with rate λ. Having obtained a closed form approximation for M in terms of N and b, we will infer the behavior of the expected completion time. Using Young s[19] expression for the expected completion time we get E(W ) = W (1 + C τ + (τ + C)2 2τM ) (14) where we take τ = 2CM which is also Young s approximation for the optimum checkpoint interval. Assuming that a perfectly parallel job takes unit time on N nodes without checkpoints and failures, the work per node will be r units when the system is partially replicated, since r = (a + 2b)/(a + b) = N/n. This means that W r = r, and E(W r ) then is given by 2C E(W r ) = r(1 + M + C M + C 2 2M 2CM ) (15) Fig. 3. Expected Completion Time for different values of r for exponential node distribution. Node MTBF = 5 years, γ =.1, Checkpointing cost = 6 seconds, α =.2 Since both r and M can be defined in terms of b and N, and since N is fixed, E(W r ) is a function of b. By taking the first and second derivative of this expression wrt b, we find that this expression has no local minimum over the range b < N/2 as long as M > C. For conciseness, we omit the calculations. This means, though, that the minimum of E(W r ) occurs only at one of the endpoints of r which correspond to either no replication or full replication. While eq. 15 is an approximation for the expected completion time, this analysis supports our numerical results that partial replication never yields optimal performance for jobs with α = γ = and when individual node failures are iid with exponential distributions. This is also consistent with the findings of [15] where it was observed that in cases where replication is better than no replication, full replication offers the best performance. When α >, it may theoretically be possible to have cases where the optimal r is strictly between 1 and 2. This is because there can be cases in which the expected completion time with α = is minimized when r = 2, but that minimum may shift to r < 2 if α >. That being said, we did not observe this for any values of parameters that we tried. As for when γ >, although it may be possible for 1 < r < 2 to be optimal, we again did not observe any such case. Figure 3 shows one example with both α > and γ >. We observe that, although the crossover between full and no replication happens earlier compared to Fig. 2, partial replication again does not win against the two extremes. Hence, our conclusion from this subsection is that partial replication is almost always never optimal for systems with iid exponential node distributions. B. Weibull Distribution Fig. 4 shows the completion times when individual node failures are given by the Weibull distribution. In practice, values of the shape parameter between and 1 are used for real world failures. In this paper, we show results with the parameter value of.7. Similar trends were observed with value of.5, but are omitted due to space limitations. In comparison to Fig. 2, we see that the crossover between full and no replication happens much earlier. Additionally, there are node counts where partial replication with degrees 1.25 and 1.5
7 Fig. 4. Expected Completion Time for different values of r with Weibull node failures. For the distribution, shape parameter =.7 and MTBF = 5 years. Checkpointing cost = 6 seconds and α = γ =. have lowest completion times. The range of node counts for which this happens is still quite small, however. The behavior remains almost similar when α or γ are made >, except that the crossover points are shifted. Increasing α shifts the crossover points to the right. For example, with α =.2, the crossover between no replication and r = 1.25 happens around 9 nodes instead of 7 nodes. Increasing γ, on the other hand, brings the crossover points to the left towards smaller node counts. For example, γ = 1 5 causes the crossover between r = 1 and r = 1.25 to happen at 65 nodes instead of 7 nodes. Moreover, just like in Figure 4, there is only a very small range of node counts for which partial replication provides the lowest completion time. Our main takeaway point from this section is that when the nodes in the system have identical failure distributions, which has been the traditional assumption in fault tolerance research for HPC, partial replication rarely provides any gains in performance against full and no replication. Depending on the number of nodes in the system, the choice should then only be between running an application under full replication or running it with no replication at all. V. SYSTEM WITH TWO TYPES OF NODES We now move one step further by considering a system where nodes are of two kinds: i) Good, which have a low probability of failure, and ii) Bad, which have a higher probability of failure. We assume that all the Good nodes have the same failure distribution and all the Bad nodes have the same failure distribution. This can be a scenario in a system where individual system nodes can be approximately divided into two categories: those which are more prone to failures and those which are less prone to failures. Let N G be the number of Good nodes and N B be the number of bad nodes, such that N G +N B = N. Thanks to the main result of section II, we know that if partial replication is to be employed, we should start replicating from the lower end. Moreover, within the nodes to be replicated, pairing should be done as indicated by Figure 1. Using this knowledge, we can enumerate all possible cases for different partial replication Fig. 5. Possible cases of partial replication for system with Good and Bad nodes. Nodes within the replicated set are paired according to the arrangement depicted in Figure 1. For this figure, the number of Good nodes is taken to be higher than the number of Bad nodes. If the number of Good nodes is strictly lower than the number of Bad nodes, cases 5 and 6 above will not happen. degrees of a Good-Bad node system. This enumeration is depicted in Fig. 5. Starting from the no replication case, increasing replication degree would mean initially replicating the Bad nodes among themselves. Case 3 is the boundary of case 2, when all of the Bad nodes have been replicated. As the replication degree is further increased, some of the Good nodes enter the replicated set as well. Case 4 thus contains two kinds of replica pairs: a Good node paired with a Bad node, and a Bad node paired with a Bad node. Case 5 is again a boundary of case 4 where all replica pairs consist of a Good and a Bad node each. The full replication case contains additional node pairs depending on the difference between the number of Good and Bad nodes. We will explore how the average completion times of these different cases fare against each other in different settings. Such an analysis can be useful for system administrators in deciding the optimal replication scheme that will result in the lowest job completion time on average, based on information about system nodes and other parameters. A. Exponential Distribution Assuming all the nodes in the system have exponential failure distribution, we can take the failure rate of Good nodes as λ g and the failure rate of the Bad nodes as λ b, where λ g λ b. Since case 2 in Fig. 5 is quite similar to the partially replicated iid system in section IV, we first attempt to approximate its MTTI. For this case, we can write the reliability of the system as R(t) = e N Gλ gt e (N B 2b)λ b t (2e λ bt e 2λ bt ) b (16) where 2b is the number of Bad nodes that are replicated. To obtain the MTTI of such a system, we can follow the same approach as in section IV to approximate the integral of R(t). This yields the following approximation for the MTTI, M, of the system in case 2 M 1 N G λ g + (N B 2b 1)λ b (17) This expression again reasonably approximates the MTTI as long as 2b is not close to N B.
