ENTERPRISE RISK MANAGEMENT Mumbai 10 Aug 2018
|
|
|
- Felicia Lamb
- 5 years ago
- Views:
Transcription
1 ENTERPRISE RISK MANAGEMENT Mumbai 10 Aug 2018 TOPIC : Information & Cyber Security Risk Pawan Chawla CIO & Partner
2 About Lucideus Incubated out of IIT Bombay, we are a pure play cyber security platforms company We provide IT risk assessment services and platforms to corporates and governments across the globe Some names in our client list include Future Generali, HSBC, Visa, ICICI Bank, SoftBank, BlackRock, Coca Cola, KFC, Indigo, Mckinsey among others We were responsible for the end-to-end cyber security assessment of the BHIM Payments Application recently launched by the Prime Minister of India We recently won the Emerging Cyber Security Vendor of the year presented by Frost and Sullivan In 2016 we were awarded the Best IT Startup of India by the Government of India
3 Cyber War You may not be interested in war, but war is interested in you - Leon Trotsky
4 Information Risk How easy is to get someone s details? Watch to understand how your data can be manipulated - Link What a company can go through because of Social Engineering - Link
5 Cyber Security & Risk Cyber Security Cyber Risk Risk Assessment For an Organization Cyber risk a growing nightmare?
6 Cyber Risk 65% of companies that reported sharing customer data with a partner also reported subsequent breach through that partner
7 Role of a CISO Strategic Advisor Chair Information Security Committee (ISC) Represent Information Security at Board Level Interface with Regulators and other Compliance Regimes Information Security Architecture and Design Manage Security Services Deliver Information Security Projects
8 Current Cyber Risk Underwriting Scenario Underwriting for cybersecurity is currently based on either of the following: External Cybersecurity Score which is not considering the security requirements of the company is not factoring in the internal changes within the company and is based on incomplete information Questionnaire Based Assessment which Suffers from information asymmetry due to differing outlooks towards a company s cybersecurity postures Compromises the completeness of information to save time
9 Why is Cyber Risk Transfer Important? Likelihood is not low enough to ignore & the impact is to massive to handle Cyber Risk is not included in current ERMs Shareholders and Customers are being kept in the dark Balance Sheets and Market Caps are not Protected
10 Challenges in Cyber Risk Transfer Damage Valuation is highly unpredictable before and after the breach Unwillingness to report breaches in fears of escalations Threat and Breach data is unavailable and non-standardized Inability to accurately estimate the likelihood of breach
11 Case Studies Target Corporation experienced a data breach in 2013, which exposed the personal information of more than 100 million customers Impact of Breach - $291 million Covered by Insurance - $100 million with $10 million deductible Bad Decisions - Improper Business Impact Analysis prior to insurance offering After sonypictures.com was breached in 2011, which resulted in 37,000 people having PII exposed, Sony Pictures made a claim of $1.6 million with Hiscox, their cyber insurance carrier at the time Impact of Breach - $15 million Covered by Insurance - Nil Bad Decisions - Improper Policy Coverage
12 Case Studies In June 2014, hackers obtained and posted on the internet approximately 60,000 credit card numbers belonging to P.F. Chang s customers. Impact of Attack - $3.6 million Covered by Insurance - $1.7 million Bad Decisions - Certain exclusions in the insurance policy that barred coverage for MasterCard s fees and assessments Hackers used phishing s to break into a Virginia bank in two separate cyber intrusions. The bank had 2 types of coverage - computer and electronic crime that had a single loss limit liability of $8 million and debit card which had a single loss limit liability of $50,000 Impact of Attack - $2.4 million Covered by Insurance - $50,000 for both intrusions Bad Decisions - Exclusions in the insurance policy that gave limited coverage for debit card breaches
13 Key desirable attributes proposed by World Economic Forum for Cyber Risk Model Applicability: Ability to apply the model across different industries and adjust it depending on the needs of the company Precision: Comprehensiveness and measurement accuracy and precision of the model Timeliness: Ability to timely reflect the environment around the incidents Scope: Ability to cover a wide range of factors and risks Decision-making process: Potential to serve as an effective risk measurement tool for executives and decision-makers *Reference: WEF (in collaboration with Deloitte); Partnering for Cyber Resilience Towards the Quantification of Cyber Threats(2015)
14 Cyber Risk Measurement for Security of Enterprises #SAFEScore The Average Cost Of A Data Breach was $3.62 Million In 2017* *SOURCE: IBM SECURITY REPORT 2017
15 How SAFE works
16 Technology Stack Buildup
17 Properties / Attributes of SAFE Score Real-Time Automated assessments gives near real time scoring for dynamic factors Up To Date coverage of threat landscape Updated with latest threat feeds and control libraries from global industry standards Risk Quantification It quantifies and helps in measuring the cyber security risk posture of an organization Cognitive Security Backed by AI / ML 100% Tech stack coverage Covers 100% assets Covers Internal & External risk Prelude to Insurance It monitors the risk across the policy period
18 SAFE Score to drive Cyber Risk Transfer Better Breach Likelihood predictions Moral Hazard addressed with Real Time Assessment Control Claims from Pandemic Breaches with fast feedback engine Adverse Selection answered by Complete Information Coverage of a Long List of Breaches and Adverse Events Model that Learns and Improves with every claim data Monitors Efforts and Outputs in Cyber Security
19 Adverse impact of a Breach An Adverse Event is an event that an adversary can create against a company resulting in a loss to the Company. 1. Productivity Loss 2. Reputation Loss 3. Competitive Advantage Loss 4. Response Cost 5. Replacement Cost 6. Fines & Jurisdiction Cost Damage factors that require Insurance Cover
20 Challenges related to Adverse Events Likelihood of an adverse event is too volatile and too uncertain for prediction Damage value is unpredictable for calculating limit of liability as well as claims
21 Risk Assessment enabled by SAFE and Lucideus
22 Cyber Risk Assessment 4 Business Impact Analysis Business Impact Analysis is done to get minimum, maximum, and mode of the impact of different incidents in various loss factors Lucideus provides the prediction of likelihood of the individual Incidents if the company maintains one of the given SAFE standards 3
23 Policy Selection & SAFE Installation 6 7
24 Process for Claims
25 Response by SAFE
26 Uncertainty in the likelihood of Adverse Events Prediction of the likelihood of an adverse event is the key challenge in cyber security underwriting vs Answer uncertainty through SAFE Score
27 Likelihood of an Adverse Event through SAFE Score Bayes Theorem yields Where A is the event that an adverse event happens to a company with given data within a year and S is the event that the SAFE score lies in a given range.
28 Prediction of the Likelihood of Adverse Event vs with or without complete cyber resilience information Likelihood of an adverse event with no consideration to the security status of a company is just too volatile and uncertain. SAFE scores depends on complete cybersecurity information about a company s cyber defense Prediction of likelihood of an adverse event becomes highly accurate with SAFE Score
29 SAFE Score Standard for Cyber Risk Transfer Breach likelihood for companies, with high SAFE score, drops down drastically providing ideal conditions for cyber risk transfer SAFE score is designed to be proportional to the cyber defense of a company. Hence, for the upper range of SAFE score the above factor is going to be extremely low.
