Lecture l(x) 1. (1) x X
|
|
|
- Millicent Shields
- 6 years ago
- Views:
Transcription
1 Lecture 14 Agenda for the lecture Kraft s inequality Shannon codes The relation H(X) L u (X) = L p (X) H(X) Kraft s inequality While the definition of prefix-free codes is intuitively clear, we still have no handle over their average length. The next result gives a simple and elegant characterization of the lengths of prefix-free codes. Theorem Given a prefix-free code which assigns a codeword of length l(x) to symbol x X, the following bound (known as Kraft s inequality) holds: 2 l(x) 1. (1) Conversely, for every sequence {l(x) N {0}, x X } satisfying Kraft s inequality (1) there exists a prefix-free code which assigns to each symbol x a codeword of length l(x). c Himanshu Tyagi. Feel free to use with acknowledgement. 1
2 Thus, lengths of codewords of a prefix-free code are simply characterized by the relation (1). Before we proceed and prove Theorem 14.1, we note an important consequence of satisfying Kraft s inequality. Lemma Given a pmf P X on X and a code which assigns a codeword of length l(x) to the symbol x X, suppose that l(x), x X, satisfy Kraft s inequality (1). Then, the average length of the code is at least H(X) From the two results above, it follows that every prefix-free code has average length at least H(X); we get the following corollary. Corollary For a pmf P X over a discrete set X, L p (X) H(X). Therefore, prefix-free codes cannot have average length less than H(X). We now prove Theorem 14.1 and Lemma We start with a proof of the lemma Proof of Lemma 14.2 The average length of a code with lengths satisfying Kraft s inequality satisfies l a (C) = P X (x) l(x) = P X (x) log = log 1 2 l(x) P X (x) log P X (x) 2 l(x) + H(X) x H(X), 1 2 l(x) + H(X) where the last bound holds using Kraft s inequality. 2
3 Proof of Theorem 14.1 We provide two different proofs, each based on a different representation of prefix-free codes. Binary-tree representation of prefix-free codes. A binary tree is a convenient pictorial rrepresentation of binary sequences. We first describe a complete binary tree. Starting from a fixed node, the so-called root, we obtain nodes at depth 1 by drawing edges to two nodes below it, one on the left of the root and the second on the right, referred to respectively as the left- and the right-child of the root. The nodes at depth 2 are obtained similarly by treating each node of depth 1 as a root and repeating the process described above. We proceed this way to obtain nodes of depth d. This gives us the complete binary tree of depth d; the nodes which do not have any children, namely the nodes at depth d, are called the leaves of the tree. Clearly, there are 2 d leaves in a complete binary tree. Note that the nodes below a node of depth l in a complete binary tree of depth d themselves form the root of the d l-depth complete binary tree below them; we refer to this tree as a sub-tree of the original tree. In general, a binary tree is obtained by starting with a complete binary tree and removing all the nodes below them; this process will remove 2 d l leaves from the original complete tree when a node at depth l removed. Also, note that there is a one-to-one map from the set of binary sequences of length less than or equal to d and the nodes of a complete binary tree of depth d. Specifically, each node of the tree can be uniquely represented by the path from root to that node, which in turn can be represented as a binary sequence by labeling each edge to the left-child with a 0 and that to a right-child with a 1. Our proof relies on representing the codewords of a prefix-free code on a binary tree using this labeling. The key observation here is that a binary sequence c of length d is a prefix of another binary sequence c of length d if and only if the node corresponding to c in the complete tree representation above lies in the sub-tree with the node corresponding to c as the root. We now prove the theorem. Suppose l 1 l 2... l m denote the sorted lengths of the 3
4 prefix-free code (this proof works when l m < ). We first place this code over a complete binary tree of depth l m using the labeling described above. Next, we prune the tree so formed by removing all the nodes below each node corresponding to a codeword. Since our code is prefix-free, none of the codeword nodes is removed in our procedure. We finally end-up with a binary tree where each codeword is a leaf node. Note that the number of leaf nodes removed corresponding to a codeword of length l i is 2 lm l i. Since there were 2 lm leaves to begin with, we must have m 2 lm l i 2 lm, i=1 which is equivalent to Kraft s inequality. Thus, the codeword lengths for a prefix-free code satisfy Kraft s inequality. For the converse, we just invert the proof above. Given a set of lengths l 1 l 2... l m satisfying kraft s inequality, consider the complete binary tree of depth l m. Our construction proceeds iteratively by identifying the codewords corresponding to l 1,..., l m. At the ith step, we start with a leaf of the original complete binary tree of depth l m and identify a node at depth l i above it, i.e., we move from this leaf to the root and stop when we are at depth l i. We remove the sub-tree with this node as its root. This results in the removal of 2 lm l i leaves of the original tree. Next, we proceed to the next available leaf and repeat the process above. Note that the removed sub-tree at each step does not contain a codeword since otherwise the length of the removed codeword will be greater than the current codeword; this cannot be the case since we have assumed that the lengths are sorted in a nondecreasing order. This process can continue as long as the number of leaves removed till step i is less than the total number of leaves. That is, as long as i 2 lm l j 2 lm. j=1 Since the lengths satisfy Kraft s inequality, the condition above continues to hold for 4
5 1 i m. The desired prefix-free code is given by the binary sequences corresponding to the leaf nodes of the tree so obtained. Interval representation of prefix-free code. Our second proof represents codewords of a prefix-free code by non-intersecting intervals which are subset of [0, 1]. Specifically, given c = (c 1,..., c l ) {0, 1} l, let I c = [0.c 1 c 2...c l, 0.c 1 c 2...c l + 2 l ) where 0.c 1 c 2...c l denotes the corresponding binary number. For example, 0.1 is 1/2, 0.11 is 1/2+1/4, and so on. We first prove that the intervals I c, c C, corresponding to a prefix-free code C are non-intersecting. Therefore, since each interval is in [0, 1], the sum of the lengths of the interval is less than 1, which gives Kraft s inequality. It only remains to prove the non-intersection claim. To that end, note that the interval I c consists of all x [0, 1] starting with 0.c 1...c l since x I c iff 0.c 1...c l x 0.c 1...c l + 2 l = 0.c 1...c l Thus, if x I c I c then x must start with 0.c as well as 0.c, which is a contradiction since the code is prefix free. Conversely, given lengths l 1... l m satisfying Kraft s inequality, we identify codewords c (1),..., c (m) of lengths l 1,..., l m, respectively, such that the corresponding intervals I c i are non-intersecting. By the argument above, such codewords must be prefix-free. The construction is simple. Let c (1) be the all zero sequence of length l 1. For 1 < i m, let x i = i 1 j=1 2 l j. Since the lengths satisfy Kraft s inequality, x i [0, 1] for all 1 < i m. The required codewords are given by binary representations of x i truncated to l i most significant bits. In particular, for 1 < i m, c (i) is sequence of length l i with 1 s at the l 1, l 2,..., l i 1th locations and zero everywhere else. For example, let l 1 = 1, l 2 = 2, l 3 = l 4 = 3. Clearly, these lengths satisfy Kraft s inequality. Then, the required code is given by {0, 10, 110, 111}. Note that here, too, it is necessary to have the lengths in a nondecreasing order. 5