8 Fig. 6. Execution time of different partially replicated executions *. N G = 1 6, N B = 8 1 5, λ g = 1/5 years, C = 6 seconds and α = γ =. * Using Eq. 1 for the No Replication case in the left figure resulted in negative values when Bad node MTBF was low, because E(extra) became greater than MTTI in those cases. We instead used Daly s[14] expression to approximate the expected completion time for No replication, which usually provides a lower value than Eq. 1. We do this only for the no replication case in the plot on the left. Expected times for the other schemes are still computed using Eq. 1. Similar to section IV, we use eq. 17 to understand the behavior of the expected completion time of the application wrt b when α = γ =. We plug M into eq. 15 along with r for this case, which is equal to (N G +N B )/(N G +N B b). Taking the first and second derivatives of the resulting expression wrt b, we again conclude that the function has no local minima and thus the minimum occurs only at the extremes, i.e. b = (no replication), or b = N B /2 (all Bad nodes replicated among themselves). This indicates that, between cases 1, 2 and 3, the minimum expected time can only be achieved by cases 1 and 3 for exponential node failures with α = γ =. We again mention that while this derivation holds only for the approximations of M and expected completion time, our numerical search also never yielded any scenarios in which case 2 resulted in lower average time than both cases 1 and 3. While we were unable to obtain an approximation of MTTI for case 4, our numerical search indicates that the minimum average completion time occurs again at the boundary cases, i.e. 3 or 5. This means that, in general, we need only consider the boundaries of partial replication in a Good-Bad node system. As an example, Figure 6 shows the expected completion time of full and no replication along with cases 3 and 5 from Figure 5. From the plot on the left in Figure 6, we see that replicating the Bad nodes among themselves (Case 3) yields the lowest completion time. Case 5, which replicates each Bad node with a Good node, offered almost the same performance as full replication. While we do not show the results with higher Bad node MTBF, we saw that no-replication started outperforming Case 3 when Bad node MTBF went above 2 years, with the same parameters as in Figure 6. In order to find out if there can be a scenario where Bad node MTBF is so low that not using the Bad nodes, replicated or not, at all is the best performing scheme, we reduced the Bad node MTBF to the order of days and also compare with a no replicated configuration using the Good nodes only (a = N G, b = ). The plot on the right in figure 6 depicts the results. We see that only in the unrealistic case of individual Bad node MTBF dropping to the order of a few day does using Good nodes only outperform Case 3. We deduce from this that, as Fig. 7. Expected time vs % of Bad Nodes in the system. N = Bad Node MTBF = 5 years. Other parameters are the same as in Fig 6. long as Bad node MTBF is larger than a few days, utilizing the Bad nodes results in lower completion time on average instead of not using them at all. Whenever Bad node MTBF is so low that using them without replication hurts application runtime, the lowest expected time can be achieved by replicating the Bad nodes among themselves and still utilizing them along with the non-replicated Good nodes. Figure 7 shows the behavior of the schemes with varying percentage of Bad nodes in the system, while the total number of nodes, N, is kept constant. When all nodes are Good, no replication is the best choice. However, as further nodes are added, no replication has a much higher normalized time. The normalized time for the no replication scheme which uses the Good nodes only also increases as % of N B in the system increases. This is because the time is normalized by W N which is the failure free time of running the job on all N system nodes. In all cases, however, we see that Case 3 offers the best expected completion time. Figure 8 shows the behavior of the different partial repli-
9 Fig. 8. Expected time for different values of α when Bad Node MTBF = 5 years. Other parameters are the same as in Figure 6. The expected time for no replication using all system nodes is much higher than all other schemes so it is omitted from the plot. Fig. 9. Execution time of different replication schemes with Weibull node failures. N G = 1 4, N B = and Good node MTBF = 5 years. The other parameters are the same as in Fig. 6. cation schemes for different values of α. The time for all the partial replication schemes increases with increasing α. However, since Case 3 has smaller replication factor than Cases 5 and 6, the impact of α is much smaller. Only when α.8 does partial replication of Case 3 start losing to no replication using Good nodes only. Hence, we can say that for most practical values of α, using the Bad nodes with full replication amongst themselves is still better than not using them at all. We do not present similar plots for the parameter γ due to lack of space. The impact of increasing γ is to favor more the cases with higher replication factor, r. Hence, as γ increases, the lowest completion time shifts from case 3 towards full replication (r = 2). B. Weibull Distribution For node failures given by the Weibull distribution, we assume that all nodes distribution have the same shape parameter. Only the rate parameter, λ, is different for the Good and Bad nodes. With this assumption, and again taking λ g λ b, the Good node will always be more reliable than the Bad node Fig. 1. Expected completion time versus r for different values of α. The values of other parameters are: γ =, C = 3 seconds and each category contains 1k nodes, for a total of 5k system nodes. throughout its lifetime. Hence, this assumption allows us to apply the theorem of section II when deciding the pairing of nodes and so the possible partial replication schemes will still be given by Fig. 5. Figure 9 shows the normalized runtimes of different partial replication cases similar to the exponential distribution subsection, but over a larger range of Bad node MTBFs. We again see that with lower Bad node MTBF, replicating Bad nodes among themselves yields the lowest expected completion time. Moreover, this happens at system scales much smaller than the ones for exponential distribution. We omit the plots for the cases when α >. The trends, however, were the same as the ones observed for exponential distribution. Based on the results from both exponential and Weibull distributions, we conclude this section with the following insight: If an HPC system has some nodes that are more likely to fail than others, those nodes can still be utilized to achieve performance gains. When the likelihood of failures in such Bad nodes is not too high, those nodes can simply be used alongside the rest of the system nodes to execute a job in parallel, without replication. If, however, the likelihood of failures in those nodes increases, they can be replicated among themselves and still be used along with the other system nodes to provide better performance compared to the case of not using such nodes at all. VI. SYSTEMS BEYOND TWO CATEGORIES OF NODES The optimization problem formulated in section III is capable of finding the optimal r for a system with any set of non-uniform node reliability values g i (t), as long as they maintain the ordering g 1 (t) g 2 (t) g N (t). This is useful when all the individual node reliability functions are known. However, we do not present any results for such a generic system because they don t provide any interesting insights about r or the behavior of the expected completion time. We, therefore, only present one example of a system with 5 categories of nodes. The MTBFs of the five categories range from 1 to 5 years in increments of 1 year, with each category having the same number of nodes. Figure 1 shows
10 the normalized expected completion time, using Eq 1, versus the partial replication factor, r, for different values of α. We kept a + 2b = N instead of the inequality a + 2b N. This is because, similar to the conclusions for the Good-Bad node system, we usually found that using all the nodes in the system is beneficial, as long as the lowest MTBF nodes do not have unrealistically low values of the MTBF. We can make several observations from Fig. 1. For all values of α, the optimal r is less than 2. For α =, optimal value of r 1.42, but for other values of α, the optimal value of r = These results highlight the importance of having and utilizing a deeper understanding of the failure characteristics of the underlying system. If, for example, instead of considering the 5 categories of nodes, one took the average value of the node MTBF across 5 categories as 2.5 years, and used that to decide the replication degree, the answer would be to fully replicate the execution. However, as we can see in the figure, partially replicating the right nodes can result in lower expected completion time than full replication. In fact, if the decision to fully replicate is made without the knowledge of the different categories of nodes, the replica pairing may not be the same as that described in section II, and may lead to even higher expected completion time. We make one final remark about the behavior versus r. We see in Fig. 1 that the curve is piecewise smooth in segments. The values of r at the boundary points of these segments correspond to the boundary cases of different partial replication configurations. So, for example, if only the nodes in the lowest MTBF category are all replicated among themselves, we get r = 1.1. We see in Fig. 1 that for 1 r 1.1, the curve is smooth. Similarly, the next smooth segment finishes at r = 1.25, which is the boundary case achieved when the lowest MTBF category is fully replicated with the next lowest category. Although we do not have any analytical results about this, our investigations of multiple scenarios always yielded the optimal r on one of these boundary cases. This indicates that, in cases where node MTBFs take a small set of discrete values, rather than doing a full search for the best r, it may be a reasonable heuristic to only consider boundary cases and pick r with the lowest completion time. VII. RELATED WORK Full[2] and partial[4] replication were both proposed for large scale systems when failures become frequent. A deeper analysis of pure replication and its comparison with simple checkpoint/restart was carried out in [3]. For partial replication, [15] provides a limited analysis and comparison with full and no replication. Even though our focus in this work is on systems with non-uniform failure distributions of individual nodes, section IV provides a more detailed analysis of partial replication with iid node failures. We provide theoretical results for the MTTI and evidence that partial replication is never optimal on such systems. All of the above have assumed systems with identical nodes in their analyses. We are only aware of two works that distinguish between different failure likelihoods in the underlying hardware. [2] considers two instances of an application running on two different platforms, that execute at different speeds and are subject to different failure rates. Our work differs from it in several aspects. Firstly, the paper considers group replication, where a complete instance of the parallel application is executed redundantly, rather than replicating individual processes. This avoids communication between instances but a single failure causes the whole instance to fail. Secondly, the framework does not allow for partial replication. Thirdly, their work assumes a single platform failure distribution, without considering the underlying nodes in the system. [21] is closer to our work since it considers individual node failure rates. However, it only performs a post hoc analysis based on failure logs to determine which nodes have the most failures and how many of those failures could be eliminated by duplicating those nodes with spare nodes. Moreover, this work only considers the improvement in MTTI without looking at the impact on completion time. Our work provides a comprehensive theoretical framework which not only determines how the nodes should be duplicated, but also when it pays off to duplicate some nodes in the system. While our work looks at partial redundancy in the presence of non-identical node failures, there are papers that consider the problem of selectively replicating tasks based on criticality[22][23][24]. These works replicate tasks from an application task dependence graph by measuring the criticality of an individual task. The idea of criticality is orthogonal to our task of selectively replicating nodes based on their individual reliability. Our work, additionally, is application agnostic since it only considers the failure distributions of individual nodes. VIII. CONCLUSION We explored partial replication for HPC systems where individual nodes have non-identical failure distributions. We provided theoretical results on the optimal way to divide the nodes into replicated and non replicated sets and to pair the nodes in the replicated sets. By computing the MTTI and expected completion time of a job executed in a partially replicated configuration, we also investigated the optimal fraction of replication. We found that, while rarely optimal for IID node failure platforms, partial replication can yield the best performance for systems comprising of nodes with different failure rates. One direction of future work is to explore the energy/performance trade-off of partial replication. While our work has demonstrated that partial replication for systems with non-identical node failures can often provide the best performance, it should be explored if that performance gain is worth spending the extra energy on the replicated nodes. Another direction of future work is to consider a mix of jobs instead of a single job. Solving for multiple jobs will require changing the metric from completion time to average job turnaround time and will also expand the search space to include options such as starting jobs in parallel over divided resources or running them one after the other. ACKNOWLEDGMENT We are thankful to reviewers for their constructive feedback that has helped us improve the quality of this paper. This research is based in part upon work supported by the Department of Energy under contract DE-SC This research was supported in part by the University of Pittsburgh Center for Research Computing through the resources provided.