30 Objective Maximize utility/satisfaction level by optimizing budget Expected Utility Expected Utility at No Loss State Expected Utility at Loss State Likelihood of No Loss Utility at No Loss Likelihood of Loss Utility at Loss Utility at No Loss given IT Budget - Premium - Cost of SAFE Subscription - Cost of Maintaining SAFE Standard Utility at Loss given IT Budget - Premium - Cost of SAFE Subscription - Cost of Maintaining SAFE Standard - Loss + Cover from Claim
31 Budget Constraint Graph Wealth at Loss Constraint Line with SAFE IT Budget - Premium - Loss + Claim + Cost(SAFE) - Cost(SAFE Standard) IT Budget - Premium - Loss + Claim IT Budget - Loss Constraint Line without SAFE Certainty of Wealth i.e., Wealth at Loss = Wealth at No Loss c b a IT Budget - Premium - Cost(SAFE) - Cost(SAFE Standard) IT Budget - Premium IT Budget Wealth at No Loss
32 Objective of an Organization Risk Pooling It is the result of insuring lots of individual people or businesses and expecting that most losses will result in only having to pay claims to some of the insured. Risk Spreading The risk is spread among many insurers or syndicates so that each holder has a sufficiently small stake in any possible outcome. Maximize Profit = Earned Premium + Investment Income Claim Underwriting Expenses
33 Adverse Selection addressed by SAFE Problem: Insurer s Lack of visibility about insured s risk type Insured has better visibility about their risk type than the insurer and are resistant to share complete information with the insurer. Solution: SAFE Score SAFE score reduces the asymmetric information about the insured risk by producing a score for the insured. Also, it helps to understand the probability (π) of the risk involved.
34 Moral hazard addressed by SAFE Problem : Moral Hazard in IT industry Most companies in the IT industry tend to show little incentive to prevent any cyber attack, and on top of that if they get insurance with full cover against any loss due to this phenomena their incentive will only decrease Solution: SAFE Score SAFE score is a real-time measure of the cybersecurity. This property helps insurer to monitor the effort of any firm in maintaining a specific SAFE score throughout the insurance/policy period. Thereby, preventing itself from any loss due to the moral hazard problem.
35 Improving accuracy of SAFE Model using Machine Learning SAFE has the ability of self improvement with observations. SAFE is built on a machine learning principal where it is able to improve itself with the help of a collection of breach data so as to be able to reflect the breaches more appropriately in the later versions. Thus, the claim data can be re-utilized in SAFE which will further enhance its capability of handling Pandemic Breach situations.
36
Cybersecurity Insurance: The Catalyst We've Been Waiting For
 SESSION ID: CRWD-W16 Cybersecurity Insurance: The Catalyst We've Been Waiting For Mark Weatherford Chief Cybersecurity Strategist varmour @marktw Agenda Insurance challenges in the market today 10 reasons
SESSION ID: CRWD-W16 Cybersecurity Insurance: The Catalyst We've Been Waiting For Mark Weatherford Chief Cybersecurity Strategist varmour @marktw Agenda Insurance challenges in the market today 10 reasons
Cyber Risk Quantification: Translating technical risks into business terms
 Cyber Risk Quantification: Translating technical risks into business terms Jesper Sachmann RSA Denmark 13-06-2018 1 CYBER RISK QUANTIFICATION: TRANSLATING TECHNICAL RISKS INTO BUSINESS TERMS Jesper Sachmann
Cyber Risk Quantification: Translating technical risks into business terms Jesper Sachmann RSA Denmark 13-06-2018 1 CYBER RISK QUANTIFICATION: TRANSLATING TECHNICAL RISKS INTO BUSINESS TERMS Jesper Sachmann
OECD Expert Workshop, May 13, Cyber Risk and Cyber Risk Insurance: What do we know? What can we measure? Martin Eling
 OECD Expert Workshop, May 13, 2017 Cyber Risk and Cyber Risk Insurance: What do we know? What can we measure? Martin Eling Management Summary Research Approach: Overview of the main research topics in
OECD Expert Workshop, May 13, 2017 Cyber Risk and Cyber Risk Insurance: What do we know? What can we measure? Martin Eling Management Summary Research Approach: Overview of the main research topics in
Cybersecurity Insurance: New Risks and New Challenges
 SESSION ID: SDS1-F01 Cybersecurity Insurance: New Risks and New Challenges Mark Weatherford Chief Cybersecurity Strategist varmour @marktw The cybersecurity market in the Asia Pacific region contributes
SESSION ID: SDS1-F01 Cybersecurity Insurance: New Risks and New Challenges Mark Weatherford Chief Cybersecurity Strategist varmour @marktw The cybersecurity market in the Asia Pacific region contributes
Solving Cyber Risk. Security Metrics and Insurance. Jason Christopher March 2017
 Solving Cyber Risk Security Metrics and Insurance Jason Christopher March 2017 How We Try to Address Cyber Risk What is Cyber Risk? Definitions Who should be concerned? Key categories of cyber risk Cyber
Solving Cyber Risk Security Metrics and Insurance Jason Christopher March 2017 How We Try to Address Cyber Risk What is Cyber Risk? Definitions Who should be concerned? Key categories of cyber risk Cyber
CyberMatics SM FAQs. General Questions
 CyberMatics SM FAQs General Questions What is CyberMatics? Like telematics for auto insurance, CyberMatics is a technology-driven process to help clients understand their current cyber risk as seen by
CyberMatics SM FAQs General Questions What is CyberMatics? Like telematics for auto insurance, CyberMatics is a technology-driven process to help clients understand their current cyber risk as seen by
The working roundtable was conducted through two interdisciplinary panel sessions:
 As advancements in technology enhance productivity, develop new businesses and enhance economic growth, malicious actors continue to advance as well, seeking to exploit technology for any number of criminal
As advancements in technology enhance productivity, develop new businesses and enhance economic growth, malicious actors continue to advance as well, seeking to exploit technology for any number of criminal
Cyber Risk Management
 Cyber Risk Management Privacy & Data Protection Agenda 2 Introductions Risk Management 101 Defining & Quantifying a Breach Prevention, Mitigation & Transfer Strategies Finance Strategy- Cyber Insurance
Cyber Risk Management Privacy & Data Protection Agenda 2 Introductions Risk Management 101 Defining & Quantifying a Breach Prevention, Mitigation & Transfer Strategies Finance Strategy- Cyber Insurance
Cyber Security Liability:
 www.mcgrathinsurance.com Cyber Security Liability: How to protect your business from a cyber security threat or breach. 01001101011000110100011101110010011000010111010001101000001000000100100101101110011100110111
www.mcgrathinsurance.com Cyber Security Liability: How to protect your business from a cyber security threat or breach. 01001101011000110100011101110010011000010111010001101000001000000100100101101110011100110111
Surprisingly, only 40 percent of small and medium-sized enterprises (SMEs) believe their
 When It Comes to Data Breaches, Why Are Corporations Largely Uninsured? Under Attack and Unprepared: Argo Group Cyber Insurance Survey 2017 Surprisingly, only 40 percent of small and medium-sized enterprises
When It Comes to Data Breaches, Why Are Corporations Largely Uninsured? Under Attack and Unprepared: Argo Group Cyber Insurance Survey 2017 Surprisingly, only 40 percent of small and medium-sized enterprises
CYBER LIABILITY REINSURANCE SOLUTIONS