6 14.2 Shannon codes We now show that there exist prefix free code of average length less than H(X) + 1. Note that in view of Theorem 14.1 we only need to exhibit codeword lengths which satisfy Kraft s inequality and the average length is less than H(X) + 1; the code can be constructed using the tree based construction or the interval based construction in the proof of Theorem To that end, we introduce Shannon codes, which actually is a class of codes. Given a source with discrete alphabet X and pmf P X, a prefix-free code is called a Shannon code for P X if the codeword lengths l(x) satisfy l(x) = log P X (x), for each x in X. These lengths satisfy Kraft s inequality since 2 l(x) = 2 log PX(x) 2 log PX(x) = P X (x) = 1. Therefore, by Theorem 14.1 there exists a prefix-free code with these lengths. Furthermore, the average length of such a code is l a (C) = P X (x) l(x) = P X (x) log P X (x) ( log P X (x) + 1) = H(X) + 1. Together with Corollary 14.3, we have shown that for every discrete source with pmf P X H(X) L p H(X) + 1. For an example of a Shannon code, consider a source which takes 4 possible values a, b, c, d with probabilities {1/8, 1/4, 1/2, 1/8}, respectively. For this source, required lengths for a Shannon code are listed in Table 1. We provide two different codes for these lengths: Code 1 is based on the binary tree construction and code 2 on the interval construction. For code 1, we start with a complete binary tree of depth 3; c is placed on the node 0, b on the node 10, a on the node 110 and d on the node 111. Note that it is important to 6
7 first sort the lengths for this process to work. For instance, if we assign a to 000 first and then look for b above the leaf node 001, the process fails. For code 2, once again we proceed in the nondecreasing order of lengths; c is assigned to the interval [0.0, 0.1), b to the interval [0.10, 0.11), a to the interval [0.110, 0.111) and d to the interval [0.111, 1). Note that both the constructions lead to the same code. However, this is due to the order we followed in selected the next available leaf in the tree construction. We selected the available leaf with the least value in binary; a different rule for selecting the next available leaf will lead to different codes. Alphabet P X (x) l(x) code a b c d Table 1: An example of a Shannon code Can we do better with uniquely decodable codes? In the previous lecture, we saw an example of a code which is uniquely decodable but not prefix-free. Thus, the class of uniquely decodable codes is much bigger than the class of prefix-free codes. But can we attain a smaller average length with uniquely decodable codes? The next results shows that lengths of codewords of uniquely decodable codes, too, satisfy Kraft s inequality. Therefore, by Theorem 14.1 there must exist a prefix-free code with these lengths, i.e., for every uniquely decodable code, there exists a prefix-free code which assigns exactly the same length codewords to each symbol. Thus, L u (X) = L p (X), 7
8 and we need not worry about uniquely decodable codes. Theorem Consider a uniquely decodable code for a source with discrete alphabet X. Let l(x) denote the length of the codeword assigned to the symbol x X. Then, 2 l(x) 1. Proof. Denoting by c(x) the codeword associated with the symbol x and by c(x) the concatenated codeword associated with the sequence x = (x 1,..., x k ), we evaluate the quantity k 2 l(c(x)) in two ways. First, noting that l(c(x)) = k i=1 l(x i), we get k 2 l(c(x)) = k i=1 k 2 l(xi) = ( ) k k 2 l(xi) = 2 l(x). i=1 x i X Also, denoting by a m the number of concatenated codewords c(x) of length m, k 2 l(c(x)) = kl max m=0 a m 2 m, where l max denotes the maximum length max x l(x). But since the code is uniquely decodable, the codewords c(x) must be distinct. Thus, a m 2 m and so k 2 l(c(x)) = Combining the bounds above, we get kl max m=0 a m 2 m kl max. ( ) k 2 l(x) kl m ax 8
9 which gives 2 l(x) k 1 k l 1 k max. Since k can chosen arbitrary, we optimize the bound on the right side for k. In fact, the best bound is attained for k. k 1 k = e ln k k e 0 as k, which proves the claim. In this limit, the right-side above goes to 1 since 9
Introduction to Greedy Algorithms: Huffman Codes
 Introduction to Greedy Algorithms: Huffman Codes Yufei Tao ITEE University of Queensland In computer science, one interesting method to design algorithms is to go greedy, namely, keep doing the thing that
Introduction to Greedy Algorithms: Huffman Codes Yufei Tao ITEE University of Queensland In computer science, one interesting method to design algorithms is to go greedy, namely, keep doing the thing that
It is used when neither the TX nor RX knows anything about the statistics of the source sequence at the start of the transmission
 It is used when neither the TX nor RX knows anything about the statistics of the source sequence at the start of the transmission -The code can be described in terms of a binary tree -0 corresponds to
It is used when neither the TX nor RX knows anything about the statistics of the source sequence at the start of the transmission -The code can be described in terms of a binary tree -0 corresponds to
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay
 Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 15 Adaptive Huffman Coding Part I Huffman code are optimal for a
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 15 Adaptive Huffman Coding Part I Huffman code are optimal for a
Structural Induction
 Structural Induction Jason Filippou CMSC250 @ UMCP 07-05-2016 Jason Filippou (CMSC250 @ UMCP) Structural Induction 07-05-2016 1 / 26 Outline 1 Recursively defined structures 2 Proofs Binary Trees Jason
Structural Induction Jason Filippou CMSC250 @ UMCP 07-05-2016 Jason Filippou (CMSC250 @ UMCP) Structural Induction 07-05-2016 1 / 26 Outline 1 Recursively defined structures 2 Proofs Binary Trees Jason
Sublinear Time Algorithms Oct 19, Lecture 1
 0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
0368.416701 Sublinear Time Algorithms Oct 19, 2009 Lecturer: Ronitt Rubinfeld Lecture 1 Scribe: Daniel Shahaf 1 Sublinear-time algorithms: motivation Twenty years ago, there was practically no investigation
Design and Analysis of Algorithms 演算法設計與分析. Lecture 9 November 19, 2014 洪國寶
 Design and Analysis of Algorithms 演算法設計與分析 Lecture 9 November 19, 2014 洪國寶 1 Outline Advanced data structures Binary heaps(review) Binomial heaps Fibonacci heaps Data structures for disjoint sets 2 Mergeable
Design and Analysis of Algorithms 演算法設計與分析 Lecture 9 November 19, 2014 洪國寶 1 Outline Advanced data structures Binary heaps(review) Binomial heaps Fibonacci heaps Data structures for disjoint sets 2 Mergeable
Data Structures. Binomial Heaps Fibonacci Heaps. Haim Kaplan & Uri Zwick December 2013