Yao s Minimax Principle
 Complexity of algorithms The complexity of an algorithm is usually measured with respect to the size of the input, where size may for example refer to the length of a binary word describing the input,
Complexity of algorithms The complexity of an algorithm is usually measured with respect to the size of the input, where size may for example refer to the length of a binary word describing the input,
Martingale Pricing Theory in Discrete-Time and Discrete-Space Models
 IEOR E4707: Foundations of Financial Engineering c 206 by Martin Haugh Martingale Pricing Theory in Discrete-Time and Discrete-Space Models These notes develop the theory of martingale pricing in a discrete-time,
IEOR E4707: Foundations of Financial Engineering c 206 by Martin Haugh Martingale Pricing Theory in Discrete-Time and Discrete-Space Models These notes develop the theory of martingale pricing in a discrete-time,
THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE
 THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE GÜNTER ROTE Abstract. A salesperson wants to visit each of n objects that move on a line at given constant speeds in the shortest possible time,
THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE GÜNTER ROTE Abstract. A salesperson wants to visit each of n objects that move on a line at given constant speeds in the shortest possible time,
Random Variables and Probability Distributions
 Chapter 3 Random Variables and Probability Distributions Chapter Three Random Variables and Probability Distributions 3. Introduction An event is defined as the possible outcome of an experiment. In engineering
Chapter 3 Random Variables and Probability Distributions Chapter Three Random Variables and Probability Distributions 3. Introduction An event is defined as the possible outcome of an experiment. In engineering
ELEMENTS OF MONTE CARLO SIMULATION
 APPENDIX B ELEMENTS OF MONTE CARLO SIMULATION B. GENERAL CONCEPT The basic idea of Monte Carlo simulation is to create a series of experimental samples using a random number sequence. According to the
APPENDIX B ELEMENTS OF MONTE CARLO SIMULATION B. GENERAL CONCEPT The basic idea of Monte Carlo simulation is to create a series of experimental samples using a random number sequence. According to the
ECON 459 Game Theory. Lecture Notes Auctions. Luca Anderlini Spring 2017
 ECON 459 Game Theory Lecture Notes Auctions Luca Anderlini Spring 2017 These notes have been used and commented on before. If you can still spot any errors or have any suggestions for improvement, please
ECON 459 Game Theory Lecture Notes Auctions Luca Anderlini Spring 2017 These notes have been used and commented on before. If you can still spot any errors or have any suggestions for improvement, please
Constrained Sequential Resource Allocation and Guessing Games
 4946 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 11, NOVEMBER 2008 Constrained Sequential Resource Allocation and Guessing Games Nicholas B. Chang and Mingyan Liu, Member, IEEE Abstract In this
4946 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 11, NOVEMBER 2008 Constrained Sequential Resource Allocation and Guessing Games Nicholas B. Chang and Mingyan Liu, Member, IEEE Abstract In this
The Value of Information in Central-Place Foraging. Research Report
 The Value of Information in Central-Place Foraging. Research Report E. J. Collins A. I. Houston J. M. McNamara 22 February 2006 Abstract We consider a central place forager with two qualitatively different
The Value of Information in Central-Place Foraging. Research Report E. J. Collins A. I. Houston J. M. McNamara 22 February 2006 Abstract We consider a central place forager with two qualitatively different
Interpolation. 1 What is interpolation? 2 Why are we interested in this?
 Interpolation 1 What is interpolation? For a certain function f (x we know only the values y 1 = f (x 1,,y n = f (x n For a point x different from x 1,,x n we would then like to approximate f ( x using
Interpolation 1 What is interpolation? For a certain function f (x we know only the values y 1 = f (x 1,,y n = f (x n For a point x different from x 1,,x n we would then like to approximate f ( x using
Sublinear Time Algorithms Oct 19, Lecture 1
 0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
Multi-period mean variance asset allocation: Is it bad to win the lottery?
 Multi-period mean variance asset allocation: Is it bad to win the lottery? Peter Forsyth 1 D.M. Dang 1 1 Cheriton School of Computer Science University of Waterloo Guangzhou, July 28, 2014 1 / 29 The Basic
Multi-period mean variance asset allocation: Is it bad to win the lottery? Peter Forsyth 1 D.M. Dang 1 1 Cheriton School of Computer Science University of Waterloo Guangzhou, July 28, 2014 1 / 29 The Basic
Characterization of the Optimum
 ECO 317 Economics of Uncertainty Fall Term 2009 Notes for lectures 5. Portfolio Allocation with One Riskless, One Risky Asset Characterization of the Optimum Consider a risk-averse, expected-utility-maximizing
ECO 317 Economics of Uncertainty Fall Term 2009 Notes for lectures 5. Portfolio Allocation with One Riskless, One Risky Asset Characterization of the Optimum Consider a risk-averse, expected-utility-maximizing
Efficiency and Herd Behavior in a Signalling Market. Jeffrey Gao
 Efficiency and Herd Behavior in a Signalling Market Jeffrey Gao ABSTRACT This paper extends a model of herd behavior developed by Bikhchandani and Sharma (000) to establish conditions for varying levels
Efficiency and Herd Behavior in a Signalling Market Jeffrey Gao ABSTRACT This paper extends a model of herd behavior developed by Bikhchandani and Sharma (000) to establish conditions for varying levels
MATH 425: BINOMIAL TREES
 MATH 425: BINOMIAL TREES G. BERKOLAIKO Summary. These notes will discuss: 1-level binomial tree for a call, fair price and the hedging procedure 1-level binomial tree for a general derivative, fair price
MATH 425: BINOMIAL TREES G. BERKOLAIKO Summary. These notes will discuss: 1-level binomial tree for a call, fair price and the hedging procedure 1-level binomial tree for a general derivative, fair price
4: SINGLE-PERIOD MARKET MODELS
 4: SINGLE-PERIOD MARKET MODELS Marek Rutkowski School of Mathematics and Statistics University of Sydney Semester 2, 2016 M. Rutkowski (USydney) Slides 4: Single-Period Market Models 1 / 87 General Single-Period
4: SINGLE-PERIOD MARKET MODELS Marek Rutkowski School of Mathematics and Statistics University of Sydney Semester 2, 2016 M. Rutkowski (USydney) Slides 4: Single-Period Market Models 1 / 87 General Single-Period
Revenue Management Under the Markov Chain Choice Model
 Revenue Management Under the Markov Chain Choice Model Jacob B. Feldman School of Operations Research and Information Engineering, Cornell University, Ithaca, New York 14853, USA jbf232@cornell.edu Huseyin
Revenue Management Under the Markov Chain Choice Model Jacob B. Feldman School of Operations Research and Information Engineering, Cornell University, Ithaca, New York 14853, USA jbf232@cornell.edu Huseyin
Pricing Dynamic Solvency Insurance and Investment Fund Protection
 Pricing Dynamic Solvency Insurance and Investment Fund Protection Hans U. Gerber and Gérard Pafumi Switzerland Abstract In the first part of the paper the surplus of a company is modelled by a Wiener process.