 CYBER LIABILITY REINSURANCE SOLUTIONS CYBER STRONG. CYBER STRONG. State-of-the-Art Protection for Growing Cyber Risks Businesses of all sizes and in every industry are experiencing an increase in cyber
CYBER LIABILITY REINSURANCE SOLUTIONS CYBER STRONG. CYBER STRONG. State-of-the-Art Protection for Growing Cyber Risks Businesses of all sizes and in every industry are experiencing an increase in cyber
Cyber Incident Response When You Didn t Have a Plan
 Cyber Incident Response When You Didn t Have a Plan April F. Doss Saul Ewing LLP How serious is the cybersecurity threat? Some sobering numbers from 2015: Over half a billion personal records were stolen
Cyber Incident Response When You Didn t Have a Plan April F. Doss Saul Ewing LLP How serious is the cybersecurity threat? Some sobering numbers from 2015: Over half a billion personal records were stolen
No More Snake Oil: Why InfoSec Needs Security Guarantees
 SESSION ID: GRC-T07 No More Snake Oil: Why InfoSec Needs Security Guarantees Jeremiah Grossman Founder WhiteHat Security, Inc. @jeremiahg Ever notice how everything in the Information Security industry
SESSION ID: GRC-T07 No More Snake Oil: Why InfoSec Needs Security Guarantees Jeremiah Grossman Founder WhiteHat Security, Inc. @jeremiahg Ever notice how everything in the Information Security industry
The Proactive Quality Guide to. Embracing Risk
 The Proactive Quality Guide to Embracing Risk Today s Business Uncertainties Are Driving Risk Beyond the Control of Every Business. Best Practice in Risk Management Can Mitigate these Threats The Proactive
The Proactive Quality Guide to Embracing Risk Today s Business Uncertainties Are Driving Risk Beyond the Control of Every Business. Best Practice in Risk Management Can Mitigate these Threats The Proactive
Gov't Must Integrate Insurance With Cybersecurity
 Portfolio Media. Inc. 860 Broadway, 6th Floor New York, NY 10003 www.law360.com Phone: +1 646 783 7100 Fax: +1 646 783 7161 customerservice@law360.com Gov't Must Integrate Insurance With Cybersecurity
Portfolio Media. Inc. 860 Broadway, 6th Floor New York, NY 10003 www.law360.com Phone: +1 646 783 7100 Fax: +1 646 783 7161 customerservice@law360.com Gov't Must Integrate Insurance With Cybersecurity
Vaco Cyber Security Panel
 Vaco Cyber Security Panel ISACA Charlotte Chapter December 5 th, 2017 Vaco is an international talent solutions firm headquartered in Nashville, Tennessee, with more than 35 locations around the globe.
Vaco Cyber Security Panel ISACA Charlotte Chapter December 5 th, 2017 Vaco is an international talent solutions firm headquartered in Nashville, Tennessee, with more than 35 locations around the globe.
HDFC Bank Recommendation: Buy
 1 Prepared by: Mark Wood cdwood@smu.edu HDFC Bank Recommendation: Buy Key Highlights: HDFC Bank has unique positioning within the Indian economy against its competitors India s growing middle class allows
1 Prepared by: Mark Wood cdwood@smu.edu HDFC Bank Recommendation: Buy Key Highlights: HDFC Bank has unique positioning within the Indian economy against its competitors India s growing middle class allows
Business Continuity Management and ERM
 Business Continuity Management and ERM Partnership for Emergency Planning Kansas City Marshall Toburen GRC Strategist ERM, ORM, 3PM RSA A division of EMC 2 June 18, 2014 1 Agenda Intro State of ERM Today
Business Continuity Management and ERM Partnership for Emergency Planning Kansas City Marshall Toburen GRC Strategist ERM, ORM, 3PM RSA A division of EMC 2 June 18, 2014 1 Agenda Intro State of ERM Today
You ve been hacked. Riekie Gordon & Roger Truebody & Alexandra Schudel. Actuarial Society 2017 Convention October 2017
 You ve been hacked Riekie Gordon & Roger Truebody & Alexandra Schudel Why should you care? U$4.6 - U$121 billion - Lloyds U$45 billion not covered 2 The plot thickens 2016 Barkly Survey: It s a business
You ve been hacked Riekie Gordon & Roger Truebody & Alexandra Schudel Why should you care? U$4.6 - U$121 billion - Lloyds U$45 billion not covered 2 The plot thickens 2016 Barkly Survey: It s a business
Aligning Risk Management with CU Business Strategy
 Aligning Risk Management with CU Business Strategy Managing your most pressing risks CUNA Mutual Group Proprietary Reproduction, Adaptation or Distribution Prohibited 2016 CUNA Mutual Group, All Rights
Aligning Risk Management with CU Business Strategy Managing your most pressing risks CUNA Mutual Group Proprietary Reproduction, Adaptation or Distribution Prohibited 2016 CUNA Mutual Group, All Rights
Trends, Vendor Management, and Practical Tips For In House Counsel. ACC National Capital Region October 16, 2018
 Cyberinsurance Issues Coming for 2019 Trends, Vendor Management, and Practical Tips For In House Counsel ACC National Capital Region October 16, 2018 Scott N. Godes Partner Insurance Recovery Co-Chair,
Cyberinsurance Issues Coming for 2019 Trends, Vendor Management, and Practical Tips For In House Counsel ACC National Capital Region October 16, 2018 Scott N. Godes Partner Insurance Recovery Co-Chair,
Customers providing benefit to banks through usage of ATM and EDC machines. Ashish Das 1
 Customers providing benefit to banks through usage of ATM and EDC machines Ashish Das 1 Department of Mathematics, Indian Institute of Technology Bombay, Mumbai-400076, India and Department of Statistics,
Customers providing benefit to banks through usage of ATM and EDC machines Ashish Das 1 Department of Mathematics, Indian Institute of Technology Bombay, Mumbai-400076, India and Department of Statistics,
The CISO as a Systems Integrator
 The CISO as a Systems Integrator AKA: Building Your Network Defense through Bad Car Analogies and Idioms Joe McMann Cyber Strategy Leader 2017 LEIDOS. ALL RIGHTS RESERVED. 17-Leidos-0222-1662 PIRA #DIS201702005
The CISO as a Systems Integrator AKA: Building Your Network Defense through Bad Car Analogies and Idioms Joe McMann Cyber Strategy Leader 2017 LEIDOS. ALL RIGHTS RESERVED. 17-Leidos-0222-1662 PIRA #DIS201702005
JAMES GRAY SPECIAL GUEST 6/7/2017. Underwriter, London UK Specialty Treaty Beazley Group
 SPECIAL GUEST JAMES GRAY Underwriter, London UK Specialty Treaty Beazley Group All 6 Beazley Lloyd's Syndicates are rated A (Excellent) by A.M. Best Admitted Carrier in the US Beazley Ins Co rated A (Excellent)
SPECIAL GUEST JAMES GRAY Underwriter, London UK Specialty Treaty Beazley Group All 6 Beazley Lloyd's Syndicates are rated A (Excellent) by A.M. Best Admitted Carrier in the US Beazley Ins Co rated A (Excellent)
CYBER REPORT CYBER REPORT 2018
 2018 CYBER REPORT CYBER REPORT 2018 Table of Contents 1. Introduction 2 2. Technology Risk Resiliency 3 3. Cyber Underwriting 5 4. Key Statistics 6 5. Cyber Stress Scenarios 7 1. Introduction Technology
2018 CYBER REPORT CYBER REPORT 2018 Table of Contents 1. Introduction 2 2. Technology Risk Resiliency 3 3. Cyber Underwriting 5 4. Key Statistics 6 5. Cyber Stress Scenarios 7 1. Introduction Technology
At the Heart of Cyber Risk Mitigation
 At the Heart of Cyber Risk Mitigation De-risking Cyber Threats with Insurance Vikram Singh Abstract Management of risks is an integral part of the insurance industry. Companies have succeeded in identifying
At the Heart of Cyber Risk Mitigation De-risking Cyber Threats with Insurance Vikram Singh Abstract Management of risks is an integral part of the insurance industry. Companies have succeeded in identifying
DEBUNKING MYTHS FOR CYBER INSURANCE
 SESSION ID: GRC-F02 DEBUNKING MYTHS FOR CYBER INSURANCE Robert Jones Global Head of Financial Lines Specialty Claims AIG Garin Pace Cyber Product Leader AIG @Garin_Pace Introduction What Is Cyber Insurance?