 Data Structures Binomial Heaps Fibonacci Heaps Haim Kaplan & Uri Zwick December 13 1 Heaps / Priority queues Binary Heaps Binomial Heaps Lazy Binomial Heaps Fibonacci Heaps Insert Find-min Delete-min Decrease-key
Data Structures Binomial Heaps Fibonacci Heaps Haim Kaplan & Uri Zwick December 13 1 Heaps / Priority queues Binary Heaps Binomial Heaps Lazy Binomial Heaps Fibonacci Heaps Insert Find-min Delete-min Decrease-key
Design and Analysis of Algorithms. Lecture 9 November 20, 2013 洪國寶
 Design and Analysis of Algorithms 演算法設計與分析 Lecture 9 November 20, 2013 洪國寶 1 Outline Advanced data structures Binary heaps (review) Binomial heaps Fibonacci heaps Dt Data structures t for disjoint dijitsets
Design and Analysis of Algorithms 演算法設計與分析 Lecture 9 November 20, 2013 洪國寶 1 Outline Advanced data structures Binary heaps (review) Binomial heaps Fibonacci heaps Dt Data structures t for disjoint dijitsets
Essays on Some Combinatorial Optimization Problems with Interval Data
 Essays on Some Combinatorial Optimization Problems with Interval Data a thesis submitted to the department of industrial engineering and the institute of engineering and sciences of bilkent university
Essays on Some Combinatorial Optimization Problems with Interval Data a thesis submitted to the department of industrial engineering and the institute of engineering and sciences of bilkent university
Homework #4. CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class
 Homework #4 CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class o Grades depend on neatness and clarity. o Write your answers with enough detail about your approach and concepts
Homework #4 CMSC351 - Spring 2013 PRINT Name : Due: Thu Apr 16 th at the start of class o Grades depend on neatness and clarity. o Write your answers with enough detail about your approach and concepts
Lecture 5: Tuesday, January 27, Peterson s Algorithm satisfies the No Starvation property (Theorem 1)
 Com S 611 Spring Semester 2015 Advanced Topics on Distributed and Concurrent Algorithms Lecture 5: Tuesday, January 27, 2015 Instructor: Soma Chaudhuri Scribe: Nik Kinkel 1 Introduction This lecture covers
Com S 611 Spring Semester 2015 Advanced Topics on Distributed and Concurrent Algorithms Lecture 5: Tuesday, January 27, 2015 Instructor: Soma Chaudhuri Scribe: Nik Kinkel 1 Introduction This lecture covers
CSE 417 Algorithms. Huffman Codes: An Optimal Data Compression Method
 CSE 417 Algorithms Huffman Codes: An Optimal Data Compression Method 1 Compression Example 100k file, 6 letter alphabet: a 45% b 13% c 12% d 16% e 9% f 5% File Size: ASCII, 8 bits/char: 800kbits 2 3 >
CSE 417 Algorithms Huffman Codes: An Optimal Data Compression Method 1 Compression Example 100k file, 6 letter alphabet: a 45% b 13% c 12% d 16% e 9% f 5% File Size: ASCII, 8 bits/char: 800kbits 2 3 >
A relation on 132-avoiding permutation patterns
 Discrete Mathematics and Theoretical Computer Science DMTCS vol. VOL, 205, 285 302 A relation on 32-avoiding permutation patterns Natalie Aisbett School of Mathematics and Statistics, University of Sydney,
Discrete Mathematics and Theoretical Computer Science DMTCS vol. VOL, 205, 285 302 A relation on 32-avoiding permutation patterns Natalie Aisbett School of Mathematics and Statistics, University of Sydney,
TABLEAU-BASED DECISION PROCEDURES FOR HYBRID LOGIC
 TABLEAU-BASED DECISION PROCEDURES FOR HYBRID LOGIC THOMAS BOLANDER AND TORBEN BRAÜNER Abstract. Hybrid logics are a principled generalization of both modal logics and description logics. It is well-known
TABLEAU-BASED DECISION PROCEDURES FOR HYBRID LOGIC THOMAS BOLANDER AND TORBEN BRAÜNER Abstract. Hybrid logics are a principled generalization of both modal logics and description logics. It is well-known
On the Optimality of a Family of Binary Trees Techical Report TR
 On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
On the Optimality of a Family of Binary Trees Techical Report TR-011101-1 Dana Vrajitoru and William Knight Indiana University South Bend Department of Computer and Information Sciences Abstract In this
The Probabilistic Method - Probabilistic Techniques. Lecture 7: Martingales
 The Probabilistic Method - Probabilistic Techniques Lecture 7: Martingales Sotiris Nikoletseas Associate Professor Computer Engineering and Informatics Department 2015-2016 Sotiris Nikoletseas, Associate
The Probabilistic Method - Probabilistic Techniques Lecture 7: Martingales Sotiris Nikoletseas Associate Professor Computer Engineering and Informatics Department 2015-2016 Sotiris Nikoletseas, Associate
Notes on Natural Logic
 Notes on Natural Logic Notes for PHIL370 Eric Pacuit November 16, 2012 1 Preliminaries: Trees A tree is a structure T = (T, E), where T is a nonempty set whose elements are called nodes and E is a relation
Notes on Natural Logic Notes for PHIL370 Eric Pacuit November 16, 2012 1 Preliminaries: Trees A tree is a structure T = (T, E), where T is a nonempty set whose elements are called nodes and E is a relation
Supporting Information
 Supporting Information Novikoff et al. 0.073/pnas.0986309 SI Text The Recap Method. In The Recap Method in the paper, we described a schedule in terms of a depth-first traversal of a full binary tree,
Supporting Information Novikoff et al. 0.073/pnas.0986309 SI Text The Recap Method. In The Recap Method in the paper, we described a schedule in terms of a depth-first traversal of a full binary tree,
Martingale Pricing Theory in Discrete-Time and Discrete-Space Models
 IEOR E4707: Foundations of Financial Engineering c 206 by Martin Haugh Martingale Pricing Theory in Discrete-Time and Discrete-Space Models These notes develop the theory of martingale pricing in a discrete-time,
IEOR E4707: Foundations of Financial Engineering c 206 by Martin Haugh Martingale Pricing Theory in Discrete-Time and Discrete-Space Models These notes develop the theory of martingale pricing in a discrete-time,
IEOR E4004: Introduction to OR: Deterministic Models
 IEOR E4004: Introduction to OR: Deterministic Models 1 Dynamic Programming Following is a summary of the problems we discussed in class. (We do not include the discussion on the container problem or the
IEOR E4004: Introduction to OR: Deterministic Models 1 Dynamic Programming Following is a summary of the problems we discussed in class. (We do not include the discussion on the container problem or the
SET 1C Binary Trees. 2. (i) Define the height of a binary tree or subtree and also define a height balanced (AVL) tree. (2)
 SET 1C Binary Trees 1. Construct a binary tree whose preorder traversal is K L N M P R Q S T and inorder traversal is N L K P R M S Q T 2. (i) Define the height of a binary tree or subtree and also define
SET 1C Binary Trees 1. Construct a binary tree whose preorder traversal is K L N M P R Q S T and inorder traversal is N L K P R M S Q T 2. (i) Define the height of a binary tree or subtree and also define
MAT25 LECTURE 10 NOTES. = a b. > 0, there exists N N such that if n N, then a n a < ɛ
 MAT5 LECTURE 0 NOTES NATHANIEL GALLUP. Algebraic Limit Theorem Theorem : Algebraic Limit Theorem (Abbott Theorem.3.3) Let (a n ) and ( ) be sequences of real numbers such that lim n a n = a and lim n =
MAT5 LECTURE 0 NOTES NATHANIEL GALLUP. Algebraic Limit Theorem Theorem : Algebraic Limit Theorem (Abbott Theorem.3.3) Let (a n ) and ( ) be sequences of real numbers such that lim n a n = a and lim n =
The Real Numbers. Here we show one way to explicitly construct the real numbers R. First we need a definition.