Pricing Dynamic Solvency Insurance and Investment Fund Protection Hans U. Gerber and Gérard Pafumi Switzerland Abstract In the first part of the paper the surplus of a company is modelled by a Wiener process.
Game Theory and Economics Prof. Dr. Debarshi Das Department of Humanities and Social Sciences Indian Institute of Technology, Guwahati
 Game Theory and Economics Prof. Dr. Debarshi Das Department of Humanities and Social Sciences Indian Institute of Technology, Guwahati Module No. # 03 Illustrations of Nash Equilibrium Lecture No. # 04
Game Theory and Economics Prof. Dr. Debarshi Das Department of Humanities and Social Sciences Indian Institute of Technology, Guwahati Module No. # 03 Illustrations of Nash Equilibrium Lecture No. # 04
Tug of War Game. William Gasarch and Nick Sovich and Paul Zimand. October 6, Abstract
 Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Likelihood-based Optimization of Threat Operation Timeline Estimation
 12th International Conference on Information Fusion Seattle, WA, USA, July 6-9, 2009 Likelihood-based Optimization of Threat Operation Timeline Estimation Gregory A. Godfrey Advanced Mathematics Applications
12th International Conference on Information Fusion Seattle, WA, USA, July 6-9, 2009 Likelihood-based Optimization of Threat Operation Timeline Estimation Gregory A. Godfrey Advanced Mathematics Applications
Integer Programming Models
 Integer Programming Models Fabio Furini December 10, 2014 Integer Programming Models 1 Outline 1 Combinatorial Auctions 2 The Lockbox Problem 3 Constructing an Index Fund Integer Programming Models 2 Integer
Integer Programming Models Fabio Furini December 10, 2014 Integer Programming Models 1 Outline 1 Combinatorial Auctions 2 The Lockbox Problem 3 Constructing an Index Fund Integer Programming Models 2 Integer
Truncated Life Test Sampling Plan under Log-Logistic Model
 ISSN: 231-753 (An ISO 327: 2007 Certified Organization) Truncated Life Test Sampling Plan under Log-Logistic Model M.Gomathi 1, Dr. S. Muthulakshmi 2 1 Research scholar, Department of mathematics, Avinashilingam
ISSN: 231-753 (An ISO 327: 2007 Certified Organization) Truncated Life Test Sampling Plan under Log-Logistic Model M.Gomathi 1, Dr. S. Muthulakshmi 2 1 Research scholar, Department of mathematics, Avinashilingam
January 26,
 January 26, 2015 Exercise 9 7.c.1, 7.d.1, 7.d.2, 8.b.1, 8.b.2, 8.b.3, 8.b.4,8.b.5, 8.d.1, 8.d.2 Example 10 There are two divisions of a firm (1 and 2) that would benefit from a research project conducted
January 26, 2015 Exercise 9 7.c.1, 7.d.1, 7.d.2, 8.b.1, 8.b.2, 8.b.3, 8.b.4,8.b.5, 8.d.1, 8.d.2 Example 10 There are two divisions of a firm (1 and 2) that would benefit from a research project conducted
1 Appendix A: Definition of equilibrium
 Online Appendix to Partnerships versus Corporations: Moral Hazard, Sorting and Ownership Structure Ayca Kaya and Galina Vereshchagina Appendix A formally defines an equilibrium in our model, Appendix B
Online Appendix to Partnerships versus Corporations: Moral Hazard, Sorting and Ownership Structure Ayca Kaya and Galina Vereshchagina Appendix A formally defines an equilibrium in our model, Appendix B
New Meaningful Effects in Modern Capital Structure Theory
 104 Journal of Reviews on Global Economics, 2018, 7, 104-122 New Meaningful Effects in Modern Capital Structure Theory Peter Brusov 1,*, Tatiana Filatova 2, Natali Orekhova 3, Veniamin Kulik 4 and Irwin
104 Journal of Reviews on Global Economics, 2018, 7, 104-122 New Meaningful Effects in Modern Capital Structure Theory Peter Brusov 1,*, Tatiana Filatova 2, Natali Orekhova 3, Veniamin Kulik 4 and Irwin
,,, be any other strategy for selling items. It yields no more revenue than, based on the
 ONLINE SUPPLEMENT Appendix 1: Proofs for all Propositions and Corollaries Proof of Proposition 1 Proposition 1: For all 1,2,,, if, is a non-increasing function with respect to (henceforth referred to as
ONLINE SUPPLEMENT Appendix 1: Proofs for all Propositions and Corollaries Proof of Proposition 1 Proposition 1: For all 1,2,,, if, is a non-increasing function with respect to (henceforth referred to as
Exam M Fall 2005 PRELIMINARY ANSWER KEY
 Exam M Fall 005 PRELIMINARY ANSWER KEY Question # Answer Question # Answer 1 C 1 E C B 3 C 3 E 4 D 4 E 5 C 5 C 6 B 6 E 7 A 7 E 8 D 8 D 9 B 9 A 10 A 30 D 11 A 31 A 1 A 3 A 13 D 33 B 14 C 34 C 15 A 35 A
Exam M Fall 005 PRELIMINARY ANSWER KEY Question # Answer Question # Answer 1 C 1 E C B 3 C 3 E 4 D 4 E 5 C 5 C 6 B 6 E 7 A 7 E 8 D 8 D 9 B 9 A 10 A 30 D 11 A 31 A 1 A 3 A 13 D 33 B 14 C 34 C 15 A 35 A
Game Theory: Normal Form Games
 Game Theory: Normal Form Games Michael Levet June 23, 2016 1 Introduction Game Theory is a mathematical field that studies how rational agents make decisions in both competitive and cooperative situations.
Game Theory: Normal Form Games Michael Levet June 23, 2016 1 Introduction Game Theory is a mathematical field that studies how rational agents make decisions in both competitive and cooperative situations.