SESSION ID: GRC-F02 DEBUNKING MYTHS FOR CYBER INSURANCE Robert Jones Global Head of Financial Lines Specialty Claims AIG Garin Pace Cyber Product Leader AIG @Garin_Pace Introduction What Is Cyber Insurance?
Cyber COPE. Transforming Cyber Underwriting by Russ Cohen
 Cyber COPE Transforming Cyber Underwriting by Russ Cohen Business Descriptor How tall is your office building? How close is the nearest fire hydrant? Does the building have an alarm system? Insurance companies
Cyber COPE Transforming Cyber Underwriting by Russ Cohen Business Descriptor How tall is your office building? How close is the nearest fire hydrant? Does the building have an alarm system? Insurance companies
Bank of America Merrill Lynch Future of Financials Conference 2018
 Bank of America Merrill Lynch Future of Financials Conference 2018 Jason Witty EVP, Chief Information Security Officer November 5, 2018 U.S. BANCORP Forward-looking Statements and Additional Information
Bank of America Merrill Lynch Future of Financials Conference 2018 Jason Witty EVP, Chief Information Security Officer November 5, 2018 U.S. BANCORP Forward-looking Statements and Additional Information
The Wild West Meets the Future: Key Tips for Maximizing Your Cyber and Privacy Insurance Coverage
 The Wild West Meets the Future: Key Tips for Maximizing Your Cyber and Privacy Insurance Coverage James P. Bobotek james.bobotek@pillsburylaw.com (202) 663-8930 Pillsbury Winthrop Shaw Pittman LLP DOCUMENT
The Wild West Meets the Future: Key Tips for Maximizing Your Cyber and Privacy Insurance Coverage James P. Bobotek james.bobotek@pillsburylaw.com (202) 663-8930 Pillsbury Winthrop Shaw Pittman LLP DOCUMENT
The Internet of Everything: Building Cyber Resilience in a Connected World
 The Internet of Everything: Building Cyber Resilience in a Connected World The Internet of Things (IoT) is everywhere, ushering in a technological revolution at lightning speed. According to an Oliver
The Internet of Everything: Building Cyber Resilience in a Connected World The Internet of Things (IoT) is everywhere, ushering in a technological revolution at lightning speed. According to an Oliver
Cyber-Insurance: Fraud, Waste or Abuse?
 SESSION ID: STR-F03 Cyber-Insurance: Fraud, Waste or Abuse? David Nathans Director of Security SOCSoter, Inc. @Zourick Cyber Insurance overview One Size Does Not Fit All 2 Our Research Reviewed many major
SESSION ID: STR-F03 Cyber-Insurance: Fraud, Waste or Abuse? David Nathans Director of Security SOCSoter, Inc. @Zourick Cyber Insurance overview One Size Does Not Fit All 2 Our Research Reviewed many major
2014 The Hartford Steam Boiler Inspection and Insurance Company. All rights reserved.
 1 2 3 This presentation module will give you some ideas for how to understand and communicate the value of our data security coverages to prospective members. 4 As you all know, when we use the term cyber
1 2 3 This presentation module will give you some ideas for how to understand and communicate the value of our data security coverages to prospective members. 4 As you all know, when we use the term cyber
UK 2015 Cyber Risk Survey Report
 INSIGHTS UK 2015 Cyber Risk Survey Report June 2015 CONTENTS 1 Introduction 2 Work still to be done in terms of awareness/ ownership of cyber risk 5 Lack of data continues to prevent companies from adequately
INSIGHTS UK 2015 Cyber Risk Survey Report June 2015 CONTENTS 1 Introduction 2 Work still to be done in terms of awareness/ ownership of cyber risk 5 Lack of data continues to prevent companies from adequately
Enterprise Risk Management Policy Adopted by the AMP Limited Board on 2 February 2017
 Enterprise Management Policy Adopted by the AMP Limited Board on 2 February 2017 AMP s promise is to help people own tomorrow. To achieve this promise, risks must be managed effectively within the Board
Enterprise Management Policy Adopted by the AMP Limited Board on 2 February 2017 AMP s promise is to help people own tomorrow. To achieve this promise, risks must be managed effectively within the Board
Cyber a risk on the rise. Digitalization Conference Beirut, 4 May 2017 Fabian Willi, Cyber Risk Reinsurance Specialist
 Cyber a risk on the rise Digitalization Conference Beirut, 4 May 2017 Fabian Willi, Cyber Risk Reinsurance Specialist Cyber data breaches reaching a new level 1 000 000 000 Source: http://money.cnn.com/2016/09/22/technology/yahoo-data-breach/
Cyber a risk on the rise Digitalization Conference Beirut, 4 May 2017 Fabian Willi, Cyber Risk Reinsurance Specialist Cyber data breaches reaching a new level 1 000 000 000 Source: http://money.cnn.com/2016/09/22/technology/yahoo-data-breach/
Automating Underwriting for the Small Commercial Segment
 Automating Underwriting for the Small Commercial Segment Leading Practice Overview Kelly Cusick and Dave Kuder Deloitte Consulting LLP March 11, 2015 Anti-Trust Notice The Casualty Actuarial Society is
Automating Underwriting for the Small Commercial Segment Leading Practice Overview Kelly Cusick and Dave Kuder Deloitte Consulting LLP March 11, 2015 Anti-Trust Notice The Casualty Actuarial Society is
Sara Robben, Statistical Advisor National Association of Insurance Commissioners
 Moderated by Daniel Eliot, Director Small Business Programs National Cyber Security Alliance Sara Robben, Statistical Advisor National Association of Insurance Commissioners Angela Gleason, Senior Counsel
Moderated by Daniel Eliot, Director Small Business Programs National Cyber Security Alliance Sara Robben, Statistical Advisor National Association of Insurance Commissioners Angela Gleason, Senior Counsel
An Overview of Cyber Insurance at AIG
 An Overview of Cyber Insurance at AIG Michael Lee, MBA Cyber Business Development Manager AIG 2018 Brittney Mishler, ARM Cyber Casualty Underwriting Specialist AIG Cyber Insurance It s a peril, not a product
An Overview of Cyber Insurance at AIG Michael Lee, MBA Cyber Business Development Manager AIG 2018 Brittney Mishler, ARM Cyber Casualty Underwriting Specialist AIG Cyber Insurance It s a peril, not a product
Society of Actuaries - ERM Forum, 10 May 2016 A regulatory perspective on consumer risk
 Society of Actuaries - ERM Forum, 10 May 2016 A regulatory perspective on consumer risk Helena Mitchell Head of Consumer Protection: Supervision Division Contents What is conduct risk and consumer risk?
Society of Actuaries - ERM Forum, 10 May 2016 A regulatory perspective on consumer risk Helena Mitchell Head of Consumer Protection: Supervision Division Contents What is conduct risk and consumer risk?