 The Real Numbers Here we show one way to explicitly construct the real numbers R. First we need a definition. Definitions/Notation: A sequence of rational numbers is a funtion f : N Q. Rather than write
The Real Numbers Here we show one way to explicitly construct the real numbers R. First we need a definition. Definitions/Notation: A sequence of rational numbers is a funtion f : N Q. Rather than write
Online Shopping Intermediaries: The Strategic Design of Search Environments
 Online Supplemental Appendix to Online Shopping Intermediaries: The Strategic Design of Search Environments Anthony Dukes University of Southern California Lin Liu University of Central Florida February
Online Supplemental Appendix to Online Shopping Intermediaries: The Strategic Design of Search Environments Anthony Dukes University of Southern California Lin Liu University of Central Florida February
1 Solutions to Tute09
 s to Tute0 Questions 4. - 4. are straight forward. Q. 4.4 Show that in a binary tree of N nodes, there are N + NULL pointers. Every node has outgoing pointers. Therefore there are N pointers. Each node,
s to Tute0 Questions 4. - 4. are straight forward. Q. 4.4 Show that in a binary tree of N nodes, there are N + NULL pointers. Every node has outgoing pointers. Therefore there are N pointers. Each node,
Optimal Satisficing Tree Searches
 Optimal Satisficing Tree Searches Dan Geiger and Jeffrey A. Barnett Northrop Research and Technology Center One Research Park Palos Verdes, CA 90274 Abstract We provide an algorithm that finds optimal
Optimal Satisficing Tree Searches Dan Geiger and Jeffrey A. Barnett Northrop Research and Technology Center One Research Park Palos Verdes, CA 90274 Abstract We provide an algorithm that finds optimal
CSE 21 Winter 2016 Homework 6 Due: Wednesday, May 11, 2016 at 11:59pm. Instructions
 CSE 1 Winter 016 Homework 6 Due: Wednesday, May 11, 016 at 11:59pm Instructions Homework should be done in groups of one to three people. You are free to change group members at any time throughout the
CSE 1 Winter 016 Homework 6 Due: Wednesday, May 11, 016 at 11:59pm Instructions Homework should be done in groups of one to three people. You are free to change group members at any time throughout the
COS 511: Theoretical Machine Learning. Lecturer: Rob Schapire Lecture #24 Scribe: Jordan Ash May 1, 2014
 COS 5: heoretical Machine Learning Lecturer: Rob Schapire Lecture #24 Scribe: Jordan Ash May, 204 Review of Game heory: Let M be a matrix with all elements in [0, ]. Mindy (called the row player) chooses
COS 5: heoretical Machine Learning Lecturer: Rob Schapire Lecture #24 Scribe: Jordan Ash May, 204 Review of Game heory: Let M be a matrix with all elements in [0, ]. Mindy (called the row player) chooses
Finding Equilibria in Games of No Chance
 Finding Equilibria in Games of No Chance Kristoffer Arnsfelt Hansen, Peter Bro Miltersen, and Troels Bjerre Sørensen Department of Computer Science, University of Aarhus, Denmark {arnsfelt,bromille,trold}@daimi.au.dk
Finding Equilibria in Games of No Chance Kristoffer Arnsfelt Hansen, Peter Bro Miltersen, and Troels Bjerre Sørensen Department of Computer Science, University of Aarhus, Denmark {arnsfelt,bromille,trold}@daimi.au.dk
Yao s Minimax Principle
 Complexity of algorithms The complexity of an algorithm is usually measured with respect to the size of the input, where size may for example refer to the length of a binary word describing the input,
Complexity of algorithms The complexity of an algorithm is usually measured with respect to the size of the input, where size may for example refer to the length of a binary word describing the input,
Feb. 4 Math 2335 sec 001 Spring 2014
 Feb. 4 Math 2335 sec 001 Spring 2014 Propagated Error in Function Evaluation Let f (x) be some differentiable function. Suppose x A is an approximation to x T, and we wish to determine the function value
Feb. 4 Math 2335 sec 001 Spring 2014 Propagated Error in Function Evaluation Let f (x) be some differentiable function. Suppose x A is an approximation to x T, and we wish to determine the function value
2 all subsequent nodes. 252 all subsequent nodes. 401 all subsequent nodes. 398 all subsequent nodes. 330 all subsequent nodes
 ¼ À ÈÌ Ê ½¾ ÈÊÇ Ä ÅË ½µ ½¾º¾¹½ ¾µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º ¹ µ ½¾º ¹ µ ½¾º ¹¾ µ ½¾º ¹ µ ½¾¹¾ ½¼µ ½¾¹ ½ (1) CLR 12.2-1 Based on the structure of the binary tree, and the procedure of Tree-Search, any
¼ À ÈÌ Ê ½¾ ÈÊÇ Ä ÅË ½µ ½¾º¾¹½ ¾µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º¾¹ µ ½¾º ¹ µ ½¾º ¹ µ ½¾º ¹¾ µ ½¾º ¹ µ ½¾¹¾ ½¼µ ½¾¹ ½ (1) CLR 12.2-1 Based on the structure of the binary tree, and the procedure of Tree-Search, any
February 2 Math 2335 sec 51 Spring 2016
 February 2 Math 2335 sec 51 Spring 2016 Section 3.1: Root Finding, Bisection Method Many problems in the sciences, business, manufacturing, etc. can be framed in the form: Given a function f (x), find
February 2 Math 2335 sec 51 Spring 2016 Section 3.1: Root Finding, Bisection Method Many problems in the sciences, business, manufacturing, etc. can be framed in the form: Given a function f (x), find
UNIT VI TREES. Marks - 14
 UNIT VI TREES Marks - 14 SYLLABUS 6.1 Non-linear data structures 6.2 Binary trees : Complete Binary Tree, Basic Terms: level number, degree, in-degree and out-degree, leaf node, directed edge, path, depth,
UNIT VI TREES Marks - 14 SYLLABUS 6.1 Non-linear data structures 6.2 Binary trees : Complete Binary Tree, Basic Terms: level number, degree, in-degree and out-degree, leaf node, directed edge, path, depth,
Q1. [?? pts] Search Traces
![Q1. [?? pts] Search Traces Q1. [?? pts] Search Traces](/thumbs/80/81482567.jpg) CS 188 Spring 2010 Introduction to Artificial Intelligence Midterm Exam Solutions Q1. [?? pts] Search Traces Each of the trees (G1 through G5) was generated by searching the graph (below, left) with a
CS 188 Spring 2010 Introduction to Artificial Intelligence Midterm Exam Solutions Q1. [?? pts] Search Traces Each of the trees (G1 through G5) was generated by searching the graph (below, left) with a
Tug of War Game. William Gasarch and Nick Sovich and Paul Zimand. October 6, Abstract
 Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Tug of War Game William Gasarch and ick Sovich and Paul Zimand October 6, 2009 To be written later Abstract Introduction Combinatorial games under auction play, introduced by Lazarus, Loeb, Propp, Stromquist,
Algorithmic Game Theory and Applications. Lecture 11: Games of Perfect Information
 Algorithmic Game Theory and Applications Lecture 11: Games of Perfect Information Kousha Etessami finite games of perfect information Recall, a perfect information (PI) game has only 1 node per information
Algorithmic Game Theory and Applications Lecture 11: Games of Perfect Information Kousha Etessami finite games of perfect information Recall, a perfect information (PI) game has only 1 node per information
A1: American Options in the Binomial Model
 Appendix 1 A1: American Options in the Binomial Model So far we were dealing with options which can be excercised only at a fixed time, at their maturity date T. These are european options. In a complete
Appendix 1 A1: American Options in the Binomial Model So far we were dealing with options which can be excercised only at a fixed time, at their maturity date T. These are european options. In a complete
Lecture 2: The Simple Story of 2-SAT
 0510-7410: Topics in Algorithms - Random Satisfiability March 04, 2014 Lecture 2: The Simple Story of 2-SAT Lecturer: Benny Applebaum Scribe(s): Mor Baruch 1 Lecture Outline In this talk we will show that