CHOICE THEORY, UTILITY FUNCTIONS AND RISK AVERSION
 CHOICE THEORY, UTILITY FUNCTIONS AND RISK AVERSION Szabolcs Sebestyén szabolcs.sebestyen@iscte.pt Master in Finance INVESTMENTS Sebestyén (ISCTE-IUL) Choice Theory Investments 1 / 65 Outline 1 An Introduction
CHOICE THEORY, UTILITY FUNCTIONS AND RISK AVERSION Szabolcs Sebestyén szabolcs.sebestyen@iscte.pt Master in Finance INVESTMENTS Sebestyén (ISCTE-IUL) Choice Theory Investments 1 / 65 Outline 1 An Introduction
Properties of IRR Equation with Regard to Ambiguity of Calculating of Rate of Return and a Maximum Number of Solutions
 Properties of IRR Equation with Regard to Ambiguity of Calculating of Rate of Return and a Maximum Number of Solutions IRR equation is widely used in financial mathematics for different purposes, such
Properties of IRR Equation with Regard to Ambiguity of Calculating of Rate of Return and a Maximum Number of Solutions IRR equation is widely used in financial mathematics for different purposes, such
Supplementary Material for: Belief Updating in Sequential Games of Two-Sided Incomplete Information: An Experimental Study of a Crisis Bargaining
 Supplementary Material for: Belief Updating in Sequential Games of Two-Sided Incomplete Information: An Experimental Study of a Crisis Bargaining Model September 30, 2010 1 Overview In these supplementary
Supplementary Material for: Belief Updating in Sequential Games of Two-Sided Incomplete Information: An Experimental Study of a Crisis Bargaining Model September 30, 2010 1 Overview In these supplementary
1.1 Basic Financial Derivatives: Forward Contracts and Options
 Chapter 1 Preliminaries 1.1 Basic Financial Derivatives: Forward Contracts and Options A derivative is a financial instrument whose value depends on the values of other, more basic underlying variables
Chapter 1 Preliminaries 1.1 Basic Financial Derivatives: Forward Contracts and Options A derivative is a financial instrument whose value depends on the values of other, more basic underlying variables
Mossin s Theorem for Upper-Limit Insurance Policies
 Mossin s Theorem for Upper-Limit Insurance Policies Harris Schlesinger Department of Finance, University of Alabama, USA Center of Finance & Econometrics, University of Konstanz, Germany E-mail: hschlesi@cba.ua.edu
Mossin s Theorem for Upper-Limit Insurance Policies Harris Schlesinger Department of Finance, University of Alabama, USA Center of Finance & Econometrics, University of Konstanz, Germany E-mail: hschlesi@cba.ua.edu
An Experimental Study of the Behaviour of the Proxel-Based Simulation Algorithm
 An Experimental Study of the Behaviour of the Proxel-Based Simulation Algorithm Sanja Lazarova-Molnar, Graham Horton Otto-von-Guericke-Universität Magdeburg Abstract The paradigm of the proxel ("probability
An Experimental Study of the Behaviour of the Proxel-Based Simulation Algorithm Sanja Lazarova-Molnar, Graham Horton Otto-von-Guericke-Universität Magdeburg Abstract The paradigm of the proxel ("probability
Notes on Intertemporal Optimization
 Notes on Intertemporal Optimization Econ 204A - Henning Bohn * Most of modern macroeconomics involves models of agents that optimize over time. he basic ideas and tools are the same as in microeconomics,
Notes on Intertemporal Optimization Econ 204A - Henning Bohn * Most of modern macroeconomics involves models of agents that optimize over time. he basic ideas and tools are the same as in microeconomics,
Maximum Contiguous Subsequences
 Chapter 8 Maximum Contiguous Subsequences In this chapter, we consider a well-know problem and apply the algorithm-design techniques that we have learned thus far to this problem. While applying these
Chapter 8 Maximum Contiguous Subsequences In this chapter, we consider a well-know problem and apply the algorithm-design techniques that we have learned thus far to this problem. While applying these
Arbitrage-Free Pricing of XVA for American Options in Discrete Time
 Arbitrage-Free Pricing of XVA for American Options in Discrete Time by Tingwen Zhou A Thesis Submitted to the Faculty of the WORCESTER POLYTECHNIC INSTITUTE In partial fulfillment of the requirements for
Arbitrage-Free Pricing of XVA for American Options in Discrete Time by Tingwen Zhou A Thesis Submitted to the Faculty of the WORCESTER POLYTECHNIC INSTITUTE In partial fulfillment of the requirements for
Implementation of a Perfectly Secure Distributed Computing System
 Implementation of a Perfectly Secure Distributed Computing System Rishi Kacker and Matt Pauker Stanford University {rkacker,mpauker}@cs.stanford.edu Abstract. The increased interest in financially-driven
Implementation of a Perfectly Secure Distributed Computing System Rishi Kacker and Matt Pauker Stanford University {rkacker,mpauker}@cs.stanford.edu Abstract. The increased interest in financially-driven
On the Optimality of a Family of Binary Trees Techical Report TR
 On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
Essays on Some Combinatorial Optimization Problems with Interval Data
 Essays on Some Combinatorial Optimization Problems with Interval Data a thesis submitted to the department of industrial engineering and the institute of engineering and sciences of bilkent university
Essays on Some Combinatorial Optimization Problems with Interval Data a thesis submitted to the department of industrial engineering and the institute of engineering and sciences of bilkent university
Reliable and Energy-Efficient Resource Provisioning and Allocation in Cloud Computing
 Reliable and Energy-Efficient Resource Provisioning and Allocation in Cloud Computing Yogesh Sharma, Bahman Javadi, Weisheng Si School of Computing, Engineering and Mathematics Western Sydney University,
Reliable and Energy-Efficient Resource Provisioning and Allocation in Cloud Computing Yogesh Sharma, Bahman Javadi, Weisheng Si School of Computing, Engineering and Mathematics Western Sydney University,
[D7] PROBABILITY DISTRIBUTION OF OUTSTANDING LIABILITY FROM INDIVIDUAL PAYMENTS DATA Contributed by T S Wright
![[D7] PROBABILITY DISTRIBUTION OF OUTSTANDING LIABILITY FROM INDIVIDUAL PAYMENTS DATA Contributed by T S Wright [D7] PROBABILITY DISTRIBUTION OF OUTSTANDING LIABILITY FROM INDIVIDUAL PAYMENTS DATA Contributed by T S Wright](/thumbs/92/107898301.jpg) Faculty and Institute of Actuaries Claims Reserving Manual v.2 (09/1997) Section D7 [D7] PROBABILITY DISTRIBUTION OF OUTSTANDING LIABILITY FROM INDIVIDUAL PAYMENTS DATA Contributed by T S Wright 1. Introduction
Faculty and Institute of Actuaries Claims Reserving Manual v.2 (09/1997) Section D7 [D7] PROBABILITY DISTRIBUTION OF OUTSTANDING LIABILITY FROM INDIVIDUAL PAYMENTS DATA Contributed by T S Wright 1. Introduction
Eco504 Spring 2010 C. Sims FINAL EXAM. β t 1 2 φτ2 t subject to (1)
 Eco54 Spring 21 C. Sims FINAL EXAM There are three questions that will be equally weighted in grading. Since you may find some questions take longer to answer than others, and partial credit will be given
Eco54 Spring 21 C. Sims FINAL EXAM There are three questions that will be equally weighted in grading. Since you may find some questions take longer to answer than others, and partial credit will be given
Notes on the symmetric group
 Notes on the symmetric group 1 Computations in the symmetric group Recall that, given a set X, the set S X of all bijections from X to itself (or, more briefly, permutations of X) is group under function
Notes on the symmetric group 1 Computations in the symmetric group Recall that, given a set X, the set S X of all bijections from X to itself (or, more briefly, permutations of X) is group under function
3.4 Copula approach for modeling default dependency. Two aspects of modeling the default times of several obligors
 3.4 Copula approach for modeling default dependency Two aspects of modeling the default times of several obligors 1. Default dynamics of a single obligor. 2. Model the dependence structure of defaults
3.4 Copula approach for modeling default dependency Two aspects of modeling the default times of several obligors 1. Default dynamics of a single obligor. 2. Model the dependence structure of defaults
Week 2 Quantitative Analysis of Financial Markets Hypothesis Testing and Confidence Intervals
 Week 2 Quantitative Analysis of Financial Markets Hypothesis Testing and Confidence Intervals Christopher Ting http://www.mysmu.edu/faculty/christophert/ Christopher Ting : christopherting@smu.edu.sg :
Week 2 Quantitative Analysis of Financial Markets Hypothesis Testing and Confidence Intervals Christopher Ting http://www.mysmu.edu/faculty/christophert/ Christopher Ting : christopherting@smu.edu.sg :
DRAFT. 1 exercise in state (S, t), π(s, t) = 0 do not exercise in state (S, t) Review of the Risk Neutral Stock Dynamics
 Chapter 12 American Put Option Recall that the American option has strike K and maturity T and gives the holder the right to exercise at any time in [0, T ]. The American option is not straightforward
Chapter 12 American Put Option Recall that the American option has strike K and maturity T and gives the holder the right to exercise at any time in [0, T ]. The American option is not straightforward
Lecture 4: Divide and Conquer
 Lecture 4: Divide and Conquer Divide and Conquer Merge sort is an example of a divide-and-conquer algorithm Recall the three steps (at each level to solve a divideand-conquer problem recursively Divide
Lecture 4: Divide and Conquer Divide and Conquer Merge sort is an example of a divide-and-conquer algorithm Recall the three steps (at each level to solve a divideand-conquer problem recursively Divide
Self-organized criticality on the stock market
 Prague, January 5th, 2014. Some classical ecomomic theory In classical economic theory, the price of a commodity is determined by demand and supply. Let D(p) (resp. S(p)) be the total demand (resp. supply)
Prague, January 5th, 2014. Some classical ecomomic theory In classical economic theory, the price of a commodity is determined by demand and supply. Let D(p) (resp. S(p)) be the total demand (resp. supply)
MATH3075/3975 FINANCIAL MATHEMATICS TUTORIAL PROBLEMS
 MATH307/37 FINANCIAL MATHEMATICS TUTORIAL PROBLEMS School of Mathematics and Statistics Semester, 04 Tutorial problems should be used to test your mathematical skills and understanding of the lecture material.