Protecting Against the High Cost of Cyberfraud
 Protecting Against the High Cost of Cyberfraud THE ROLE OF CYBER LIABILITY INSURANCE IN YOUR RISK MANAGEMENT STRATEGY Paying the Price...2 The Ransomware Scourge...3 Policy Provisions...3 Management Liability...4
Protecting Against the High Cost of Cyberfraud THE ROLE OF CYBER LIABILITY INSURANCE IN YOUR RISK MANAGEMENT STRATEGY Paying the Price...2 The Ransomware Scourge...3 Policy Provisions...3 Management Liability...4
This article has been published in PLI Current: The Journal of PLI Press, Vol. 2, No. 2, Spring 2018 ( 2018 Practising Law Institute),
 This article has been published in PLI Current: The Journal of PLI Press, Vol. 2, No. 2, Spring 2018 ( 2018 Practising Law Institute), www.pli.edu/plicurrent. PLI Current The Journal of PLI Press Vol.
This article has been published in PLI Current: The Journal of PLI Press, Vol. 2, No. 2, Spring 2018 ( 2018 Practising Law Institute), www.pli.edu/plicurrent. PLI Current The Journal of PLI Press Vol.
Principal risks and uncertainties
 Principal risks and uncertainties Strategic report Principal risks are a risk or a combination of risks that, given the Group s current position, could seriously affect the performance, future prospects
Principal risks and uncertainties Strategic report Principal risks are a risk or a combination of risks that, given the Group s current position, could seriously affect the performance, future prospects
Overview and context
 Michael Eves Overview and context Why Are We Talking About This Now? One facet of a long-term reaction to the financial crisis by many stakeholders: Increasing knowledge of models Decreasing confidence
Michael Eves Overview and context Why Are We Talking About This Now? One facet of a long-term reaction to the financial crisis by many stakeholders: Increasing knowledge of models Decreasing confidence
Break the Risk Paradigms - Overhauling Your Risk Program
 SESSION ID: GRC-T11 Break the Risk Paradigms - Overhauling Your Risk Program Evan Wheeler MUFG Union Bank Director, Information Risk Management Your boss asks you to identify the top risks for your organization
SESSION ID: GRC-T11 Break the Risk Paradigms - Overhauling Your Risk Program Evan Wheeler MUFG Union Bank Director, Information Risk Management Your boss asks you to identify the top risks for your organization
Cyber Risks & Insurance
 Cyber Risks & Insurance Bob Klobe Asst. Vice President & Cyber Security Subject Matter Expert Chubb Specialty Insurance Legal Disclaimer The views, information and content expressed herein are those of
Cyber Risks & Insurance Bob Klobe Asst. Vice President & Cyber Security Subject Matter Expert Chubb Specialty Insurance Legal Disclaimer The views, information and content expressed herein are those of
ENTERPRISE RISK MANAGEMENT (ERM) The Conceptual Framework
 ENTERPRISE RISK MANAGEMENT (ERM) The Conceptual Framework ENTERPRISE RISK MANAGEMENT (ERM) ERM Definition The Conceptual Frameworks: CAS and COSO Risk Categories Implementing ERM Why ERM? ERM Maturity
ENTERPRISE RISK MANAGEMENT (ERM) The Conceptual Framework ENTERPRISE RISK MANAGEMENT (ERM) ERM Definition The Conceptual Frameworks: CAS and COSO Risk Categories Implementing ERM Why ERM? ERM Maturity
Advent Direct. Harnessing the power of technology for data management. Tackling the global challenges of fund regulations
 October 2013 Advent Direct Harnessing the power of technology for data management Tackling the global challenges of fund regulations Integrated framework for data processing One-stop workflow solution
October 2013 Advent Direct Harnessing the power of technology for data management Tackling the global challenges of fund regulations Integrated framework for data processing One-stop workflow solution
2016 Risk Practices Survey
 Strong Board. Strong Bank. 2016 Risk Practices Survey MAR 2016 RESEARCH Sponsored by: 2 2016 RISK PRACTICES SURVEY TABLE OF CONTENTS Executive Summary 3 Risk Governance & Oversight 4 Risk Culture & Infrastructure
Strong Board. Strong Bank. 2016 Risk Practices Survey MAR 2016 RESEARCH Sponsored by: 2 2016 RISK PRACTICES SURVEY TABLE OF CONTENTS Executive Summary 3 Risk Governance & Oversight 4 Risk Culture & Infrastructure
EMERGING INSURANCE RISKS. Presented by Lawrence Njore Apex Reinsurance Brokers- Nairobi- Kenya
 EMERGING INSURANCE RISKS Presented by Lawrence Njore Apex Reinsurance Brokers- Nairobi- Kenya EMERGING RISK DEFINITIONS Lloyds: An issue that is perceived to be potentially significant but which may not
EMERGING INSURANCE RISKS Presented by Lawrence Njore Apex Reinsurance Brokers- Nairobi- Kenya EMERGING RISK DEFINITIONS Lloyds: An issue that is perceived to be potentially significant but which may not
Financial Industry Developments
 2016 INVESTMENT MANAGEMENT CONFERENCE Financial Industry Developments Nicholas S. Hodge, Partner, Boston Michael W. McGrath, Partner, Boston Copyright 2016 by K&L Gates LLP. All rights reserved. Hedge
2016 INVESTMENT MANAGEMENT CONFERENCE Financial Industry Developments Nicholas S. Hodge, Partner, Boston Michael W. McGrath, Partner, Boston Copyright 2016 by K&L Gates LLP. All rights reserved. Hedge
Post-Class Quiz: Information Security and Risk Management Domain
 1. Which choice below is the role of an Information System Security Officer (ISSO)? A. The ISSO establishes the overall goals of the organization s computer security program. B. The ISSO is responsible
1. Which choice below is the role of an Information System Security Officer (ISSO)? A. The ISSO establishes the overall goals of the organization s computer security program. B. The ISSO is responsible
Defining a Risk Appetite That Works
 SESSION ID: CXO-W10 Defining a Risk Appetite That Works Jack Jones Chairman - FAIR Institute What we ll cover Appetite vs. tolerance what s the diff? Why bother? Comparing risk appetite definitions An
SESSION ID: CXO-W10 Defining a Risk Appetite That Works Jack Jones Chairman - FAIR Institute What we ll cover Appetite vs. tolerance what s the diff? Why bother? Comparing risk appetite definitions An
Cybersecurity Privacy and Network Security and Risk Mitigation
 Ask the Experts at fi360 2016 Cybersecurity Privacy and Network Security and Risk Mitigation Gary Sutherland, NAPLIA CEO Brian Edelman, Financial Computer Inc. CEO Paul Smith, AIF NAPLIA SVP SEC s 1st
Ask the Experts at fi360 2016 Cybersecurity Privacy and Network Security and Risk Mitigation Gary Sutherland, NAPLIA CEO Brian Edelman, Financial Computer Inc. CEO Paul Smith, AIF NAPLIA SVP SEC s 1st
Beazley Financial Institutions
 Market leading protection tailored for financial institutions, providing seamless cover from crime and professional indemnity to directors & officers and data breach. 0 1 0 0 1 1 0 0 0 1 1 0 Beazley Financial
Market leading protection tailored for financial institutions, providing seamless cover from crime and professional indemnity to directors & officers and data breach. 0 1 0 0 1 1 0 0 0 1 1 0 Beazley Financial
market opportunity line fair odds line Example 6.6, p. 120.