0510-7410: Topics in Algorithms - Random Satisfiability March 04, 2014 Lecture 2: The Simple Story of 2-SAT Lecturer: Benny Applebaum Scribe(s): Mor Baruch 1 Lecture Outline In this talk we will show that
Heaps. Heap/Priority queue. Binomial heaps: Advanced Algorithmics (4AP) Heaps Binary heap. Binomial heap. Jaak Vilo 2009 Spring
 .0.00 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Advanced Algorithmics (4AP) Heaps Jaak Vilo 00 Spring Binary heap http://en.wikipedia.org/wiki/binary_heap Binomial heap http://en.wikipedia.org/wiki/binomial_heap
.0.00 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Advanced Algorithmics (4AP) Heaps Jaak Vilo 00 Spring Binary heap http://en.wikipedia.org/wiki/binary_heap Binomial heap http://en.wikipedia.org/wiki/binomial_heap
Ch 10 Trees. Introduction to Trees. Tree Representations. Binary Tree Nodes. Tree Traversals. Binary Search Trees
 Ch 10 Trees Introduction to Trees Tree Representations Binary Tree Nodes Tree Traversals Binary Search Trees 1 Binary Trees A binary tree is a finite set of elements called nodes. The set is either empty
Ch 10 Trees Introduction to Trees Tree Representations Binary Tree Nodes Tree Traversals Binary Search Trees 1 Binary Trees A binary tree is a finite set of elements called nodes. The set is either empty
6.854J / J Advanced Algorithms Fall 2008
 MIT OpenCourseWare http://ocw.mit.edu 6.854J / 18.415J Advanced Algorithms Fall 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advanced
MIT OpenCourseWare http://ocw.mit.edu 6.854J / 18.415J Advanced Algorithms Fall 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advanced
NOTES ON FIBONACCI TREES AND THEIR OPTIMALITY* YASUICHI HORIBE INTRODUCTION 1. FIBONACCI TREES
 0#0# NOTES ON FIBONACCI TREES AND THEIR OPTIMALITY* YASUICHI HORIBE Shizuoka University, Hamamatsu, 432, Japan (Submitted February 1982) INTRODUCTION Continuing a previous paper [3], some new observations
0#0# NOTES ON FIBONACCI TREES AND THEIR OPTIMALITY* YASUICHI HORIBE Shizuoka University, Hamamatsu, 432, Japan (Submitted February 1982) INTRODUCTION Continuing a previous paper [3], some new observations
Outline of Lecture 1. Martin-Löf tests and martingales
 Outline of Lecture 1 Martin-Löf tests and martingales The Cantor space. Lebesgue measure on Cantor space. Martin-Löf tests. Basic properties of random sequences. Betting games and martingales. Equivalence
Outline of Lecture 1 Martin-Löf tests and martingales The Cantor space. Lebesgue measure on Cantor space. Martin-Löf tests. Basic properties of random sequences. Betting games and martingales. Equivalence
Lecture 7: Bayesian approach to MAB - Gittins index
 Advanced Topics in Machine Learning and Algorithmic Game Theory Lecture 7: Bayesian approach to MAB - Gittins index Lecturer: Yishay Mansour Scribe: Mariano Schain 7.1 Introduction In the Bayesian approach
Advanced Topics in Machine Learning and Algorithmic Game Theory Lecture 7: Bayesian approach to MAB - Gittins index Lecturer: Yishay Mansour Scribe: Mariano Schain 7.1 Introduction In the Bayesian approach
Best response cycles in perfect information games
 P. Jean-Jacques Herings, Arkadi Predtetchinski Best response cycles in perfect information games RM/15/017 Best response cycles in perfect information games P. Jean Jacques Herings and Arkadi Predtetchinski
P. Jean-Jacques Herings, Arkadi Predtetchinski Best response cycles in perfect information games RM/15/017 Best response cycles in perfect information games P. Jean Jacques Herings and Arkadi Predtetchinski
CEC login. Student Details Name SOLUTIONS
 Student Details Name SOLUTIONS CEC login Instructions You have roughly 1 minute per point, so schedule your time accordingly. There is only one correct answer per question. Good luck! Question 1. Searching
Student Details Name SOLUTIONS CEC login Instructions You have roughly 1 minute per point, so schedule your time accordingly. There is only one correct answer per question. Good luck! Question 1. Searching
On Finite Strategy Sets for Finitely Repeated Zero-Sum Games
 On Finite Strategy Sets for Finitely Repeated Zero-Sum Games Thomas C. O Connell Department of Mathematics and Computer Science Skidmore College 815 North Broadway Saratoga Springs, NY 12866 E-mail: oconnellt@acm.org
On Finite Strategy Sets for Finitely Repeated Zero-Sum Games Thomas C. O Connell Department of Mathematics and Computer Science Skidmore College 815 North Broadway Saratoga Springs, NY 12866 E-mail: oconnellt@acm.org
Heaps
 AdvancedAlgorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary_heap
AdvancedAlgorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary_heap
Lecture 6. 1 Polynomial-time algorithms for the global min-cut problem
 ORIE 633 Network Flows September 20, 2007 Lecturer: David P. Williamson Lecture 6 Scribe: Animashree Anandkumar 1 Polynomial-time algorithms for the global min-cut problem 1.1 The global min-cut problem
ORIE 633 Network Flows September 20, 2007 Lecturer: David P. Williamson Lecture 6 Scribe: Animashree Anandkumar 1 Polynomial-time algorithms for the global min-cut problem 1.1 The global min-cut problem
CS 798: Homework Assignment 4 (Game Theory)
 0 5 CS 798: Homework Assignment 4 (Game Theory) 1.0 Preferences Assigned: October 28, 2009 Suppose that you equally like a banana and a lottery that gives you an apple 30% of the time and a carrot 70%
0 5 CS 798: Homework Assignment 4 (Game Theory) 1.0 Preferences Assigned: October 28, 2009 Suppose that you equally like a banana and a lottery that gives you an apple 30% of the time and a carrot 70%
Maximum Contiguous Subsequences
 Chapter 8 Maximum Contiguous Subsequences In this chapter, we consider a well-know problem and apply the algorithm-design techniques that we have learned thus far to this problem. While applying these
Chapter 8 Maximum Contiguous Subsequences In this chapter, we consider a well-know problem and apply the algorithm-design techniques that we have learned thus far to this problem. While applying these
Sy D. Friedman. August 28, 2001
 0 # and Inner Models Sy D. Friedman August 28, 2001 In this paper we examine the cardinal structure of inner models that satisfy GCH but do not contain 0 #. We show, assuming that 0 # exists, that such
0 # and Inner Models Sy D. Friedman August 28, 2001 In this paper we examine the cardinal structure of inner models that satisfy GCH but do not contain 0 #. We show, assuming that 0 # exists, that such
Design and Analysis of Algorithms 演算法設計與分析. Lecture 8 November 16, 2016 洪國寶
 Design and Analysis of Algorithms 演算法設計與分析 Lecture 8 November 6, 206 洪國寶 Outline Review Amortized analysis Advanced data structures Binary heaps Binomial heaps Fibonacci heaps Data structures for disjoint
Design and Analysis of Algorithms 演算法設計與分析 Lecture 8 November 6, 206 洪國寶 Outline Review Amortized analysis Advanced data structures Binary heaps Binomial heaps Fibonacci heaps Data structures for disjoint
A DNC function that computes no effectively bi-immune set
 A DNC function that computes no effectively bi-immune set Achilles A. Beros Laboratoire d Informatique de Nantes Atlantique, Université de Nantes July 5, 204 Standard Definitions Definition f is diagonally
A DNC function that computes no effectively bi-immune set Achilles A. Beros Laboratoire d Informatique de Nantes Atlantique, Université de Nantes July 5, 204 Standard Definitions Definition f is diagonally
Web Appendix: Proofs and extensions.