MATH307/37 FINANCIAL MATHEMATICS TUTORIAL PROBLEMS School of Mathematics and Statistics Semester, 04 Tutorial problems should be used to test your mathematical skills and understanding of the lecture material.
Gamma Distribution Fitting
 Chapter 552 Gamma Distribution Fitting Introduction This module fits the gamma probability distributions to a complete or censored set of individual or grouped data values. It outputs various statistics
Chapter 552 Gamma Distribution Fitting Introduction This module fits the gamma probability distributions to a complete or censored set of individual or grouped data values. It outputs various statistics
Financial Mathematics III Theory summary
 Financial Mathematics III Theory summary Table of Contents Lecture 1... 7 1. State the objective of modern portfolio theory... 7 2. Define the return of an asset... 7 3. How is expected return defined?...
Financial Mathematics III Theory summary Table of Contents Lecture 1... 7 1. State the objective of modern portfolio theory... 7 2. Define the return of an asset... 7 3. How is expected return defined?...
On Packing Densities of Set Partitions
 On Packing Densities of Set Partitions Adam M.Goyt 1 Department of Mathematics Minnesota State University Moorhead Moorhead, MN 56563, USA goytadam@mnstate.edu Lara K. Pudwell Department of Mathematics
On Packing Densities of Set Partitions Adam M.Goyt 1 Department of Mathematics Minnesota State University Moorhead Moorhead, MN 56563, USA goytadam@mnstate.edu Lara K. Pudwell Department of Mathematics
Problem 1: Random variables, common distributions and the monopoly price
 Problem 1: Random variables, common distributions and the monopoly price In this problem, we will revise some basic concepts in probability, and use these to better understand the monopoly price (alternatively
Problem 1: Random variables, common distributions and the monopoly price In this problem, we will revise some basic concepts in probability, and use these to better understand the monopoly price (alternatively
Tutorial 4 - Pigouvian Taxes and Pollution Permits II. Corrections
 Johannes Emmerling Natural resources and environmental economics, TSE Tutorial 4 - Pigouvian Taxes and Pollution Permits II Corrections Q 1: Write the environmental agency problem as a constrained minimization
Johannes Emmerling Natural resources and environmental economics, TSE Tutorial 4 - Pigouvian Taxes and Pollution Permits II Corrections Q 1: Write the environmental agency problem as a constrained minimization
Lecture 5. 1 Online Learning. 1.1 Learning Setup (Perspective of Universe) CSCI699: Topics in Learning & Game Theory
 CSCI699: Topics in Learning & Game Theory Lecturer: Shaddin Dughmi Lecture 5 Scribes: Umang Gupta & Anastasia Voloshinov In this lecture, we will give a brief introduction to online learning and then go
CSCI699: Topics in Learning & Game Theory Lecturer: Shaddin Dughmi Lecture 5 Scribes: Umang Gupta & Anastasia Voloshinov In this lecture, we will give a brief introduction to online learning and then go
Effective Cost Allocation for Deterrence of Terrorists
 Effective Cost Allocation for Deterrence of Terrorists Eugene Lee Quan Susan Martonosi, Advisor Francis Su, Reader May, 007 Department of Mathematics Copyright 007 Eugene Lee Quan. The author grants Harvey
Effective Cost Allocation for Deterrence of Terrorists Eugene Lee Quan Susan Martonosi, Advisor Francis Su, Reader May, 007 Department of Mathematics Copyright 007 Eugene Lee Quan. The author grants Harvey
On Existence of Equilibria. Bayesian Allocation-Mechanisms
 On Existence of Equilibria in Bayesian Allocation Mechanisms Northwestern University April 23, 2014 Bayesian Allocation Mechanisms In allocation mechanisms, agents choose messages. The messages determine
On Existence of Equilibria in Bayesian Allocation Mechanisms Northwestern University April 23, 2014 Bayesian Allocation Mechanisms In allocation mechanisms, agents choose messages. The messages determine
Lecture 4. Finite difference and finite element methods
 Finite difference and finite element methods Lecture 4 Outline Black-Scholes equation From expectation to PDE Goal: compute the value of European option with payoff g which is the conditional expectation
Finite difference and finite element methods Lecture 4 Outline Black-Scholes equation From expectation to PDE Goal: compute the value of European option with payoff g which is the conditional expectation
Alternative VaR Models
 Alternative VaR Models Neil Roeth, Senior Risk Developer, TFG Financial Systems. 15 th July 2015 Abstract We describe a variety of VaR models in terms of their key attributes and differences, e.g., parametric
Alternative VaR Models Neil Roeth, Senior Risk Developer, TFG Financial Systems. 15 th July 2015 Abstract We describe a variety of VaR models in terms of their key attributes and differences, e.g., parametric
Web Appendix: Proofs and extensions.
 B eb Appendix: Proofs and extensions. B.1 Proofs of results about block correlated markets. This subsection provides proofs for Propositions A1, A2, A3 and A4, and the proof of Lemma A1. Proof of Proposition
B eb Appendix: Proofs and extensions. B.1 Proofs of results about block correlated markets. This subsection provides proofs for Propositions A1, A2, A3 and A4, and the proof of Lemma A1. Proof of Proposition
Internet Appendix for Cost of Experimentation and the Evolution of Venture Capital
 Internet Appendix for Cost of Experimentation and the Evolution of Venture Capital I. Matching between Entrepreneurs and Investors No Commitment Using backward induction we start with the second period
Internet Appendix for Cost of Experimentation and the Evolution of Venture Capital I. Matching between Entrepreneurs and Investors No Commitment Using backward induction we start with the second period
Price Theory of Two-Sided Markets
 The E. Glen Weyl Department of Economics Princeton University Fundação Getulio Vargas August 3, 2007 Definition of a two-sided market 1 Two groups of consumers 2 Value from connecting (proportional to
The E. Glen Weyl Department of Economics Princeton University Fundação Getulio Vargas August 3, 2007 Definition of a two-sided market 1 Two groups of consumers 2 Value from connecting (proportional to
Case Study: Heavy-Tailed Distribution and Reinsurance Rate-making
 Case Study: Heavy-Tailed Distribution and Reinsurance Rate-making May 30, 2016 The purpose of this case study is to give a brief introduction to a heavy-tailed distribution and its distinct behaviors in
Case Study: Heavy-Tailed Distribution and Reinsurance Rate-making May 30, 2016 The purpose of this case study is to give a brief introduction to a heavy-tailed distribution and its distinct behaviors in
An Algorithm for Distributing Coalitional Value Calculations among Cooperating Agents
 An Algorithm for Distributing Coalitional Value Calculations among Cooperating Agents Talal Rahwan and Nicholas R. Jennings School of Electronics and Computer Science, University of Southampton, Southampton
An Algorithm for Distributing Coalitional Value Calculations among Cooperating Agents Talal Rahwan and Nicholas R. Jennings School of Electronics and Computer Science, University of Southampton, Southampton
Maximizing the Spread of Influence through a Social Network Problem/Motivation: Suppose we want to market a product or promote an idea or behavior in
 Maximizing the Spread of Influence through a Social Network Problem/Motivation: Suppose we want to market a product or promote an idea or behavior in a society. In order to do so, we can target individuals,
Maximizing the Spread of Influence through a Social Network Problem/Motivation: Suppose we want to market a product or promote an idea or behavior in a society. In order to do so, we can target individuals,
The Duration Derby: A Comparison of Duration Based Strategies in Asset Liability Management
 The Duration Derby: A Comparison of Duration Based Strategies in Asset Liability Management H. Zheng Department of Mathematics, Imperial College London SW7 2BZ, UK h.zheng@ic.ac.uk L. C. Thomas School
The Duration Derby: A Comparison of Duration Based Strategies in Asset Liability Management H. Zheng Department of Mathematics, Imperial College London SW7 2BZ, UK h.zheng@ic.ac.uk L. C. Thomas School
March 30, Why do economists (and increasingly, engineers and computer scientists) study auctions?