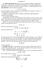 September 5 The market opportunity line depicts in the plane the different combinations of outcomes and that are available to the individual at the prevailing market prices, depending on how much of an
September 5 The market opportunity line depicts in the plane the different combinations of outcomes and that are available to the individual at the prevailing market prices, depending on how much of an
Ball State University
 PCI Data Security Awareness Training Agenda What is PCI-DSS PCI-DDS Standards Training Definitions Compliance 6 Goals 12 Security Requirements Card Identification Basic Rules to Follow Myths 1 What is
PCI Data Security Awareness Training Agenda What is PCI-DSS PCI-DDS Standards Training Definitions Compliance 6 Goals 12 Security Requirements Card Identification Basic Rules to Follow Myths 1 What is
Data breaches only or disproportionately affect retail merchants.
 October 30, 2014 Mr. Jim Nussle Credit Union National Association 601 Pennsylvania Ave NW, South Bldg. Washington DC 20004 Mr. Dan Berger National Association of Federal Credit Unions 3138 10 th Street
October 30, 2014 Mr. Jim Nussle Credit Union National Association 601 Pennsylvania Ave NW, South Bldg. Washington DC 20004 Mr. Dan Berger National Association of Federal Credit Unions 3138 10 th Street
Aon Cyber Risk and Directors & Officers Forum CRM011
 Aon Cyber Risk and Directors & Officers Forum CRM011 Speakers: Leslie Lamb, Director, Global Risk & Resiliency Management, Cisco Systems Timothy Fletcher, Senior Vice President and Team Leader, Aon Risk
Aon Cyber Risk and Directors & Officers Forum CRM011 Speakers: Leslie Lamb, Director, Global Risk & Resiliency Management, Cisco Systems Timothy Fletcher, Senior Vice President and Team Leader, Aon Risk
Cyber Security & Insurance Solution Karachi, Pakistan
 March 2017 Cyber Security & Insurance Solution Karachi, Pakistan Ram Garg CFA, MBA Financial & Casualty Line J B Boda & Co (Singapore) Pte Ltd Karachi Insurance Institute Agenda Cyber Risk - Background
March 2017 Cyber Security & Insurance Solution Karachi, Pakistan Ram Garg CFA, MBA Financial & Casualty Line J B Boda & Co (Singapore) Pte Ltd Karachi Insurance Institute Agenda Cyber Risk - Background
SUGGESTED SOLUTION FINAL MAY 2019 EXAM. Test Code - FNJ 7081
 SUGGESTED SOLUTION FINAL MAY 2019 EXAM SUBJECT- SCM & PE Test Code - FNJ 7081 BRANCH - () (Date :) Head Office : Shraddha, 3 rd Floor, Near Chinai College, Andheri (E), Mumbai 69. Tel : (022) 26836666
SUGGESTED SOLUTION FINAL MAY 2019 EXAM SUBJECT- SCM & PE Test Code - FNJ 7081 BRANCH - () (Date :) Head Office : Shraddha, 3 rd Floor, Near Chinai College, Andheri (E), Mumbai 69. Tel : (022) 26836666
INSURING CYBER RISKS WITH A CAPTIVE: IS IT WORTH IT?
 CAPSTONE ASSOCIATED SERVICES, LTD Two Post Oak Central 1980 Post Oak Blvd., Suite 1950 Houston, TX 77056. USA Telephone: 713.800.0550 Toll-Free: 1.800.705.4014 Fax: 713.623.0329 Website: www.capstoneassociated.com
CAPSTONE ASSOCIATED SERVICES, LTD Two Post Oak Central 1980 Post Oak Blvd., Suite 1950 Houston, TX 77056. USA Telephone: 713.800.0550 Toll-Free: 1.800.705.4014 Fax: 713.623.0329 Website: www.capstoneassociated.com
Cyber insurance: The next frontier. Cyber insurance the next frontier
 Cyber insurance the next frontier 1 Table of contents Summary 3 The Market Need 3 Cyber Risk: A Growing Concern 4 Rising Cost of Cyber Crime 5 Impact by Industry 6 Cyber Risk and Insurance 7 Cyber Risk
Cyber insurance the next frontier 1 Table of contents Summary 3 The Market Need 3 Cyber Risk: A Growing Concern 4 Rising Cost of Cyber Crime 5 Impact by Industry 6 Cyber Risk and Insurance 7 Cyber Risk
CYBER SECURITY SURVEY Business Software Alliance JUNE 5-7, 2002
 Interviews: 395 IT professionals Margin of error: +5.0 Interview dates: Ipsos Public Affairs 1101 Connecticut Avenue NW, Suite 200 Washington, DC 20036 (202) 463-7300 CYBER SECURITY SURVEY Business Software
Interviews: 395 IT professionals Margin of error: +5.0 Interview dates: Ipsos Public Affairs 1101 Connecticut Avenue NW, Suite 200 Washington, DC 20036 (202) 463-7300 CYBER SECURITY SURVEY Business Software
Moderator: Ann Weber, JD. Presenters: Dan Adamson Angela Nelson
 Session 103 PD - Use of Artificial Intelligence in GI: Industry Opportunities and Regulatory Challenges Moderator: Ann Weber, JD Presenters: Dan Adamson Angela Nelson SOA Antitrust Compliance Guidelines
Session 103 PD - Use of Artificial Intelligence in GI: Industry Opportunities and Regulatory Challenges Moderator: Ann Weber, JD Presenters: Dan Adamson Angela Nelson SOA Antitrust Compliance Guidelines
Cybersecurity Threats: What Retirement Plan Sponsors and Fiduciaries Need to Know and Do
 ARTICLE Cybersecurity Threats: What Retirement Plan Sponsors and Fiduciaries Need to Know and Do By Gene Griggs and Saad Gul This article analyzes cybersecurity issues for retirement plans. Introduction
ARTICLE Cybersecurity Threats: What Retirement Plan Sponsors and Fiduciaries Need to Know and Do By Gene Griggs and Saad Gul This article analyzes cybersecurity issues for retirement plans. Introduction
Launching a Hedge Fund: 10 Keys to Success. from marketing to technology, the top tips for achieving startup success
 Launching a Hedge Fund: 10 Keys to Success from marketing to technology, the top tips for achieving startup success It may be a dream for most, but the desire to start a hedge fund is a real one for many
Launching a Hedge Fund: 10 Keys to Success from marketing to technology, the top tips for achieving startup success It may be a dream for most, but the desire to start a hedge fund is a real one for many
SURVEY OF GOVERNMENT CONTRACTOR SALES EXPECTATIONS
 SURVEY OF GOVERNMENT CONTRACTOR SALES EXPECTATIONS 2017-18 Executive Summary... 03 Introduction... 05 Profile of Government Contractors Surveyed... 06 TABLE OF CONTENTS Onvia Government Contractor Confidence
SURVEY OF GOVERNMENT CONTRACTOR SALES EXPECTATIONS 2017-18 Executive Summary... 03 Introduction... 05 Profile of Government Contractors Surveyed... 06 TABLE OF CONTENTS Onvia Government Contractor Confidence
Cyber Risk Pool. 21 February
 21 February 2017-1 - Europe Economics is registered in England No. 3477100. Registered offices at Chancery House, 53-64 Chancery Lane, London WC2A 1QU. Whilst every effort has been made to ensure the accuracy
21 February 2017-1 - Europe Economics is registered in England No. 3477100. Registered offices at Chancery House, 53-64 Chancery Lane, London WC2A 1QU. Whilst every effort has been made to ensure the accuracy
Q: What is PCI? Q: To whom does PCI apply? Q: Where can I find the PCI Data Security Standards (PCI DSS)? Q: What are the PCI compliance deadlines?