 B eb Appendix: Proofs and extensions. B.1 Proofs of results about block correlated markets. This subsection provides proofs for Propositions A1, A2, A3 and A4, and the proof of Lemma A1. Proof of Proposition
B eb Appendix: Proofs and extensions. B.1 Proofs of results about block correlated markets. This subsection provides proofs for Propositions A1, A2, A3 and A4, and the proof of Lemma A1. Proof of Proposition
0.1 Equivalence between Natural Deduction and Axiomatic Systems
 0.1 Equivalence between Natural Deduction and Axiomatic Systems Theorem 0.1.1. Γ ND P iff Γ AS P ( ) it is enough to prove that all axioms are theorems in ND, as MP corresponds to ( e). ( ) by induction
0.1 Equivalence between Natural Deduction and Axiomatic Systems Theorem 0.1.1. Γ ND P iff Γ AS P ( ) it is enough to prove that all axioms are theorems in ND, as MP corresponds to ( e). ( ) by induction
AVL Trees. The height of the left subtree can differ from the height of the right subtree by at most 1.
 AVL Trees In order to have a worst case running time for insert and delete operations to be O(log n), we must make it impossible for there to be a very long path in the binary search tree. The first balanced
AVL Trees In order to have a worst case running time for insert and delete operations to be O(log n), we must make it impossible for there to be a very long path in the binary search tree. The first balanced
CHARACTERIZATION OF CLOSED CONVEX SUBSETS OF R n
 CHARACTERIZATION OF CLOSED CONVEX SUBSETS OF R n Chebyshev Sets A subset S of a metric space X is said to be a Chebyshev set if, for every x 2 X; there is a unique point in S that is closest to x: Put
CHARACTERIZATION OF CLOSED CONVEX SUBSETS OF R n Chebyshev Sets A subset S of a metric space X is said to be a Chebyshev set if, for every x 2 X; there is a unique point in S that is closest to x: Put
Smoothed Analysis of Binary Search Trees
 Smoothed Analysis of Binary Search Trees Bodo Manthey and Rüdiger Reischuk Universität zu Lübeck, Institut für Theoretische Informatik Ratzeburger Allee 160, 23538 Lübeck, Germany manthey/reischuk@tcs.uni-luebeck.de
Smoothed Analysis of Binary Search Trees Bodo Manthey and Rüdiger Reischuk Universität zu Lübeck, Institut für Theoretische Informatik Ratzeburger Allee 160, 23538 Lübeck, Germany manthey/reischuk@tcs.uni-luebeck.de
Lecture 14: Basic Fixpoint Theorems (cont.)
 Lecture 14: Basic Fixpoint Theorems (cont) Predicate Transformers Monotonicity and Continuity Existence of Fixpoints Computing Fixpoints Fixpoint Characterization of CTL Operators 1 2 E M Clarke and E
Lecture 14: Basic Fixpoint Theorems (cont) Predicate Transformers Monotonicity and Continuity Existence of Fixpoints Computing Fixpoints Fixpoint Characterization of CTL Operators 1 2 E M Clarke and E
Multirate Multicast Service Provisioning I: An Algorithm for Optimal Price Splitting Along Multicast Trees
 Mathematical Methods of Operations Research manuscript No. (will be inserted by the editor) Multirate Multicast Service Provisioning I: An Algorithm for Optimal Price Splitting Along Multicast Trees Tudor
Mathematical Methods of Operations Research manuscript No. (will be inserted by the editor) Multirate Multicast Service Provisioning I: An Algorithm for Optimal Price Splitting Along Multicast Trees Tudor
The Traveling Salesman Problem. Time Complexity under Nondeterminism. A Nondeterministic Algorithm for tsp (d)
 The Traveling Salesman Problem We are given n cities 1, 2,..., n and integer distances d ij between any two cities i and j. Assume d ij = d ji for convenience. The traveling salesman problem (tsp) asks
The Traveling Salesman Problem We are given n cities 1, 2,..., n and integer distances d ij between any two cities i and j. Assume d ij = d ji for convenience. The traveling salesman problem (tsp) asks
The suffix binary search tree and suffix AVL tree
 Journal of Discrete Algorithms 1 (2003) 387 408 www.elsevier.com/locate/jda The suffix binary search tree and suffix AVL tree Robert W. Irving, Lorna Love Department of Computing Science, University of
Journal of Discrete Algorithms 1 (2003) 387 408 www.elsevier.com/locate/jda The suffix binary search tree and suffix AVL tree Robert W. Irving, Lorna Love Department of Computing Science, University of
The Tree Data Model. Laura Kovács
 The Tree Data Model Laura Kovács Trees (Baumstrukturen) Definition Trees are sets of points, called nodes (Knoten) and lines, called edges (Kanten), connecting two distinct nodes, such that: n 2 n 3 n
The Tree Data Model Laura Kovács Trees (Baumstrukturen) Definition Trees are sets of points, called nodes (Knoten) and lines, called edges (Kanten), connecting two distinct nodes, such that: n 2 n 3 n
Advanced Algorithmics (4AP) Heaps
 Advanced Algorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary
Advanced Algorithmics (4AP) Heaps Jaak Vilo 2009 Spring Jaak Vilo MTAT.03.190 Text Algorithms 1 Heaps http://en.wikipedia.org/wiki/category:heaps_(structure) Binary heap http://en.wikipedia.org/wiki/binary
( ) = R + ª. Similarly, for any set endowed with a preference relation º, we can think of the upper contour set as a correspondance  : defined as
 6 Lecture 6 6.1 Continuity of Correspondances So far we have dealt only with functions. It is going to be useful at a later stage to start thinking about correspondances. A correspondance is just a set-valued
6 Lecture 6 6.1 Continuity of Correspondances So far we have dealt only with functions. It is going to be useful at a later stage to start thinking about correspondances. A correspondance is just a set-valued
Practice Second Midterm Exam II
 CS13 Handout 34 Fall 218 November 2, 218 Practice Second Midterm Exam II This exam is closed-book and closed-computer. You may have a double-sided, 8.5 11 sheet of notes with you when you take this exam.
CS13 Handout 34 Fall 218 November 2, 218 Practice Second Midterm Exam II This exam is closed-book and closed-computer. You may have a double-sided, 8.5 11 sheet of notes with you when you take this exam.