 March 3, 215 Steven A. Matthews, A Technical Primer on Auction Theory I: Independent Private Values, Northwestern University CMSEMS Discussion Paper No. 196, May, 1995. This paper is posted on the course
March 3, 215 Steven A. Matthews, A Technical Primer on Auction Theory I: Independent Private Values, Northwestern University CMSEMS Discussion Paper No. 196, May, 1995. This paper is posted on the course
Lecture 7: Bayesian approach to MAB - Gittins index
 Advanced Topics in Machine Learning and Algorithmic Game Theory Lecture 7: Bayesian approach to MAB - Gittins index Lecturer: Yishay Mansour Scribe: Mariano Schain 7.1 Introduction In the Bayesian approach
Advanced Topics in Machine Learning and Algorithmic Game Theory Lecture 7: Bayesian approach to MAB - Gittins index Lecturer: Yishay Mansour Scribe: Mariano Schain 7.1 Introduction In the Bayesian approach
Counterparty Risk Modeling for Credit Default Swaps
 Counterparty Risk Modeling for Credit Default Swaps Abhay Subramanian, Avinayan Senthi Velayutham, and Vibhav Bukkapatanam Abstract Standard Credit Default Swap (CDS pricing methods assume that the buyer
Counterparty Risk Modeling for Credit Default Swaps Abhay Subramanian, Avinayan Senthi Velayutham, and Vibhav Bukkapatanam Abstract Standard Credit Default Swap (CDS pricing methods assume that the buyer
Quota bonuses in a principle-agent setting
 Quota bonuses in a principle-agent setting Barna Bakó András Kálecz-Simon October 2, 2012 Abstract Theoretical articles on incentive systems almost excusively focus on linear compensations, while in practice,
Quota bonuses in a principle-agent setting Barna Bakó András Kálecz-Simon October 2, 2012 Abstract Theoretical articles on incentive systems almost excusively focus on linear compensations, while in practice,
Finding optimal arbitrage opportunities using a quantum annealer
 Finding optimal arbitrage opportunities using a quantum annealer White Paper Finding optimal arbitrage opportunities using a quantum annealer Gili Rosenberg Abstract We present two formulations for finding
Finding optimal arbitrage opportunities using a quantum annealer White Paper Finding optimal arbitrage opportunities using a quantum annealer Gili Rosenberg Abstract We present two formulations for finding
A different re-execution speed can help
 A different re-execution speed can help Anne Benoit, Aurélien Cavelan, alentin Le Fèvre, Yves Robert, Hongyang Sun LIP, ENS de Lyon, France PASA orkshop, in conjunction with ICPP 16 August 16, 2016 Anne.Benoit@ens-lyon.fr
A different re-execution speed can help Anne Benoit, Aurélien Cavelan, alentin Le Fèvre, Yves Robert, Hongyang Sun LIP, ENS de Lyon, France PASA orkshop, in conjunction with ICPP 16 August 16, 2016 Anne.Benoit@ens-lyon.fr
Equivalence Tests for One Proportion
 Chapter 110 Equivalence Tests for One Proportion Introduction This module provides power analysis and sample size calculation for equivalence tests in one-sample designs in which the outcome is binary.
Chapter 110 Equivalence Tests for One Proportion Introduction This module provides power analysis and sample size calculation for equivalence tests in one-sample designs in which the outcome is binary.
PORTFOLIO OPTIMIZATION AND EXPECTED SHORTFALL MINIMIZATION FROM HISTORICAL DATA
 PORTFOLIO OPTIMIZATION AND EXPECTED SHORTFALL MINIMIZATION FROM HISTORICAL DATA We begin by describing the problem at hand which motivates our results. Suppose that we have n financial instruments at hand,
PORTFOLIO OPTIMIZATION AND EXPECTED SHORTFALL MINIMIZATION FROM HISTORICAL DATA We begin by describing the problem at hand which motivates our results. Suppose that we have n financial instruments at hand,
Forward Contracts and Generator Market Power: How Externalities Reduce Benefits in Equilibrium
 Forward Contracts and Generator Market Power: How Externalities Reduce Benefits in Equilibrium Ian Schneider, Audun Botterud, and Mardavij Roozbehani November 9, 2017 Abstract Research has shown that forward
Forward Contracts and Generator Market Power: How Externalities Reduce Benefits in Equilibrium Ian Schneider, Audun Botterud, and Mardavij Roozbehani November 9, 2017 Abstract Research has shown that forward
15-451/651: Design & Analysis of Algorithms November 9 & 11, 2015 Lecture #19 & #20 last changed: November 10, 2015
 15-451/651: Design & Analysis of Algorithms November 9 & 11, 2015 Lecture #19 & #20 last changed: November 10, 2015 Last time we looked at algorithms for finding approximately-optimal solutions for NP-hard
15-451/651: Design & Analysis of Algorithms November 9 & 11, 2015 Lecture #19 & #20 last changed: November 10, 2015 Last time we looked at algorithms for finding approximately-optimal solutions for NP-hard
Portfolio Sharpening
 Portfolio Sharpening Patrick Burns 21st September 2003 Abstract We explore the effective gain or loss in alpha from the point of view of the investor due to the volatility of a fund and its correlations
Portfolio Sharpening Patrick Burns 21st September 2003 Abstract We explore the effective gain or loss in alpha from the point of view of the investor due to the volatility of a fund and its correlations
Optimization Prof. A. Goswami Department of Mathematics Indian Institute of Technology, Kharagpur. Lecture - 18 PERT
 Optimization Prof. A. Goswami Department of Mathematics Indian Institute of Technology, Kharagpur Lecture - 18 PERT (Refer Slide Time: 00:56) In the last class we completed the C P M critical path analysis
Optimization Prof. A. Goswami Department of Mathematics Indian Institute of Technology, Kharagpur Lecture - 18 PERT (Refer Slide Time: 00:56) In the last class we completed the C P M critical path analysis
Stock Repurchase with an Adaptive Reservation Price: A Study of the Greedy Policy
 Stock Repurchase with an Adaptive Reservation Price: A Study of the Greedy Policy Ye Lu Asuman Ozdaglar David Simchi-Levi November 8, 200 Abstract. We consider the problem of stock repurchase over a finite
Stock Repurchase with an Adaptive Reservation Price: A Study of the Greedy Policy Ye Lu Asuman Ozdaglar David Simchi-Levi November 8, 200 Abstract. We consider the problem of stock repurchase over a finite
Extraction capacity and the optimal order of extraction. By: Stephen P. Holland
 Extraction capacity and the optimal order of extraction By: Stephen P. Holland Holland, Stephen P. (2003) Extraction Capacity and the Optimal Order of Extraction, Journal of Environmental Economics and
Extraction capacity and the optimal order of extraction By: Stephen P. Holland Holland, Stephen P. (2003) Extraction Capacity and the Optimal Order of Extraction, Journal of Environmental Economics and
A Formal Study of Distributed Resource Allocation Strategies in Multi-Agent Systems
 A Formal Study of Distributed Resource Allocation Strategies in Multi-Agent Systems Jiaying Shen, Micah Adler, Victor Lesser Department of Computer Science University of Massachusetts Amherst, MA 13 Abstract
A Formal Study of Distributed Resource Allocation Strategies in Multi-Agent Systems Jiaying Shen, Micah Adler, Victor Lesser Department of Computer Science University of Massachusetts Amherst, MA 13 Abstract
Arborescent Architecture for Decentralized Supervisory Control of Discrete Event Systems
 Arborescent Architecture for Decentralized Supervisory Control of Discrete Event Systems Ahmed Khoumsi and Hicham Chakib Dept. Electrical & Computer Engineering, University of Sherbrooke, Canada Email:
Arborescent Architecture for Decentralized Supervisory Control of Discrete Event Systems Ahmed Khoumsi and Hicham Chakib Dept. Electrical & Computer Engineering, University of Sherbrooke, Canada Email:
ECON Micro Foundations
 ECON 302 - Micro Foundations Michael Bar September 13, 2016 Contents 1 Consumer s Choice 2 1.1 Preferences.................................... 2 1.2 Budget Constraint................................ 3
ECON 302 - Micro Foundations Michael Bar September 13, 2016 Contents 1 Consumer s Choice 2 1.1 Preferences.................................... 2 1.2 Budget Constraint................................ 3
LECTURE 2: MULTIPERIOD MODELS AND TREES
 LECTURE 2: MULTIPERIOD MODELS AND TREES 1. Introduction One-period models, which were the subject of Lecture 1, are of limited usefulness in the pricing and hedging of derivative securities. In real-world
LECTURE 2: MULTIPERIOD MODELS AND TREES 1. Introduction One-period models, which were the subject of Lecture 1, are of limited usefulness in the pricing and hedging of derivative securities. In real-world
Multi-Armed Bandit, Dynamic Environments and Meta-Bandits
 Multi-Armed Bandit, Dynamic Environments and Meta-Bandits C. Hartland, S. Gelly, N. Baskiotis, O. Teytaud and M. Sebag Lab. of Computer Science CNRS INRIA Université Paris-Sud, Orsay, France Abstract This
Multi-Armed Bandit, Dynamic Environments and Meta-Bandits C. Hartland, S. Gelly, N. Baskiotis, O. Teytaud and M. Sebag Lab. of Computer Science CNRS INRIA Université Paris-Sud, Orsay, France Abstract This
October An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution.