 Q: What is PCI? A: The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that ALL companies that process, store or transmit credit card information maintain
Q: What is PCI? A: The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that ALL companies that process, store or transmit credit card information maintain
Your Risk Management Toolkit. Kevin Larson, Chief Compliance Officer, Cetera Investment Services
 Your Risk Management Toolkit Kevin Larson, Chief Compliance Officer, Cetera Investment Services Agenda Recap of Enforcement Actions FINRA Exam Priorities Banking Priorities How Best to Protect Your Financial
Your Risk Management Toolkit Kevin Larson, Chief Compliance Officer, Cetera Investment Services Agenda Recap of Enforcement Actions FINRA Exam Priorities Banking Priorities How Best to Protect Your Financial
AUTOMATE MORTGAGE BROKER COMPENSATION
 HOW SALES COMMISSION SOFTWARE HELPS AUTOMATE MORTGAGE BROKER COMPENSATION Automate Mortgage Broker Compensation 01 Contents 02 03 06 07 08 Introduction Incentive Software Eliminates Spreadsheet Complexity
HOW SALES COMMISSION SOFTWARE HELPS AUTOMATE MORTGAGE BROKER COMPENSATION Automate Mortgage Broker Compensation 01 Contents 02 03 06 07 08 Introduction Incentive Software Eliminates Spreadsheet Complexity
Modeling Extreme Event Risk
 Modeling Extreme Event Risk Both natural catastrophes earthquakes, hurricanes, tornadoes, and floods and man-made disasters, including terrorism and extreme casualty events, can jeopardize the financial
Modeling Extreme Event Risk Both natural catastrophes earthquakes, hurricanes, tornadoes, and floods and man-made disasters, including terrorism and extreme casualty events, can jeopardize the financial
Certified Enterprise Risk Professional (CERP) Test Content Outline
 Certified Enterprise Risk Professional (CERP) Test Content Outline SECTION 1: RISK GOVERNANCE Domain 1: Board and Senior Management Oversight (8%) Task 1: Provide relevant, timely, and accurate information
Certified Enterprise Risk Professional (CERP) Test Content Outline SECTION 1: RISK GOVERNANCE Domain 1: Board and Senior Management Oversight (8%) Task 1: Provide relevant, timely, and accurate information
Lloyd s City Risk Index
 Lloyd s City Risk Index 2015-2025 lloyds.com/cityriskindex Executive Summary About Lloyd s Lloyd s is the world s only specialist insurance and reinsurance market that offers a unique concentration of
Lloyd s City Risk Index 2015-2025 lloyds.com/cityriskindex Executive Summary About Lloyd s Lloyd s is the world s only specialist insurance and reinsurance market that offers a unique concentration of
Regulatory Hot Issues
 www.pwchk.com Regulatory Hot Issues March 2018 Welcome to our first edition of Regulatory Hot Issues, which will provide an overview of key regulatory issues and challenges that financial institutions
www.pwchk.com Regulatory Hot Issues March 2018 Welcome to our first edition of Regulatory Hot Issues, which will provide an overview of key regulatory issues and challenges that financial institutions
Small Business Lending Landscape
 Small Business Lending Landscape Opportunity Finance Network June 8, 2016 Agenda Small Business Financing Initiative Overview Today s Topic and Presenters Small Business Lending Landscape How can mission-driven
Small Business Lending Landscape Opportunity Finance Network June 8, 2016 Agenda Small Business Financing Initiative Overview Today s Topic and Presenters Small Business Lending Landscape How can mission-driven
Taking the stress out of operational-risk stress testing
 Saptarshi Ganguly and Daniel Mikkelsen Taking the stress out of operational-risk stress testing Risk Management December 2015 Financial institutions are facing heightened supervisory scrutiny, but those
Saptarshi Ganguly and Daniel Mikkelsen Taking the stress out of operational-risk stress testing Risk Management December 2015 Financial institutions are facing heightened supervisory scrutiny, but those
Administration and Department Credit Card Policy
 Administration and Department Credit Card Policy Updated February 29, 2016 CONTENTS Purpose PCI DSS Scope/Applicability Authority Securing Credit Card Data Policy Glossary Page 2 of 5 PURPOSE As a department
Administration and Department Credit Card Policy Updated February 29, 2016 CONTENTS Purpose PCI DSS Scope/Applicability Authority Securing Credit Card Data Policy Glossary Page 2 of 5 PURPOSE As a department
IBM Financial Crimes Insight for Insurance
 IBM Financial Crimes Insight for Insurance Highlights Improve outcomes and reduce cost of counterfraud efforts Optimize assets for efficient and effective fraud management Quickly distinguish fraudsters
IBM Financial Crimes Insight for Insurance Highlights Improve outcomes and reduce cost of counterfraud efforts Optimize assets for efficient and effective fraud management Quickly distinguish fraudsters
HEALTHCARE INDUSTRY SESSION CYBER IND 011
 HEALTHCARE INDUSTRY SESSION CYBER IND 011 Speakers: Jody Westby, Chief Executive Officer, Global Cyber Risk René Siemens, Partner, Covington & Burling LLP Brent Rieth, Senior Vice President and Team Leader,
HEALTHCARE INDUSTRY SESSION CYBER IND 011 Speakers: Jody Westby, Chief Executive Officer, Global Cyber Risk René Siemens, Partner, Covington & Burling LLP Brent Rieth, Senior Vice President and Team Leader,
Insuring your online world, even when you re offline. Masterpiece Cyber Protection
 Insuring your online world, even when you re offline Masterpiece Cyber Protection Protect your online information from being an open network 97% of Chubb clients who had a claim paid were highly satisfied
Insuring your online world, even when you re offline Masterpiece Cyber Protection Protect your online information from being an open network 97% of Chubb clients who had a claim paid were highly satisfied
Lloyd s Asia. Underwriting human progress
 Lloyd s Asia Underwriting human progress What is Lloyd s? Lloyd s is the world s specialist insurance and reinsurance market. With expertise earned over centuries, Lloyd s is the foundation of the insurance
Lloyd s Asia Underwriting human progress What is Lloyd s? Lloyd s is the world s specialist insurance and reinsurance market. With expertise earned over centuries, Lloyd s is the foundation of the insurance
Crossing the Breach. It won t happen to us
 Crossing the Breach P R O T E C T I N G F R O M D ATA B R E A C H E S I S M O R E T H A N A N I. T. I S S U E WHITE PA P E R V E S T I G E D I G I TA L I N V E S T I G AT I O N S Crossing the Breach It
Crossing the Breach P R O T E C T I N G F R O M D ATA B R E A C H E S I S M O R E T H A N A N I. T. I S S U E WHITE PA P E R V E S T I G E D I G I TA L I N V E S T I G AT I O N S Crossing the Breach It
MTPredictor Trade Module for NinjaTrader 7 (v1.1) Getting Started Guide
 MTPredictor Trade Module for NinjaTrader 7 (v1.1) Getting Started Guide Introduction The MTPredictor Trade Module for NinjaTrader 7 is a new extension to the MTPredictor Add-on s for NinjaTrader 7 designed
MTPredictor Trade Module for NinjaTrader 7 (v1.1) Getting Started Guide Introduction The MTPredictor Trade Module for NinjaTrader 7 is a new extension to the MTPredictor Add-on s for NinjaTrader 7 designed