CMPSCI 311: Introduction to Algorithms Second Midterm Practice Exam SOLUTIONS
 CMPSCI 311: Introduction to Algorithms Second Midterm Practice Exam SOLUTIONS November 17, 2016. Name: ID: Instructions: Answer the questions directly on the exam pages. Show all your work for each question.
CMPSCI 311: Introduction to Algorithms Second Midterm Practice Exam SOLUTIONS November 17, 2016. Name: ID: Instructions: Answer the questions directly on the exam pages. Show all your work for each question.
Chapter 16. Binary Search Trees (BSTs)
 Chapter 16 Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types of search trees designed
Chapter 16 Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types of search trees designed
MSU CSE Spring 2011 Exam 2-ANSWERS
 MSU CSE 260-001 Spring 2011 Exam 2-NSWERS Name: This is a closed book exam, with 9 problems on 5 pages totaling 100 points. Integer ivision/ Modulo rithmetic 1. We can add two numbers in base 2 by using
MSU CSE 260-001 Spring 2011 Exam 2-NSWERS Name: This is a closed book exam, with 9 problems on 5 pages totaling 100 points. Integer ivision/ Modulo rithmetic 1. We can add two numbers in base 2 by using
Algorithms and Networking for Computer Games
 Algorithms and Networking for Computer Games Chapter 4: Game Trees http://www.wiley.com/go/smed Game types perfect information games no hidden information two-player, perfect information games Noughts
Algorithms and Networking for Computer Games Chapter 4: Game Trees http://www.wiley.com/go/smed Game types perfect information games no hidden information two-player, perfect information games Noughts
1 Economical Applications
 WEEK 4 Reading [SB], 3.6, pp. 58-69 1 Economical Applications 1.1 Production Function A production function y f(q) assigns to amount q of input the corresponding output y. Usually f is - increasing, that
WEEK 4 Reading [SB], 3.6, pp. 58-69 1 Economical Applications 1.1 Production Function A production function y f(q) assigns to amount q of input the corresponding output y. Usually f is - increasing, that
ECON 459 Game Theory. Lecture Notes Auctions. Luca Anderlini Spring 2017
 ECON 459 Game Theory Lecture Notes Auctions Luca Anderlini Spring 2017 These notes have been used and commented on before. If you can still spot any errors or have any suggestions for improvement, please
ECON 459 Game Theory Lecture Notes Auctions Luca Anderlini Spring 2017 These notes have been used and commented on before. If you can still spot any errors or have any suggestions for improvement, please
c 2004 Society for Industrial and Applied Mathematics
 SIAM J. COMPUT. Vol. 33, No. 5, pp. 1011 1034 c 2004 Society for Industrial and Applied Mathematics EFFICIENT ALGORITHMS FOR OPTIMAL STREAM MERGING FOR MEDIA-ON-DEMAND AMOTZ BAR-NOY AND RICHARD E. LADNER
SIAM J. COMPUT. Vol. 33, No. 5, pp. 1011 1034 c 2004 Society for Industrial and Applied Mathematics EFFICIENT ALGORITHMS FOR OPTIMAL STREAM MERGING FOR MEDIA-ON-DEMAND AMOTZ BAR-NOY AND RICHARD E. LADNER
Lecture 23: April 10
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 23: April 10 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 23: April 10 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Fundamental Algorithms - Surprise Test
 Technische Universität München Fakultät für Informatik Lehrstuhl für Effiziente Algorithmen Dmytro Chibisov Sandeep Sadanandan Winter Semester 007/08 Sheet Model Test January 16, 008 Fundamental Algorithms
Technische Universität München Fakultät für Informatik Lehrstuhl für Effiziente Algorithmen Dmytro Chibisov Sandeep Sadanandan Winter Semester 007/08 Sheet Model Test January 16, 008 Fundamental Algorithms
Chapter 7 One-Dimensional Search Methods
 Chapter 7 One-Dimensional Search Methods An Introduction to Optimization Spring, 2014 1 Wei-Ta Chu Golden Section Search! Determine the minimizer of a function over a closed interval, say. The only assumption
Chapter 7 One-Dimensional Search Methods An Introduction to Optimization Spring, 2014 1 Wei-Ta Chu Golden Section Search! Determine the minimizer of a function over a closed interval, say. The only assumption
Lecture Quantitative Finance Spring Term 2015
 implied Lecture Quantitative Finance Spring Term 2015 : May 7, 2015 1 / 28 implied 1 implied 2 / 28 Motivation and setup implied the goal of this chapter is to treat the implied which requires an algorithm
implied Lecture Quantitative Finance Spring Term 2015 : May 7, 2015 1 / 28 implied 1 implied 2 / 28 Motivation and setup implied the goal of this chapter is to treat the implied which requires an algorithm
0/1 knapsack problem knapsack problem
 1 (1) 0/1 knapsack problem. A thief robbing a safe finds it filled with N types of items of varying size and value, but has only a small knapsack of capacity M to use to carry the goods. More precisely,
1 (1) 0/1 knapsack problem. A thief robbing a safe finds it filled with N types of items of varying size and value, but has only a small knapsack of capacity M to use to carry the goods. More precisely,
Approximate Revenue Maximization with Multiple Items
 Approximate Revenue Maximization with Multiple Items Nir Shabbat - 05305311 December 5, 2012 Introduction The paper I read is called Approximate Revenue Maximization with Multiple Items by Sergiu Hart
Approximate Revenue Maximization with Multiple Items Nir Shabbat - 05305311 December 5, 2012 Introduction The paper I read is called Approximate Revenue Maximization with Multiple Items by Sergiu Hart
The Stackelberg Minimum Spanning Tree Game
 The Stackelberg Minimum Spanning Tree Game J. Cardinal, E. Demaine, S. Fiorini, G. Joret, S. Langerman, I. Newman, O. Weimann, The Stackelberg Minimum Spanning Tree Game, WADS 07 Stackelberg Game 2 players:
The Stackelberg Minimum Spanning Tree Game J. Cardinal, E. Demaine, S. Fiorini, G. Joret, S. Langerman, I. Newman, O. Weimann, The Stackelberg Minimum Spanning Tree Game, WADS 07 Stackelberg Game 2 players:
ECON Micro Foundations
 ECON 302 - Micro Foundations Michael Bar September 13, 2016 Contents 1 Consumer s Choice 2 1.1 Preferences.................................... 2 1.2 Budget Constraint................................ 3
ECON 302 - Micro Foundations Michael Bar September 13, 2016 Contents 1 Consumer s Choice 2 1.1 Preferences.................................... 2 1.2 Budget Constraint................................ 3
Collinear Triple Hypergraphs and the Finite Plane Kakeya Problem
 Collinear Triple Hypergraphs and the Finite Plane Kakeya Problem Joshua Cooper August 14, 006 Abstract We show that the problem of counting collinear points in a permutation (previously considered by the
Collinear Triple Hypergraphs and the Finite Plane Kakeya Problem Joshua Cooper August 14, 006 Abstract We show that the problem of counting collinear points in a permutation (previously considered by the
GAME THEORY. Department of Economics, MIT, Follow Muhamet s slides. We need the following result for future reference.