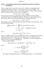 October 13..18.4 An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution. We now assume that the reservation values of the bidders are independently and identically distributed
October 13..18.4 An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution. We now assume that the reservation values of the bidders are independently and identically distributed
Chapter 2 Uncertainty Analysis and Sampling Techniques
 Chapter 2 Uncertainty Analysis and Sampling Techniques The probabilistic or stochastic modeling (Fig. 2.) iterative loop in the stochastic optimization procedure (Fig..4 in Chap. ) involves:. Specifying
Chapter 2 Uncertainty Analysis and Sampling Techniques The probabilistic or stochastic modeling (Fig. 2.) iterative loop in the stochastic optimization procedure (Fig..4 in Chap. ) involves:. Specifying
Antino Kim Kelley School of Business, Indiana University, Bloomington Bloomington, IN 47405, U.S.A.
 THE INVISIBLE HAND OF PIRACY: AN ECONOMIC ANALYSIS OF THE INFORMATION-GOODS SUPPLY CHAIN Antino Kim Kelley School of Business, Indiana University, Bloomington Bloomington, IN 47405, U.S.A. {antino@iu.edu}
THE INVISIBLE HAND OF PIRACY: AN ECONOMIC ANALYSIS OF THE INFORMATION-GOODS SUPPLY CHAIN Antino Kim Kelley School of Business, Indiana University, Bloomington Bloomington, IN 47405, U.S.A. {antino@iu.edu}
Order book resilience, price manipulations, and the positive portfolio problem
 Order book resilience, price manipulations, and the positive portfolio problem Alexander Schied Mannheim University PRisMa Workshop Vienna, September 28, 2009 Joint work with Aurélien Alfonsi and Alla
Order book resilience, price manipulations, and the positive portfolio problem Alexander Schied Mannheim University PRisMa Workshop Vienna, September 28, 2009 Joint work with Aurélien Alfonsi and Alla
Partial privatization as a source of trade gains
 Partial privatization as a source of trade gains Kenji Fujiwara School of Economics, Kwansei Gakuin University April 12, 2008 Abstract A model of mixed oligopoly is constructed in which a Home public firm
Partial privatization as a source of trade gains Kenji Fujiwara School of Economics, Kwansei Gakuin University April 12, 2008 Abstract A model of mixed oligopoly is constructed in which a Home public firm
2 Deduction in Sentential Logic
 2 Deduction in Sentential Logic Though we have not yet introduced any formal notion of deductions (i.e., of derivations or proofs), we can easily give a formal method for showing that formulas are tautologies:
2 Deduction in Sentential Logic Though we have not yet introduced any formal notion of deductions (i.e., of derivations or proofs), we can easily give a formal method for showing that formulas are tautologies:
Impact of Imperfect Information on the Optimal Exercise Strategy for Warrants
 Impact of Imperfect Information on the Optimal Exercise Strategy for Warrants April 2008 Abstract In this paper, we determine the optimal exercise strategy for corporate warrants if investors suffer from
Impact of Imperfect Information on the Optimal Exercise Strategy for Warrants April 2008 Abstract In this paper, we determine the optimal exercise strategy for corporate warrants if investors suffer from
Advanced Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology, Madras
 Advanced Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology, Madras Lecture 21 Successive Shortest Path Problem In this lecture, we continue our discussion
Advanced Operations Research Prof. G. Srinivasan Department of Management Studies Indian Institute of Technology, Madras Lecture 21 Successive Shortest Path Problem In this lecture, we continue our discussion
S atisfactory reliability and cost performance
 Grid Reliability Spare Transformers and More Frequent Replacement Increase Reliability, Decrease Cost Charles D. Feinstein and Peter A. Morris S atisfactory reliability and cost performance of transmission
Grid Reliability Spare Transformers and More Frequent Replacement Increase Reliability, Decrease Cost Charles D. Feinstein and Peter A. Morris S atisfactory reliability and cost performance of transmission
The Fixed Income Valuation Course. Sanjay K. Nawalkha Gloria M. Soto Natalia A. Beliaeva
 Interest Rate Risk Modeling The Fixed Income Valuation Course Sanjay K. Nawalkha Gloria M. Soto Natalia A. Beliaeva Interest t Rate Risk Modeling : The Fixed Income Valuation Course. Sanjay K. Nawalkha,
Interest Rate Risk Modeling The Fixed Income Valuation Course Sanjay K. Nawalkha Gloria M. Soto Natalia A. Beliaeva Interest t Rate Risk Modeling : The Fixed Income Valuation Course. Sanjay K. Nawalkha,
Macro Consumption Problems 33-43
 Macro Consumption Problems 33-43 3rd October 6 Problem 33 This is a very simple example of questions involving what is referred to as "non-convex budget sets". In other words, there is some non-standard
Macro Consumption Problems 33-43 3rd October 6 Problem 33 This is a very simple example of questions involving what is referred to as "non-convex budget sets". In other words, there is some non-standard
d. Find a competitive equilibrium for this economy. Is the allocation Pareto efficient? Are there any other competitive equilibrium allocations?
 Answers to Microeconomics Prelim of August 7, 0. Consider an individual faced with two job choices: she can either accept a position with a fixed annual salary of x > 0 which requires L x units of labor
Answers to Microeconomics Prelim of August 7, 0. Consider an individual faced with two job choices: she can either accept a position with a fixed annual salary of x > 0 which requires L x units of labor
Valuing the Probability. of Generating Negative Interest Rates. under the Vasicek One-Factor Model
 Communications in Mathematical Finance, vol.4, no.2, 2015, 1-47 ISSN: 2241-1968 print), 2241-195X online) Scienpress Ltd, 2015 Valuing the Probability of Generating Negative Interest Rates under the Vasicek
Communications in Mathematical Finance, vol.4, no.2, 2015, 1-47 ISSN: 2241-1968 print), 2241-195X online) Scienpress Ltd, 2015 Valuing the Probability of Generating Negative Interest Rates under the Vasicek
Review for Quiz #2 Revised: October 31, 2015
 ECON-UB 233 Dave Backus @ NYU Review for Quiz #2 Revised: October 31, 2015 I ll focus again on the big picture to give you a sense of what we ve done and how it fits together. For each topic/result/concept,
ECON-UB 233 Dave Backus @ NYU Review for Quiz #2 Revised: October 31, 2015 I ll focus again on the big picture to give you a sense of what we ve done and how it fits together. For each topic/result/concept,