Cisco Insurance Whitepaper Fall 2016
 White Paper Cisco Insurance Whitepaper Fall 2016 Technology Helps Insurers Unleash the Possibilities of Digitization It s no secret that InsureTech investment is on the rise. According to the Pulse of
White Paper Cisco Insurance Whitepaper Fall 2016 Technology Helps Insurers Unleash the Possibilities of Digitization It s no secret that InsureTech investment is on the rise. According to the Pulse of
How we manage risk. Risk philosophy. Risk policy. Risk framework
 How we manage risk Risk management is integral to the daily operations of our businesses. As a multinational group with activities in over 130 countries, Naspers is exposed to a wide range of risks that
How we manage risk Risk management is integral to the daily operations of our businesses. As a multinational group with activities in over 130 countries, Naspers is exposed to a wide range of risks that
Structured ScenarioS
 Structured ScenarioS A pilot experiment on peer structured scenario assessment Yao, Jane, American Bankers Association, JYao@aba.com Condamin, Laurent, Mstar, laurent.condamin@elseware.fr Naim, Patrick,
Structured ScenarioS A pilot experiment on peer structured scenario assessment Yao, Jane, American Bankers Association, JYao@aba.com Condamin, Laurent, Mstar, laurent.condamin@elseware.fr Naim, Patrick,
Why CISOs Should Embrace Their Cyber Insurer
 6 Steps to Start Working Together Today Cyber Security risk management is undergoing one of the most important shifts in recent memory; however, this shift is not being driven by the information security
6 Steps to Start Working Together Today Cyber Security risk management is undergoing one of the most important shifts in recent memory; however, this shift is not being driven by the information security
Lloyd s Asia. Underwriting human progress. Lloyds Global Brochure - ASIA_154x233_V6.indd 1 22/08/ :51
 Lloyd s Asia Underwriting human progress Lloyds Global Brochure - ASIA_154x233_V6.indd 1 22/08/2016 10:51 What is Lloyd s? Lloyd s is the world s specialist insurance and reinsurance market. With expertise
Lloyd s Asia Underwriting human progress Lloyds Global Brochure - ASIA_154x233_V6.indd 1 22/08/2016 10:51 What is Lloyd s? Lloyd s is the world s specialist insurance and reinsurance market. With expertise
TONGA NATIONAL QUALIFICATIONS AND ACCREDITATION BOARD
 TONGA NATIONAL QUALIFICATIONS AND ACCREDITATION BOARD RISK MANAGEMENT FRAMEWORK 2017 Overview Tonga National Qualifications and Accreditation Board (TNQAB) was established in 2004, after the Tonga National
TONGA NATIONAL QUALIFICATIONS AND ACCREDITATION BOARD RISK MANAGEMENT FRAMEWORK 2017 Overview Tonga National Qualifications and Accreditation Board (TNQAB) was established in 2004, after the Tonga National
PCI security standards: A high-level overview
 PCI security standards: A high-level overview Prepared by: Joel Dubin, Manager, RSM US LLP joel.dubin@rsmus.com, +1 312 634 3422 Many merchants often have difficulty understanding how they must comply
PCI security standards: A high-level overview Prepared by: Joel Dubin, Manager, RSM US LLP joel.dubin@rsmus.com, +1 312 634 3422 Many merchants often have difficulty understanding how they must comply
PRIVACY AND CYBER SECURITY
 PRIVACY AND CYBER SECURITY Presented by: Joe Marra, Senior Account Executive/Producer Stoya Corcoran, Assistant Vice President Presented to: CIFFA Members September 20, 2017 1 Disclaimer The information
PRIVACY AND CYBER SECURITY Presented by: Joe Marra, Senior Account Executive/Producer Stoya Corcoran, Assistant Vice President Presented to: CIFFA Members September 20, 2017 1 Disclaimer The information
THE PROBLEM THERE IS AN INFORMATION CRISIS IN CONSUMER FINANCE LATIKA. Emilian. Alternative online lender without enough data
 THE PROBLEM THERE IS AN INFORMATION CRISIS IN CONSUMER FINANCE NEEDS A LOAN WANTS TO LEND LATIKA Small business owner in India Emilian Alternative online lender without enough data INTRODUCTION WHAT IS
THE PROBLEM THERE IS AN INFORMATION CRISIS IN CONSUMER FINANCE NEEDS A LOAN WANTS TO LEND LATIKA Small business owner in India Emilian Alternative online lender without enough data INTRODUCTION WHAT IS
2018 Small Business Risk Report
 2018 Small Business Risk Report Key findings The 2018 Small Business Risk Report reveals that while small business owners are aware they face multiple risks and growing concerns, they often are not spending
2018 Small Business Risk Report Key findings The 2018 Small Business Risk Report reveals that while small business owners are aware they face multiple risks and growing concerns, they often are not spending
Strategic Security Management: Risk Assessments in the Environment of Care. Karim H. Vellani, CPP, CSC
 Strategic Security Management: Risk Assessments in the Environment of Care Karim H. Vellani, CPP, CSC Securing the environment of care is a challenging and continual effort for most healthcare security
Strategic Security Management: Risk Assessments in the Environment of Care Karim H. Vellani, CPP, CSC Securing the environment of care is a challenging and continual effort for most healthcare security
Auckland Transport Alignment Project. Revenue and Expenditure Report
 Auckland Transport Alignment Project Revenue and Expenditure Report Contents 1. Introduction... 3 2. Approach... 3 3. Expenditure... 5 3.1. Historic transport expenditure 2001-2015... 5 3.2. Expenditure
Auckland Transport Alignment Project Revenue and Expenditure Report Contents 1. Introduction... 3 2. Approach... 3 3. Expenditure... 5 3.1. Historic transport expenditure 2001-2015... 5 3.2. Expenditure
Principles of Risk Management and Insurance, 13e (Rejda/McNamara) Chapter 2 Insurance and Risk
 Principles of Risk Management and Insurance, 13e (Rejda/McNamara) Chapter 2 Insurance and Risk 1) Which of the following is a basic characteristic of insurance? A) pooling of losses B) avoidance of risk
Principles of Risk Management and Insurance, 13e (Rejda/McNamara) Chapter 2 Insurance and Risk 1) Which of the following is a basic characteristic of insurance? A) pooling of losses B) avoidance of risk
Key Themes. Organizational Dynamics and Effective Risk Management. Organizational Alignment. Risk Management Effectiveness
 Key Themes Organizational Alignment Risk Management Effectiveness Organizational Dynamics and Effective Risk Management Data, Analytics, and Technology Building a Cyber Risk Framework 1 Organization: Where
Key Themes Organizational Alignment Risk Management Effectiveness Organizational Dynamics and Effective Risk Management Data, Analytics, and Technology Building a Cyber Risk Framework 1 Organization: Where
Predicting and Preventing Credit Card Default
 Predicting and Preventing Credit Card Default Project Plan MS-E2177: Seminar on Case Studies in Operations Research Client: McKinsey Finland Ari Viitala Max Merikoski (Project Manager) Nourhan Shafik 21.2.2018
Predicting and Preventing Credit Card Default Project Plan MS-E2177: Seminar on Case Studies in Operations Research Client: McKinsey Finland Ari Viitala Max Merikoski (Project Manager) Nourhan Shafik 21.2.2018