 14.126 GAME THEORY MIHAI MANEA Department of Economics, MIT, 1. Existence and Continuity of Nash Equilibria Follow Muhamet s slides. We need the following result for future reference. Theorem 1. Suppose
14.126 GAME THEORY MIHAI MANEA Department of Economics, MIT, 1. Existence and Continuity of Nash Equilibria Follow Muhamet s slides. We need the following result for future reference. Theorem 1. Suppose
An effective perfect-set theorem
 An effective perfect-set theorem David Belanger, joint with Keng Meng (Selwyn) Ng CTFM 2016 at Waseda University, Tokyo Institute for Mathematical Sciences National University of Singapore The perfect
An effective perfect-set theorem David Belanger, joint with Keng Meng (Selwyn) Ng CTFM 2016 at Waseda University, Tokyo Institute for Mathematical Sciences National University of Singapore The perfect
Crash-tolerant Consensus in Directed Graph Revisited
 Crash-tolerant Consensus in Directed Graph Revisited Ashish Choudhury Gayathri Garimella Arpita Patra Divya Ravi Pratik Sarkar Abstract Fault-tolerant distributed consensus is a fundamental problem in
Crash-tolerant Consensus in Directed Graph Revisited Ashish Choudhury Gayathri Garimella Arpita Patra Divya Ravi Pratik Sarkar Abstract Fault-tolerant distributed consensus is a fundamental problem in
Single Machine Inserted Idle Time Scheduling with Release Times and Due Dates
 Single Machine Inserted Idle Time Scheduling with Release Times and Due Dates Natalia Grigoreva Department of Mathematics and Mechanics, St.Petersburg State University, Russia n.s.grig@gmail.com Abstract.
Single Machine Inserted Idle Time Scheduling with Release Times and Due Dates Natalia Grigoreva Department of Mathematics and Mechanics, St.Petersburg State University, Russia n.s.grig@gmail.com Abstract.
THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE
 THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE GÜNTER ROTE Abstract. A salesperson wants to visit each of n objects that move on a line at given constant speeds in the shortest possible time,
THE TRAVELING SALESMAN PROBLEM FOR MOVING POINTS ON A LINE GÜNTER ROTE Abstract. A salesperson wants to visit each of n objects that move on a line at given constant speeds in the shortest possible time,
Principles of Program Analysis: Algorithms
 Principles of Program Analysis: Algorithms Transparencies based on Chapter 6 of the book: Flemming Nielson, Hanne Riis Nielson and Chris Hankin: Principles of Program Analysis. Springer Verlag 2005. c
Principles of Program Analysis: Algorithms Transparencies based on Chapter 6 of the book: Flemming Nielson, Hanne Riis Nielson and Chris Hankin: Principles of Program Analysis. Springer Verlag 2005. c
Up till now, we ve mostly been analyzing auctions under the following assumptions:
 Econ 805 Advanced Micro Theory I Dan Quint Fall 2007 Lecture 7 Sept 27 2007 Tuesday: Amit Gandhi on empirical auction stuff p till now, we ve mostly been analyzing auctions under the following assumptions:
Econ 805 Advanced Micro Theory I Dan Quint Fall 2007 Lecture 7 Sept 27 2007 Tuesday: Amit Gandhi on empirical auction stuff p till now, we ve mostly been analyzing auctions under the following assumptions:
4 Martingales in Discrete-Time
 4 Martingales in Discrete-Time Suppose that (Ω, F, P is a probability space. Definition 4.1. A sequence F = {F n, n = 0, 1,...} is called a filtration if each F n is a sub-σ-algebra of F, and F n F n+1
4 Martingales in Discrete-Time Suppose that (Ω, F, P is a probability space. Definition 4.1. A sequence F = {F n, n = 0, 1,...} is called a filtration if each F n is a sub-σ-algebra of F, and F n F n+1
LECTURE 2: MULTIPERIOD MODELS AND TREES
 LECTURE 2: MULTIPERIOD MODELS AND TREES 1. Introduction One-period models, which were the subject of Lecture 1, are of limited usefulness in the pricing and hedging of derivative securities. In real-world
LECTURE 2: MULTIPERIOD MODELS AND TREES 1. Introduction One-period models, which were the subject of Lecture 1, are of limited usefulness in the pricing and hedging of derivative securities. In real-world
Online Algorithms SS 2013
 Faculty of Computer Science, Electrical Engineering and Mathematics Algorithms and Complexity research group Jun.-Prof. Dr. Alexander Skopalik Online Algorithms SS 2013 Summary of the lecture by Vanessa
Faculty of Computer Science, Electrical Engineering and Mathematics Algorithms and Complexity research group Jun.-Prof. Dr. Alexander Skopalik Online Algorithms SS 2013 Summary of the lecture by Vanessa
October An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution.
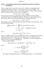 October 13..18.4 An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution. We now assume that the reservation values of the bidders are independently and identically distributed
October 13..18.4 An Equilibrium of the First Price Sealed Bid Auction for an Arbitrary Distribution. We now assume that the reservation values of the bidders are independently and identically distributed
CS134: Networks Spring Random Variables and Independence. 1.2 Probability Distribution Function (PDF) Number of heads Probability 2 0.
 CS134: Networks Spring 2017 Prof. Yaron Singer Section 0 1 Probability 1.1 Random Variables and Independence A real-valued random variable is a variable that can take each of a set of possible values in
CS134: Networks Spring 2017 Prof. Yaron Singer Section 0 1 Probability 1.1 Random Variables and Independence A real-valued random variable is a variable that can take each of a set of possible values in
Lecture 17: More on Markov Decision Processes. Reinforcement learning
 Lecture 17: More on Markov Decision Processes. Reinforcement learning Learning a model: maximum likelihood Learning a value function directly Monte Carlo Temporal-difference (TD) learning COMP-424, Lecture
Lecture 17: More on Markov Decision Processes. Reinforcement learning Learning a model: maximum likelihood Learning a value function directly Monte Carlo Temporal-difference (TD) learning COMP-424, Lecture
COS 445 Final. Due online Monday, May 21st at 11:59 pm. Please upload each problem as a separate file via MTA.
 COS 445 Final Due online Monday, May 21st at 11:59 pm All problems on this final are no collaboration problems. You may not discuss any aspect of any problems with anyone except for the course staff. You
COS 445 Final Due online Monday, May 21st at 11:59 pm All problems on this final are no collaboration problems. You may not discuss any aspect of any problems with anyone except for the course staff. You
Online Appendix for "Optimal Liability when Consumers Mispredict Product Usage" by Andrzej Baniak and Peter Grajzl Appendix B
 Online Appendix for "Optimal Liability when Consumers Mispredict Product Usage" by Andrzej Baniak and Peter Grajzl Appendix B In this appendix, we first characterize the negligence regime when the due
Online Appendix for "Optimal Liability when Consumers Mispredict Product Usage" by Andrzej Baniak and Peter Grajzl Appendix B In this appendix, we first characterize the negligence regime when the due
Successor. CS 361, Lecture 19. Tree-Successor. Outline
 Successor CS 361, Lecture 19 Jared Saia University of New Mexico The successor of a node x is the node that comes after x in the sorted order determined by an in-order tree walk. If all keys are distinct,
Successor CS 361, Lecture 19 Jared Saia University of New Mexico The successor of a node x is the node that comes after x in the sorted order determined by an in-order tree walk. If all keys are distinct,
